Communication lies at the heart of every successful system, allowing for seamless interaction and the exchange of valuable information. In the digital realm, the development of effective network protocols has become a paramount focus, ensuring efficient data transmission and secure connections. This comprehensive guide delves into the intricacies of Windows network protocol creation and management, shedding light on the evolutionary journey that has shaped modern communication tools.
Throughout the years, the Windows operating system has witnessed a remarkable evolution in its network communication capabilities, with a constant drive towards optimization and innovation. This exploration aims to uncover the underlying principles and techniques employed to establish reliable network connections, while exploring the transformative impact they have had on our digital landscape.
By delving into the fundamentals of network protocol development, this guide will unpack the intricate mechanisms that govern data transmission, from the initial handshake to the establishment of secure channels. From the humble beginnings of basic protocols to the sophisticated frameworks of today, we will uncover the inner workings of communication protocols that have shaped modern computing.
The fascinating journey of Windows network protocol creation and management encompasses not only the technical aspects but also the human ingenuity and collaborative efforts that have driven its advancement. By understanding the foundations and intricacies of network communication, both new and seasoned professionals can acquire the knowledge needed to navigate through the complexities of modern networks with confidence and efficiency.
Understanding the Fundamentals of Windows Network Protocol Landscape
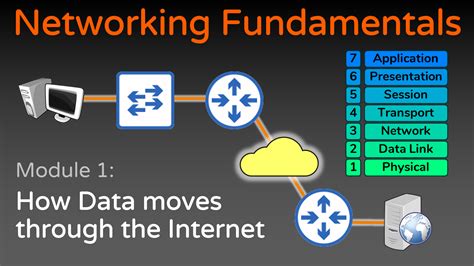
In this section, we will explore the essential concepts and components that form the foundation of the vibrant ecosystem of communication protocols within the Windows operating system. We will delve into the intricacies of the networking landscape to gain a deep understanding of how data flows seamlessly across devices, enabling efficient and secure communication.
Throughout this exploration, we will analyze the fundamental principles and mechanisms that underpin the functioning of diverse protocols employed in the Windows ecosystem. By grasping these underlying principles, readers will acquire the knowledge necessary to make informed decisions when it comes to selecting, configuring, and managing network protocols.
Moreover, we will examine the crucial role that network protocols play in establishing reliable connections, facilitating data exchange, and ensuring data integrity. Understanding the diverse protocols available and their specific use cases will empower network administrators and system architects to design robust and efficient network infrastructures tailored to the unique needs of their organizations.
By delving into the intricate world of network protocols, this section aims to equip readers with a solid understanding of the foundations of Windows networking. Through comprehensive insights into these essential components, readers will be better equipped to enhance the performance, security, and reliability of their network environments.
The Significance of Effective Development and Administration of Network Protocols
As organizations strive to optimize their systems and enhance communication and data exchange, the creation and management of network protocols play a pivotal role in ensuring seamless operations. The proper implementation of protocols guarantees efficient transmission, customization, and interpretation of information between network devices, fostering secure and reliable connections. This section delves into the importance of proficient protocol development and administration, highlighting the key benefits it brings to the overall network infrastructure.
Key Components of the Windows Network Protocol Stack
The Windows Network Protocol Stack comprises essential components that facilitate communication within a network infrastructure. Understanding these key components is crucial for managing and troubleshooting network connectivity and performance issues.
- Transport Layer: The transport layer is responsible for facilitating reliable data transmission between network endpoints. It establishes connections, breaks down data into manageable chunks, and handles error detection and correction.
- Network Layer: The network layer deals with addressing and routing of data packets across different networks. It ensures that data reaches its intended destination by selecting the most efficient path and interpreting IP addresses.
- Data Link Layer: The data link layer provides error-free transmission of data frames between adjacent network nodes. It establishes and terminates logical connections, ensures data integrity through error checking, and uses MAC addresses to identify devices on a local network.
- Physical Layer: The physical layer is responsible for transmitting raw bit stream over physical media, such as Ethernet cables or wireless signals. It defines protocols for electrical, optical, or wireless transmission, ensuring the integrity and synchronization of data on the physical layer.
- Network Interface Card (NIC): The NIC is a hardware component that interfaces between a computer's network adapter and the network. It converts data between the computer and the network, enables communication using the protocols defined by the network stack, and handles tasks such as addressing, encryption, and packet encapsulation.
- Network Protocols: Network protocols are a set of rules and procedures that govern communication between devices in a network. They define standards for data exchange, addressing, routing, and error handling. Examples of network protocols include TCP/IP, UDP, ICMP, and ARP.
By understanding these key components of the Windows Network Protocol Stack, network administrators can effectively diagnose and resolve network issues, optimize performance, and ensure seamless communication within their network infrastructure.
Configuring and Troubleshooting Windows Network Protocols
In this section, we will explore the process of configuring and resolving issues related to the communication protocols used in the Windows operating system. We will delve into the intricacies of fine-tuning and troubleshooting network protocols to ensure seamless data exchange between devices, without relying on their brand names, system components, or management guides. By understanding the underlying principles and employing effective strategies, we can optimize the performance and resolve any hiccups that may arise during network protocol configuration.
1. Configuring Network Protocols
When it comes to configuring network protocols, it is essential to have a clear understanding of the various options and parameters available. This section will guide you through the process of customizing network protocol settings, providing a comprehensive overview of the different levels of configuration, from basic to advanced. By having control over protocol configurations, you can tailor the network communication to suit your specific requirements, enhancing efficiency, security, and compatibility.
1.1 Protocol Selection and Prioritization
- Understanding the different network protocols available and their distinct functionalities.
- Exploring strategies for selecting and prioritizing protocols based on specific network requirements.
- Tips for customizing protocol settings to optimize network performance.
1.2 Fine-tuning Protocol Parameters
- Examining the various parameters that can be adjusted to optimize protocol behavior.
- Best practices for modifying protocol settings to enhance network performance.
- Understanding the impact of protocol modifications on security and compatibility.
2. Troubleshooting Network Protocols
When network communication faces interruptions or errors, it is crucial to have troubleshooting skills to identify and resolve protocol-related issues promptly. This section will equip you with a range of techniques and strategies to diagnose and resolve common problems that can arise in Windows network protocols.
2.1 Identifying Protocol-related Issues
- Recognizing symptoms and indicators of potential protocol-related problems.
- Effective methods for identifying the root cause of protocol issues.
- Using diagnostic tools and techniques to gather relevant information for troubleshooting.
2.2 Resolving Protocol Issues
- Step-by-step approach to troubleshooting and resolving protocol-related problems.
- Common techniques for resolving connectivity, performance, and compatibility issues.
- Addressing security concerns and mitigating potential protocol vulnerabilities.
By mastering the art of configuring and troubleshooting Windows network protocols, you can ensure reliable and efficient communication within your network environment. With the knowledge and skills gained from this section, you will be well-equipped to overcome any challenges and maintain a robust and secure network infrastructure.
Effective Strategies for Designing Efficient Windows Network Protocols
In this section, we will explore the best practices for designing highly efficient network protocols in the Windows environment. By optimizing the design of these protocols, you can enhance network performance, reduce latency, and improve overall network efficiency. This guide will provide you with key insights and strategies to ensure your Windows network protocols are fast, reliable, and scalable.
- 1. Minimize Protocol Overhead: One crucial aspect of efficient protocol design is minimizing unnecessary overhead. By reducing packet size, limiting the number of round trips, and optimizing data representation, you can significantly improve the efficiency of your network protocols.
- 2. Prioritize Packet Transmission: As every network administrator knows, not all packets are equal. To ensure efficient network communication, it is essential to prioritize critical data packets, such as real-time video and voice, over less time-sensitive traffic. This can be achieved through intelligent packet queuing, Quality of Service (QoS) techniques, and effective traffic shaping mechanisms.
- 3. Implement Error Handling Mechanisms: Robust error handling is crucial for efficient network protocol design. By implementing reliable error detection and correction mechanisms, you can minimize the impact of packet loss and latency issues. Techniques such as checksums, acknowledgments, and retransmission strategies can significantly improve the overall performance of your Windows network protocols.
- 4. Optimize Bandwidth Utilization: Efficiently utilizing available network bandwidth can help maximize performance and reduce wastage. This can be achieved through techniques such as compression, traffic prioritization, aggregation of data packets, and leveraging multicast or broadcast capabilities when appropriate.
- 5. Consider Scalability and Extensibility: Designing network protocols with scalability and extensibility in mind is essential for future-proofing your network infrastructure. By incorporating flexible architectures and well-defined interfaces, you can accommodate future growth, support new features, and facilitate seamless integration with other protocols or systems.
By following these best practices, you can create efficient Windows network protocols that optimize performance, enhance user experience, and support the evolving needs of your network infrastructure. With a focus on minimizing overhead, prioritizing packets, implementing error handling mechanisms, optimizing bandwidth utilization, and considering scalability, your protocols will provide a solid foundation for efficient communication within your Windows network environment.
Security Considerations in the Management of Network Protocols on the Windows Platform
When it comes to overseeing the operation of network protocols on the Windows platform, taking into account security considerations is of utmost importance. As the use of network protocols becomes increasingly prevalent in modern computing environments, ensuring the protection and integrity of these protocols is crucial for maintaining a secure network infrastructure.
One of the primary concerns in managing network protocols is safeguarding against potential vulnerabilities and attacks. Network protocols can be targeted by malicious actors who exploit weaknesses in the protocol implementations to gain unauthorized access or disrupt network communications. It is imperative for network administrators and system managers to stay abreast of the latest security threats and vulnerabilities, as well as utilize robust security measures to mitigate these risks.
- Secure Configuration: Configuring network protocols with secure settings is an essential step in reducing the risk of unauthorized access. This involves enabling appropriate encryption, authentication, and access control mechanisms to protect sensitive data transmission and ensure the authenticity of network communications.
- Access Control: Implementing effective access controls is crucial in managing network protocols. This includes defining and enforcing permissions and privileges for users and devices interacting with the protocols. By limiting access to authorized individuals or entities, the potential for unauthorized manipulation or misuse of protocols is significantly reduced.
- Regular Monitoring and Auditing: Continuously monitoring network protocols and auditing their activity provides valuable insights into potential security breaches or suspicious activities. By analyzing protocol logs and network traffic, it becomes possible to detect and respond promptly to any signs of unauthorized access or abnormal behavior, thereby strengthening overall network security.
- Software Updates and Patch Management: Keeping network protocols up to date with the latest patches and software updates is crucial for addressing known security vulnerabilities. Regularly applying patches and updates ensures that any potential weaknesses or flaws in the protocol implementations are promptly addressed, reducing the risk of exploitation by attackers.
- Security Awareness and Training: Proper education and training of network administrators and users regarding security best practices are essential in minimizing the risks associated with network protocol management. By raising awareness of potential threats and providing guidance on secure protocol usage, organizations can foster a culture of security and empower individuals to actively contribute to the protection of the network infrastructure.
In conclusion, the effective management of network protocols on the Windows platform necessitates a strong focus on security considerations. By following best practices such as configuring protocols securely, implementing access controls, regularly monitoring and auditing protocol activity, applying software updates and patches, and promoting security awareness and training, organizations can enhance the overall security posture of their network infrastructure.
Exploring the Incorporation of Third-Party Network Protocols into Windows Environment
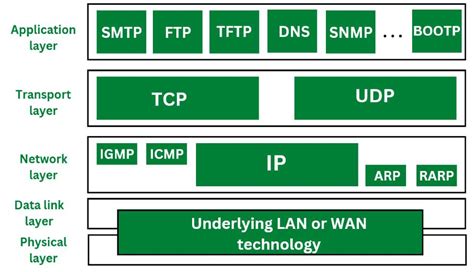
Integrating external network protocols into the Windows operating system opens up a world of possibilities and expands the functionality of the existing network infrastructure. This section delves into the seamless integration of third-party network protocols within Windows, exploring the diverse benefits and challenges associated with this process.
- Understanding the Need for External Network Protocol Integration
- Examining the Selection Criteria for Third-Party Network Protocols
- Overcoming Integration Challenges and Ensuring Compatibility
- Implementing and Managing Third-Party Network Protocols in Windows
- Exploring Real-Life Examples of Successful Protocol Integration
In today's interconnected world, where diverse network devices and systems operate across various platforms, the incorporation of third-party network protocols becomes imperative. This section delves into the reasons why organizations choose to integrate external network protocols with Windows, acknowledging the advantages it brings, such as enhanced compatibility and extended functionality.
Choosing the right third-party network protocol plays a vital role in ensuring seamless integration with Windows infrastructure. This subsection explores the key criteria organizations should consider when selecting an external network protocol to meet their specific requirements, including protocol efficiency, security features, community support, and ease of implementation.
Integrating third-party network protocols within Windows can present certain challenges that need to be addressed for successful implementation. This part discusses the common roadblocks organizations may face, such as interoperability issues, conflicting protocol standards, and potential performance bottlenecks. Strategies and best practices for overcoming these challenges and ensuring compatibility are explored.
This subsection provides practical guidance on the implementation and management of third-party network protocols in a Windows environment. It covers essential steps and considerations for a smooth integration process, including protocol installation, configuration, and ongoing monitoring and maintenance. Additionally, this part discusses the significance of effective documentation and training resources for successful protocol management.
Highlighting real-life cases where organizations have successfully incorporated third-party network protocols into their Windows networks, this section offers valuable insights and inspiration. By examining these examples, readers can gain a deeper understanding of the benefits, challenges, and potential outcomes associated with integrating external network protocols into a Windows environment.
By comprehending the opportunities and complexities associated with incorporating third-party network protocols into Windows, organizations can effectively leverage the power of diverse network technologies and optimize their network infrastructure to meet evolving business needs.
Emerging Trends in the Future Development of Windows Network Protocols
In this section, we will explore the potential advancements and directions in the evolution of Windows network protocols. Focusing on the advancements and innovations that lie ahead, we aim to provide insights into the future trends shaping the landscape of network protocols.
Exploring New Horizons
The ever-changing realm of technology constantly pushes the boundaries of what is possible. As we delve into the realm of future network protocol development, we find ourselves poised on the precipice of exciting possibilities. This section aims to present a glimpse into the potential breakthroughs awaiting us in the world of Windows network protocols.
The Rise of Artificial Intelligence
One of the most significant trends anticipated in the development of Windows network protocols is the integration of artificial intelligence. AI has already demonstrated its potential in revolutionizing various aspects of technology and is set to play a pivotal role in the future of network protocols as well. This section will explore how AI can enhance network performance, security, and management.
Enhancing Network Security
With the growing sophistication of cyber threats, network security has become a critical concern. In this section, we will examine the future trends in Windows network protocols that focus on enhancing security measures. From advanced encryption techniques to anomaly detection algorithms, we will explore the innovative approaches that can safeguard networks from evolving cyber threats.
Seamless Integration with IoT
The proliferation of the Internet of Things (IoT) has necessitated the development of network protocols that seamlessly integrate with an array of devices. This section will delve into the potential future advancements in Windows network protocols that can enable smooth communication and connectivity with IoT devices, facilitating the growth of smart homes, industries, and cities.
Transition to Quantum Networks
Quantum computing holds immense promise for the future, and its impact on network protocols cannot be ignored. As we move towards the era of quantum computing, this section will explore the potential challenges and opportunities in developing Windows network protocols that can harness the power of quantum technologies and ensure secure and efficient communication in this new paradigm.
In conclusion, this section provides a glimpse into the future trends in Windows network protocol development. From the integration of artificial intelligence to enhanced network security and seamless integration with the IoT, the future holds exciting possibilities for the evolution of network protocols.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
What is Windows Network Protocol Creation and Management?
Windows Network Protocol Creation and Management is a comprehensive guide that provides detailed information on how to create and manage network protocols in the Windows operating system.
Why is it important to understand network protocol creation and management?
Understanding network protocol creation and management is crucial for network administrators and IT professionals as it allows them to design, implement, and troubleshoot networks effectively, ensuring smooth communication and data transfer within an organization.
What are the key components of network protocol creation and management in Windows?
The key components of network protocol creation and management in Windows include protocol design, implementation, configuration, and monitoring. It also covers topics such as security, performance optimization, and troubleshooting.
Are there any best practices for network protocol creation and management in Windows?
Yes, the article provides several best practices for network protocol creation and management in Windows. Some of them include proper documentation, thorough testing, regular updates, and adherence to industry standards and protocols.
Is this guide suitable for beginners or is it more advanced?
This guide caters to both beginners and advanced users. It starts with the basics of network protocols and gradually delves into advanced topics, making it suitable for readers with varying levels of knowledge and experience in network administration.
What is the importance of network protocol creation and management in Windows?
Network protocol creation and management are crucial for Windows as they define the rules and standards for communication between devices on a network. It allows different devices and software to understand each other's data and ensures smooth and efficient data transfer.




