In today's digital age, where smartphones and tablets have become an integral part of our lives, it is not uncommon to forget the passcode to your iPad. And, let's face it, constantly entering the wrong passcode can be extremely frustrating and time-consuming. Luckily, there are ways to bypass the lock screen of your iPad and regain access to all your precious data and apps.
By utilizing clever techniques and leveraging the inherent vulnerabilities in Apple's security system, you can gain entry to your iPad without the need for remembering the exact password combination. It's like having a master key that unlocks the doors to your own digital kingdom, allowing you to regain control over your device and continue using it without any restrictions.
However, it's important to note that this method should only be used ethically and on your own devices. It goes without saying that attempting to gain unauthorized access to someone else's iPad is illegal and can have serious consequences. Always remember to respect others' privacy and only use this knowledge for legitimate purposes.
So, if you find yourself locked out of your iPad and desperately need to regain access to your files, documents, and applications, join us as we explore the fascinating world of bypassing iPad passcodes. Discover the secrets that lie beneath the surface of Apple's security measures and learn how to unlock your iPad effortlessly, ensuring that you never have to be locked out again.
Exploring Methods to Override Security Settings on Apple Tablets: A Comprehensive Guide
Within the realm of digital devices, there is a demand to understand alternative approaches for bypassing the security measures of Apple tablets. This extensive guide aims to shed light on various techniques that enable users to bypass the protective features of these devices. By exploring these methods, individuals can expand their knowledge about potential workarounds and gain entry into iPads without relying on traditional means.
1. The Evasive "Passcode Obsolescence" Technique:
One of the potential strategies for circumventing Apple iPad security is to employ the "Passcode Obsolescence" technique. This approach involves leveraging alternative methods to render the existing security measures obsolete, thus granting access to the device.
2. The Enigmatic "Biometric Anomaly" Approach:
For those seeking an unconventional workaround, the "Biometric Anomaly" approach may provide a solution. This method explores the intricate nuances of the iPad's biometric security features to discover potential vulnerabilities that can be exploited to bypass the password requirement.
3. The Elusive "Operating System Manipulation" Method:
Another avenue worth exploring is the "Operating System Manipulation" method, which delves into the underlying software framework of the iPad. By skillfully manipulating the operating system, individuals can gain access to the device even without having knowledge of the original password.
4. The Ingenious "iCloud Syncing" Technique:
Considering the increasing reliance on cloud technologies, it becomes crucial to explore the potential role of iCloud syncing in bypassing iPad passwords. The "iCloud Syncing" technique investigates the device's synchronization process, aiming to identify gaps within its security mechanisms that can lead to password bypass.
5. The Resourceful "Third-Party Applications" Exploits:
Lastly, individuals looking to bypass the iPad password extensively explore the plethora of third-party applications available in the market. Making use of the vulnerabilities and loopholes found within these applications, users can potentially gain access to the iPad without the need for the original password.
By considering these alternative approaches, one can expand their understanding of the techniques available for bypassing iPad passwords. Please note that these methods are shared for informational purposes only, and attempting to bypass security measures without proper authorization may breach legal and ethical boundaries. It is essential to exercise caution and respect the privacy and security of others.
Understanding the Significance of Enhancing Security for iPad Passwords
Given the constant evolution of technology and the increasing dependence on digital devices, comprehending the importance of reinforcing password security on iPads has become paramount. Enhancing the defense mechanisms for your iPad's password serves as a crucial safeguard against unauthorized access and potential breaches of personal information.
- Protection against Intrusion: Implementing strong and reliable passwords on iPads provides a vital defense mechanism against unauthorized individuals trying to gain access to confidential data stored on the device.
- Safeguarding Personal Information: By reinforcing password security, iPad users can protect sensitive personal information, including financial data, private conversations, and important documents from falling into the wrong hands.
- Preserving Digital Identity: The utilization of sturdy passwords for iPad accounts helps safeguard your digital identity, ensuring that your online presence and activity remain protected from potential threats.
- Minimizing Data Breaches: Strengthening password security can contribute to minimizing the likelihood of data breaches, thereby safeguarding not only your own information but also that of any connected networks or individuals with whom you interact digitally.
- Preventing Unauthorized Purchases and Access: An enhanced password barrier can act as a preventive measure against unauthorized purchases made through apps or websites, as well as unapproved access to various online platforms.
Understanding the significance of reinforcing password security on iPads goes beyond the simple act of protecting a device; it is about safeguarding personal and digital integrity in an increasingly interconnected world.
Considering the legal aspects prior to attempting to disable security measures on an Apple tablet
When venturing into the realm of attempting to disable the security protocols on a certain brand of tablet device, it is crucial to be aware of the legal implications that are associated with such actions. Prior to engaging in any activities that involve circumventing security measures, individuals must possess a thorough understanding of the legal considerations and potential ramifications that may arise.
Comprehending the legal implications: A crucial aspect when contemplating actions related to disabling security on a tablet device is to gain a comprehensive understanding of the legal framework surrounding such activities. Familiarize yourself with laws and regulations pertaining to device security, digital rights, and intellectual property, ensuring compliance with any applicable jurisdictional requirements.
Evaluating the impact on device warranty: It is vital to recognize that attempting to disable security features may void the device warranty, as such measures are put in place to protect the integrity and functionality of the tablet. Assess the potential consequences of losing warranty coverage before proceeding with any actions that may compromise the device's security.
Knowing the ownership and consent requirements: It is essential to ascertain the legal ownership of the tablet and whether you have the necessary consent to modify its security settings. If you do not have legal ownership or the owner's explicit permission, any attempt to bypass the password may be illegal and subject to legal consequences.
Consulting legal professionals: To ensure adherence to legal regulations, seek advice from legal professionals who specialize in technology and intellectual property. They can provide valuable insight into the specific legal considerations pertaining to disabling security measures and offer guidance on navigating the complex legal landscape.
Disclaimer: The information provided in this article is for informational purposes only and does not constitute legal advice. It is important to consult with a qualified legal professional for advice regarding the specific circumstances of your situation.
Alternative Approaches for Overcoming Security Measures on an iOS Device
When faced with the challenge of accessing an iOS device protected by a passcode, individuals may find themselves looking for alternative methods rather than attempting to directly bypass the security measures. While it may be tempting to search for ways to unlock an iPad without the correct passcode, it is essential to explore traditional techniques that can potentially lead to success.
1. Recovery through Passcode Hints:
One of the primary ways to uncover the passcode for an iPad is by utilizing the passcode hints provided on the lock screen. Alongside the numeric keypad, users have the option to set up hints that can help in remembering the correct combination. By carefully analyzing the hints and employing logical thinking, individuals can increase their chances of recalling the passcode accurately.
2. Utilizing Default or Frequently Used Codes:
Another traditional approach to surpassing a locked iPad is considering default or frequently used passcodes. This strategy is based on the premise that individuals often select easily guessable codes, such as birthdates, simple patterns, or sequences, ultimately compromising the security of their device. By conducting some background research or analyzing personal preferences, it may be possible to unlock an iPad by trying these commonly used passcodes.
3. Subsequent Attempts with Delays:
In cases where guesswork is the only option left, individuals can experiment with different combinations and introduce delays between consecutive incorrect attempts. iOS will typically impose a time delay before the next try, which gradually increases with each failed attempt. By strategically taking advantage of these imposed delays, one can eventually uncover the correct passcode without the need for advanced bypassing techniques.
4. Seeking Assistance from Official Channels:
If all else fails or the urgency to access the iPad is high, individuals can reach out to official channels, such as Apple Support or an authorized service provider. These entities can provide guidance and potential solutions to bypassing the lock screen, taking into account the rightful ownership of the device. It is important to note that such assistance may involve specific procedures or proof of ownership to ensure compliance with legal and ethical standards.
In conclusion, while bypassing an iPad passcode without utilizing professional tools or advanced techniques can present difficulties, exploring alternative approaches can yield favorable results. Taking advantage of passcode hints, considering common codes, employing timed delays, or seeking official assistance offer various strategies to overcome the security measures of an iOS device.
Guessing the password: The simplest approach

The act of guessing the password may seem like a straightforward strategy to gain unauthorized access to an iPad device. By employing various techniques and tricks, individuals attempt to uncover the secret combination that grants them entry into someone else's digital world.
1. Brute force: One common method involves using software that systematically tries all possible combinations of characters until the correct password is deciphered. This approach can be time-consuming due to the vast number of combinations that exist, especially if the password is complex.
2. Dictionary attack: Another approach is to use a program that scans through a database of commonly used passwords or commonly accepted words. This method relies on the assumption that individuals tend to use familiar words or easily guessable phrases as their passwords.
3. Social engineering: This technique involves gathering information about the target user through various means, such as online research or personal interactions. By understanding the individual's preferences, hobbies, or significant life events, it is possible to make educated guesses about their password choices.
4. Common patterns or personal information: Many individuals use patterns or personal information as a basis for their passwords. Names of family members, birthdays, or favorite songs are examples of commonly used elements that may be used as a starting point for guessing a password.
5. Keystroke monitoring: In some cases, malicious individuals may try to monitor a target user's keystrokes. By observing the patterns and frequency of certain keys being pressed, they can derive potential combinations that the user might be using as their password.
- Brute force: Trying every possible combination of characters until the correct password is found.
- Dictionary attack: Using a database of commonly used passwords or words to find an easy-to-guess password.
- Social engineering: Researching personal information or interacting with the target to make educated guesses about their password choices.
- Common patterns or personal information: Using patterns or personal details, such as names or birthdays, as a basis for guessing a password.
- Keystroke monitoring: Observing keystrokes to derive potential password combinations.
Using iTunes to Restore the iPad and Eliminate the Passcode
In this section, we will explore a method that involves utilizing iTunes to restore your iPad and effectively remove the passcode protection. By following these steps, you will regain access to your device without bypassing any security measures or compromising its integrity.
Step 1: Preparation
Before proceeding with the restoration process, ensure that you have the latest version of iTunes installed on your computer. Additionally, ensure that your iPad is sufficiently charged or connected to a power source throughout the process to avoid interruptions.
Step 2: Connecting the iPad
Connect your iPad to the computer using a USB cable. Launch iTunes on your computer, and it should automatically recognize the connected device.
Step 3: Entering Recovery Mode
To enter recovery mode on your iPad, simultaneously press and hold the Sleep/Wake button and the Home button. Keep holding both buttons until the iPad screen displays the iTunes logo along with a USB cable symbol.
Step 4: Restoring the Device
In iTunes, you should now see a prompt indicating that your iPad is currently in recovery mode and needs to be restored. Click on the "Restore" button to begin the restoration process.
Step 5: Confirming the Restoration
A pop-up window will appear, asking you to confirm the restoration. It's important to note that this process will erase all data and settings on your iPad. Ensure that you have a recent backup of your device before proceeding. Click on the "Restore and Update" button to continue.
Step 6: Waiting for the Restoration
iTunes will now proceed to download the necessary software for the restoration process. The download time may vary depending on your internet connection speed. Ensure that your computer remains connected to the internet throughout the process.
Step 7: Setting up the iPad
Once the download is complete, iTunes will restore your iPad to its factory settings. This includes eliminating the passcode lock. Follow the on-screen instructions to set up your device as a new iPad or restore it from a previous backup.
Step 8: Completion
After the setup process is complete, your iPad will no longer have a passcode and will be accessible without any restrictions. You can now start using your device as usual or reconfigure any necessary settings.
Remember to use this method responsibly and only on your own iPad or with appropriate authorization. Removing someone else's passcode without permission is a violation of privacy.
Utilizing iCloud to Restore Access to Your iPad by Resetting the Passcode
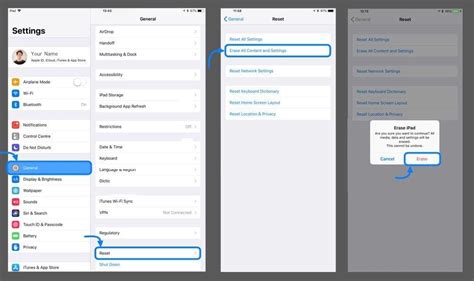
Discover a seamless approach to regain access to your iPad and reset the passcode using the power of iCloud. By leveraging the robust capabilities of iCloud, you can easily reset your iPad's passcode and gain uninterrupted access to your device.
Step 1: Accessing iCloud To initiate the process, navigate to the iCloud website on a computer or another iOS device. Enter your credentials, including your Apple ID and password, to log in. |
Step 2: Device Selection Once you have successfully logged into iCloud, locate and select the "Find iPhone" icon. This will allow you to access your connected devices. |
Step 3: Selecting the iPad From the list of available devices, identify and choose your iPad that you wish to reset the passcode for. This will trigger additional options specific to your selected device. |
Step 4: Enabling Lost Mode Activate the "Lost Mode" feature, which will lock your iPad remotely. This action will prompt you to set a temporary passcode that will override your current passcode. |
Step 5: Resetting the Passcode Once the "Lost Mode" is enabled, proceed to set a new passcode for your iPad. Make sure to choose a memorable yet secure passcode to ensure the privacy of your device. |
Step 6: Access Restored After successfully resetting the passcode, you can now regain access to your iPad using the temporary passcode you set. Once you have logged in, you can customize your passcode settings according to your preference. |
By utilizing iCloud's advanced features, you can conveniently reset your iPad's passcode and regain access to your device without any hassle. Ensure the security of your personal data while enjoying the ease of accessing your iPad with the help of iCloud.
Exploring Advanced Techniques to Circumvent Security Measures on Your Apple Tablet
When faced with the need to overcome the protective mechanisms implemented on your Apple tablet, it is essential to possess a thorough understanding of the more sophisticated approaches available at your disposal. This section delves into the realm of advanced techniques, delving into alternative strategies for overcoming the security barriers in place.
1. The Art of Incognito: Discover the power of concealing your intentions by utilizing strategies that allow you to navigate the digital landscape undetected. Explore options like disguising your identity, manipulating device metadata, and altering system logs to maintain a cloak of invisibility.
2. Exploiting Anomalies: Uncover the secret vulnerabilities hidden within the Apple tablet's operating system and exploit them to achieve your desired outcome. Gain insight into identifying and capitalizing on inconsistencies within the security architecture.
3. Evasive Maneuvers: Master the skills necessary to outsmart and outmaneuver the security measures implemented by Apple. Learn about the techniques like social engineering, hardware manipulation, and unconventional methods to bypass the password barriers.
4. The Power of Persuasion: Explore the realm of persuasive tactics that can be employed to gain access to an iPad without relying on conventional means. Investigate psychological manipulation techniques and non-technical approaches to convince authorized users to share their password unwittingly.
5. Advanced Scripting: Delve into the world of scripting and automation to increase your chances of breaking through the security layers in place. Understand the importance of scripting languages such as Python and their potential to automate password bypassing processes.
6. Cryptographic Conundrums: Gain knowledge about the intricacies of encryption algorithms and cryptographic protocols utilized on Apple devices. Unravel the mysteries behind password hashes, rainbow tables, and cryptographic key manipulation to overcome the barriers protecting sensitive information.
Remember: The information provided within this section is purely educational and should only be used responsibly. Unauthorized access to personal devices may be illegal, and it is crucial to respect the privacy and security of others.
Overcoming the Restriction: Harnessing External Software Solutions

When confronted with the challenge of gaining access to a locked device, individuals can explore alternative measures beyond traditional means. Empowering oneself with third-party software offers a potential solution to bypass the limitations imposed by password restrictions.
Jailbreaking the iPad: A risky but effective alternative
In the realm of unlocking the potential of the iPad lies a daring and controversial method known as jailbreaking. While this process is not without risks, it offers users an alternative pathway to explore the boundaries of their device beyond the confines set by the manufacturer.
By engaging in jailbreaking, individuals can break free from the limitations imposed by the device's default settings and gain access to a whole new world of customization and functionality. Although the term "jailbreaking" may seem negative, it actually refers to liberating the iPad from its locked state, granting users the freedom to install unauthorized apps and tweaks that are not readily available on the official App Store.
However, it is crucial to acknowledge the potential drawbacks and risks involved in jailbreaking. First and foremost, the process itself is not supported or endorsed by Apple, and therefore, it voids any warranty associated with the device. Additionally, since jailbreaking involves modifying core system files, it can lead to instability, security vulnerabilities, and even the potential for malicious attacks.
Despite these risks, many users find the benefits of jailbreaking to be worth the potential consequences. By jailbreaking their iPad, individuals can enjoy a wide range of advantages, such as the ability to customize the appearance of the device's interface, install third-party apps not available on the App Store, and access advanced system settings for greater control and optimization.
It is crucial, however, for individuals considering jailbreaking to proceed with caution and be fully aware of the potential risks involved. This process requires technical knowledge and expertise, as well as a thorough understanding of the potential consequences and the steps necessary to mitigate them.
| Pros | Cons |
|---|---|
| Access to unauthorized apps and tweaks | Potential loss of device warranty |
| Greater customization options | Increased risk of instability and software malfunctions |
| Advanced system control and optimization | Potential security vulnerabilities |
Ethical considerations in the process of circumventing an iPad lockscreen

When exploring the ethical dimensions of circumventing the security measures of an Apple tablet, it is essential to analyze the moral ramifications that arise from such actions. This section delves into the various ethical considerations one must take into account when attempting to bypass the protective screen lock of an iPad, as well as the potential consequences that may follow.
- The importance of informed consent: Prior to attempting to bypass an iPad password, it is crucial to obtain clear and explicit consent from the owner of the device. This ensures that the individual is aware of and agrees to the potential invasion of their privacy.
- Respecting personal boundaries: In any ethical discussion regarding circumvention of security measures, it is essential to acknowledge and respect the private sphere of individuals. Bypassing an iPad password should only be considered in specific and justified circumstances where legally authorized or authorized by the owner.
- Consideration of legal implications: Alongside ethical considerations, it is important to be mindful of the legal implications that surround the act of bypassing an iPad lockscreen without proper authorization. Engaging in such activities without legal grounds could potentially result in legal consequences.
- The balance between security and accessibility: While there may be legitimate reasons to bypass the lockscreen of an iPad, it is essential to maintain a delicate balance between ensuring security and upholding privacy rights. The ethical path lies in approaching each case individually and weighing the potential risks and benefits.
- Transparency and accountability: When bypassing an iPad password, it is imperative to adopt a responsible approach by keeping records of the process. This includes documenting the purpose for bypassing the lockscreen, the steps taken, and any information accessed during the process. This ensures transparency and accountability.
By navigating the ethical considerations involved in bypassing an iPad password, individuals can approach such actions with the necessary prudence and responsibility. Bearing in mind the potential impacts on privacy and legality, it is essential to approach each situation with a conscientious mindset, considering both the rights of individuals and the broader implications of one's actions.
FAQ
How can I bypass the password on my iPad?
There are a few methods you can try to bypass the password on your iPad. One option is to use iTunes to restore your device to factory settings, but keep in mind that this will result in the loss of all your data. Another method involves using a third-party software designed specifically for bypassing iPad passwords. Lastly, if you've synced your iPad with iCloud and have Find My iPad enabled, you can remotely erase your device and then set it up as new.
Is it possible to bypass the iPad password without losing any data?
Unfortunately, if you can't remember the password to unlock your iPad, it is difficult to bypass it without losing any data. The safest and most effective method to regain access to your iPad in this situation is to restore it to factory settings using iTunes. However, this will result in the deletion of all data on your device.
Can I bypass the iPad passcode with Touch ID or Face ID?
If your iPad has Touch ID or Face ID enabled, you can use these features to bypass the passcode. Simply place your registered finger on the Touch ID sensor or allow Face ID to recognize your face, and your iPad will unlock without the need for a passcode.
Are there any risks involved in bypassing the iPad password?
While there are methods available to bypass the iPad password, it's important to note that these methods may come with risks. Using third-party software or restoring your device with iTunes can potentially lead to data loss or other issues. It's always recommended to create regular backups of your data to prevent any major loss in case of password-related difficulties.
What should I do if I forgot my iPad password?
If you forgot your iPad password, the best course of action is to use iTunes to restore your device to factory settings. This will erase all data on your iPad, but it's the only way to regain access without the correct password. Remember to back up your data regularly to avoid losing important information in situations like this.
Is it possible to bypass the iPad password and gain access without knowing the password?
Yes, it is possible to bypass the iPad password and gain access without knowing the password. There are various methods and tools available online to help you bypass the password. However, it is important to note that bypassing a password without proper authorization is illegal and unethical.
Are there any risks involved in bypassing the iPad password?
Yes, there are risks involved in bypassing the iPad password. By using unauthorized methods or tools to bypass the password, you might compromise the security of your device and personal data. Additionally, you may violate the terms and conditions set by Apple, which can result in repercussions such as voiding your device's warranty.