In today's digital age, ensuring the protection of your personal data and sensitive information is of paramount importance. With the ever-increasing number of cyber threats and malicious actors out there, it is crucial to have robust security measures in place. One highly effective way to bolster the security of your computer system is by implementing a personalized lockout mechanism.
By configuring custom lockout settings, you can fortify your computer's defense against unauthorized access and potential breaches. This powerful feature allows you to restrict the number of failed login attempts, specify time intervals between login attempts, and establish stringent password requirements.
With the ability to tailor lockout parameters to your specific needs, you can create an additional layer of protection that complements your existing security measures. Whether you are an individual user concerned about personal privacy or an organization looking to safeguard critical data, setting up a customized lockout system is a prudent step in the right direction.
Enhancing Security Measures with Windows Lockout

In today's digital landscape, safeguarding our personal data and protecting sensitive information has become paramount. Implementing an effective Windows lockout mechanism can significantly contribute to enhancing the security measures of your computer system. By employing this feature, you can prevent unauthorized access and unauthorized use of your device, ensuring the utmost protection for your valuable data and personal privacy.
Augmenting security:
The increasingly sophisticated methods used by cybercriminals necessitate the implementation of robust security measures. Setting up Windows lockout adds an additional layer of defense against potential breaches, making it significantly more challenging for unauthorized individuals to gain entry into your system or tamper with your files. This security feature discourages and deters unauthorized access attempts, thereby safeguarding your computer and its contents from potential threats.
Protecting personal information:
Your computer contains a wealth of personal information, ranging from financial data to sensitive documents and personal communications. These records are highly valuable and can be exploited if they fall into the wrong hands. By implementing a Windows lockout, you can prevent unauthorized access to your confidential information, granting you peace of mind and protecting your personal and financial well-being.
Safeguarding privacy:
Privacy is a fundamental right that should not be compromised. By using Windows lockout, you can ensure that your private conversations, personal files, and sensitive data remain inaccessible to unauthorized individuals. This feature prevents unauthorized users from gaining unauthorized entry into your computer, maintaining the confidentiality of your digital life and upholding your right to privacy.
Preventing unauthorized usage:
Implementing Windows lockout serves as a strong deterrent against unauthorized usage of your computer. Whether you need to step away momentarily or leave your computer unattended for an extended period, enabling this feature adds an extra layer of protection, thwarting unauthorized users from utilizing your device without your permission. By doing so, you maintain control over your computer usage and mitigate the risk of unauthorized actions.
Conclusion:
Investing in the setup of Windows lockout not only fortifies the security of your computer system but also safeguards your personal information, preserves your privacy, and prevents unauthorized usage. By prioritizing these protective measures, you can ensure a safer digital environment for yourself and maintain control of your computer's integrity and security.
A Simple Method to Enable Security Measures on a PC
In this section, we will discuss a step-by-step guide on configuring a protective feature for your personal computer. By following the outlined instructions, you can establish a robust defense system that safeguards your data and privacy. By implementing this solution, you'll be able to restrict unauthorized access and enhance the overall security of your system.
To begin, let's start with the initial step: creating a user account. By having dedicated user accounts, you can assign specific access privileges to different individuals, ensuring customized control over the system. This allows for effective management and prevents unauthorized users from gaining unrestricted access to critical files and settings.
| Step | Description |
|---|---|
| 1 | Create a New User Account |
| 2 | Assign User Permissions |
| 3 | Configure Password Policies |
| 4 | Enable Automatic Lockout |
After successfully creating a user account, it is crucial to configure appropriate user permissions. By defining access levels and restrictions, you can regulate the actions each user can perform on the computer. This prevents unauthorized data manipulation and ensures that only authorized individuals can make significant changes or install new software.
Additionally, it is vital to establish strong password policies to maintain a robust defense against potential breaches. Configure password complexity requirements, establish password expiration intervals, and enforce password history rules. These measures discourage the use of weak and easily guessable passwords, thus reducing the risk of unauthorized access to your account.
Finally, enabling automatic lockout after a specified time of inactivity adds another layer of security to your system. By activating this feature, you can set a predetermined timeframe after which the system automatically locks itself. This prevents unauthorized users from gaining access to your computer if you forget to manually lock it before stepping away.
By following these step-by-step instructions, you can enhance the security measures on your computer significantly. Implementing user accounts, defining permissions, configuring password policies, and enabling automatic lockout will provide you with peace of mind, ensuring that your data remains secure from unauthorized access.
Choosing the Right Lockout Settings for Your Device

When it comes to securing your device, selecting the appropriate lockout settings is paramount. These settings determine the level of protection your device will have against unauthorized access, ensuring that your data and personal information remain safeguarded.
There are several factors to consider when choosing the right lockout settings for your device. First and foremost, assess the level of security you require. Depending on the sensitivity of your data, you may opt for a higher level of lockout measures to ensure maximum protection.
- Lockout duration: Define how long your device will remain locked after a certain number of failed login attempts. Consider striking a balance between security and convenience, as longer lockout durations may impede quick access to your device.
- Lockout threshold: Determine the number of failed login attempts that will trigger the lockout. Setting a higher threshold can deter potential intruders, but keep in mind that lower thresholds offer greater protection against brute-force attacks.
- Lockout type: Choose the type of lockout mechanism that suits your needs. You may opt for a temporary lockout, where the device is locked for a specific duration, or a permanent lockout that requires manual intervention to regain access.
- Additional security measures: Consider implementing multifactor authentication or biometric authentication to enhance the security of your device. These additional layers of protection can further deter unauthorized access.
Remember that it is essential to strike a balance between security and convenience when configuring lockout settings. Too strict lockout measures may inconvenience you, while lax settings may compromise the security of your device. Take the time to evaluate your needs and make informed decisions to ensure your device remains protected at all times.
Customizing the Screen that Appears when Your Windows System is Locked
When your computer's operating system encounters an unexpected event that results in it being locked, a screen appears to notify you and prevent further access until the issue is resolved. But did you know that you can customize this lockout screen to reflect your personal style or organization's branding?
By customizing the lockout screen, you can add a personal touch or professional look to the interface that appears when your computer is locked. It allows you to showcase your creativity or adhere to your organization's visual identity, making the lockout screen more visually appealing and engaging.
To customize the lockout screen, you can change the background image, modify the text, add your logo, or even include helpful information or contact details. This not only enhances the aesthetics of the lockout screen but also provides users with relevant information or instructions while they wait for access to be restored.
Customizing the lockout screen can be done through various methods, depending on your operating system. Windows provides built-in customization options, such as accessing the Group Policy Editor or using the registry editor. You can also explore third-party applications or software that specifically cater to lockout screen customization.
Remember, the lockout screen customization should not compromise the security or functionality of your system. It is important to choose appropriate images, messages, and logos that align with your intent while maintaining professionalism and usability.
By taking the time to customize your Windows lockout screen, you can transform it from a generic screen into a visually appealing and informative interface that not only enhances user experience but also reflects your personal or organizational identity.
Creating a Robust Password for Enhanced System Security
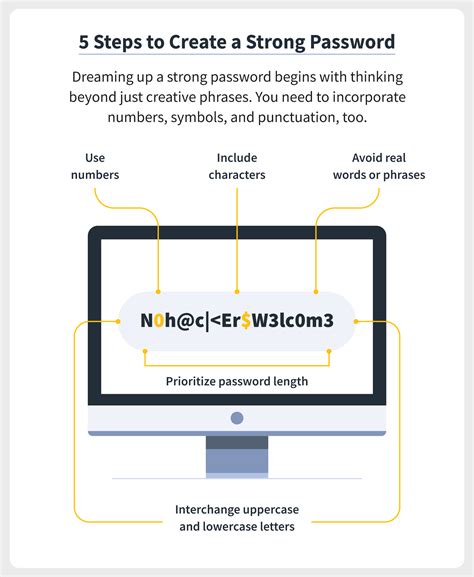
Introduction: Establishing a reliable password is essential for reinforcing the security mechanisms of your Windows account. By crafting a strong password, you can significantly decrease the vulnerability of potential unauthorized access to your system.
Why is a strong password important? A strong password acts as an impenetrable shield, protecting your computer from malicious activities and ensuring the privacy of your personal information. It serves as the first line of defense against unauthorized infiltration attempts.
What makes a password strong? A strong password possesses several key characteristics. Firstly, it should contain a combination of uppercase and lowercase letters, numbers, and special characters. This mixture provides a diverse combination that is hard to predict or guess. Additionally, a strong password should be unique and not easily associated with personal details, such as your name or birthdate.
Creating a strong password: To create a robust password, start by selecting a phrase or sentence that has personal significance but is not easily identifiable by others. Next, transform the phrase into a mnemonic combination of letters, numbers, and symbols. For example, "I love hiking in the mountains" can be transformed into the password "1L0veH1king!nTh3Mnt5."
Remember and protect your password: Once you have established a strong password, it is crucial to commit it to memory, ensuring you do not write it down or share it with anyone. Additionally, refrain from using the same password for multiple accounts, as this increases the risk of a security breach.
Regularly update your password: To maintain the highest level of security, it is recommended to change your password periodically. By doing so, you reduce the chances of unauthorized access and increase the overall security of your Windows lockout system.
Conclusion: Setting a strong password for your Windows lockout is an integral part of establishing a secure computing environment. By following the guidelines and best practices for creating a robust password, you significantly enhance the protection of your personal data and minimize the risk of unauthorized access to your computer system.
Introducing Automatic Inactivity Lockout
In this section, we will explore the process of enabling automatic lockout on your computer when it is left inactive. By implementing this feature, you can enhance the security of your system and protect your sensitive data from unauthorized access.
Enabling automatic lockout on inactivity involves configuring your computer's settings to automatically lock the screen and require a password after a specified period of inactivity. This feature can be particularly useful in situations where you need to step away from your computer but want to ensure that no one else can access your files or personal information.
One of the key advantages of enabling automatic lockout on inactivity is that it provides an additional layer of security. By setting a relatively short period of inactivity before the lockout engages, you can limit the time window in which someone could potentially compromise your computer.
- Step 1: Access the system settings
- Step 2: Locate the security settings
- Step 3: Enable the automatic lockout feature
- Step 4: Set the inactivity timeout
- Step 5: Test the automatic lockout
By following the steps outlined above, you will be able to enable automatic lockout on inactivity and enhance the security of your computer. Remember to choose a suitable inactivity timeout that balances convenience with security, as a too short timeout may cause frequent lockouts while a too long timeout may leave your computer vulnerable.
Configuring Windows Lockout for Multiple Users
In this section, we will explore the process of adjusting the lockout settings on a Windows operating system to enhance security for multiple users. By configuring the lockout parameters, you can implement measures to prevent unauthorized access and protect sensitive data. These settings can be customized to suit your specific requirements, allowing you to establish stringent security protocols for your computer system.
Step 1: Accessing the Lockout Policy
To begin, you need to navigate to the lockout policy settings on your Windows computer. This can typically be done through the Local Security Policy tool, which provides a graphical interface for configuring various security settings. Alternatively, you can use the Group Policy Editor to adjust lockout policies for multiple users on a network.
Step 2: Determining Lockout Thresholds
Once you have accessed the lockout policy settings, it is important to determine the appropriate lockout thresholds for unsuccessful login attempts. The lockout threshold refers to the number of failed login attempts allowed before a user is locked out of their account. By setting a reasonable threshold, you can strike a balance between security and user convenience.
Note: It is important to carefully assess the lockout thresholds to ensure they are not excessively rigid, causing frequent lockouts for legitimate users.
Step 3: Configuring Lockout Duration
Another crucial aspect of configuring Windows lockout for multiple users is defining the lockout duration. This parameter determines the length of time a user will be locked out of their account after reaching the lockout threshold. It is recommended to set a duration that is sufficient to deter potential attackers, while still allowing legitimate users to regain access after a reasonable period.
Note: Consider the potential impact of lockout duration on user productivity and weigh it against the level of security required for your computer system.
Step 4: Analyzing Lockout Event Logs
Regularly monitoring and analyzing lockout event logs is a vital step in managing lockout configurations for multiple users on your Windows computer. These logs provide valuable insights into the source of failed login attempts, enabling you to identify potential security threats and take appropriate actions to enhance your system's defenses.
Note: It is recommended to implement automated processes for reviewing lockout event logs to efficiently identify patterns or recurring issues.
By carefully configuring the Windows lockout settings for multiple users, you can bolster the security of your computer system and safeguard confidential information from unauthorized access.
Unlocking Your PC after a Temporary Block
Reclaiming access to your device may become necessary after a temporary limitation has been imposed. In this section, we will guide you through the steps to regain access to your operating system without compromising its security. Ensure that you follow the instructions carefully to prevent any further inconveniences.
Step 1: Authenticating Your Identity
To unlock your PC, you need to verify your identity through a secure authentication process. This ensures that only authorized individuals can regain access to the operating system. Various methods can be used for identity verification, such as entering a password, a PIN, or submitting biometric information like fingerprints or facial recognition.
Step 2: Password Recovery
If you are unable to recall your password, you can initiate a password recovery process by utilizing alternative security measures. This may involve answering security questions, receiving a verification code via email or text message, or signing in through another authorized device or account. It is crucial to set up these recovery options proactively to ensure a smooth and hassle-free unlocking experience.
Step 3: Contacting System Administrator
In some cases, unlocking your account might require intervention from a system administrator. This is commonly applicable in corporate environments or scenarios where additional security measures are in place. Contacting the system administrator will enable them to lift the lockout and provide assistance in recovering access to your PC.
Step 4: Enhancing Security Measures
Once you have regained access to your PC, it is advisable to revisit your security settings. Take the opportunity to strengthen your password, enable multi-factor authentication, or review any other security features that may help prevent future lockouts. By implementing these precautions, you can minimize the chances of being locked out again and enhance the overall security of your computer.
Conclusion
Experiencing a temporary lockout can be frustrating, but with the appropriate steps, you can regain access to your Windows operating system. Remember to prioritize security measures during the recovery process and take additional precautions to avoid future lockouts. Embrace the steps shared in this section to unlock your PC securely and efficiently.
Troubleshooting Common Issues with Windows Lockout

In this section, we will address the various challenges that users may encounter when implementing and managing the lockout feature on their Windows system. Understanding the potential roadblocks and finding effective solutions will help ensure a smooth and secure user experience.
1. Authentication Errors: One of the most common issues users face with the Windows lockout feature is authentication errors. These errors can occur due to incorrect login credentials, expired passwords, or account lockouts caused by multiple unsuccessful login attempts. It is important to troubleshoot and address these errors promptly to regain access to your system.
2. Policy Configurations: Another challenge users may come across is related to policy configurations. Windows lockout operates based on specific configurations set by system administrators or users themselves. If these policies are misconfigured, it can result in either excessive lockouts, where users are frequently locked out even with valid credentials, or insufficient lockouts that fail to secure the system adequately. Identifying and adjusting policy settings appropriately is crucial to ensure effective lockout functionality.
3. Network Connectivity: Windows lockout relies on network connectivity to verify login credentials and enforce lockout measures. Poor network connections, firewall restrictions, or DNS issues can affect the lockout feature's proper functioning. Troubleshooting network-related problems and ensuring a stable and secure network connection will help overcome these issues.
4. Software Conflicts: Conflicts between the lockout feature and other installed software can cause unexpected issues. Antivirus programs, firewalls, or other security software might interfere with the lockout functionality, resulting in false positives or false negatives. Identifying and resolving software conflicts will allow for seamless implementation and operation of the lockout feature.
5. User Education: Sometimes, the challenges users face with the lockout feature can be attributed to a lack of understanding or awareness. Users may not be familiar with the system's lockout policies, the consequences of incorrect login attempts, or the steps to regain access after a lockout. Providing comprehensive user education and clear instructions can minimize lockout-related issues and enhance user experience.
By addressing these common issues and taking the necessary steps to troubleshoot and resolve them, users can effectively implement and manage the lockout feature on their Windows systems, enhancing security and protecting sensitive information.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
What is Windows lockout and why is it important?
Windows lockout is a security feature that prevents unauthorized access to your computer. It is important because it safeguards your personal and sensitive information from being accessed by others.
How can I enable the Windows lockout feature on my computer?
To enable the Windows lockout feature, you can go to the Control Panel, click on "User Accounts", and then select "Change account settings". From there, you can choose the option to require a password when your computer wakes up from sleep or when the screen saver starts.
Can I customize the lockout settings on my computer?
Yes, you can customize the lockout settings on your computer. When you access the lockout options in the Control Panel, you can specify the amount of time before your computer locks, choose whether to display a message when it locks, and require a password to unlock it.
Is it possible to set up multiple user accounts with different lockout settings?
Yes, you can set up multiple user accounts on your computer, and each account can have its own lockout settings. This allows you to customize the lockout feature based on your preferences and requirements for each user.
What should I do if I forget my lockout password?
If you forget your lockout password, you can reset it by accessing the "User Accounts" section in the Control Panel. Look for the option to reset your password, which typically involves answering security questions or using alternate email addresses to verify your identity.
Why should I set up Windows Lockout on my computer?
Setting up Windows Lockout on your computer adds an extra layer of security by automatically locking your device after a period of inactivity. This helps prevent unauthorized access to your computer and protects your personal information and privacy.




