With the ever-increasing dependence on technology, security has become an indispensable aspect of our daily lives. One vital component in ensuring a secure digital experience is the implementation of robust authentication protocols. In this article, we will delve into the intricacies of establishing a rock-solid authentication system on a popular operating system, leveraging the power of an industry-leading security framework.
Within the realm of information security, establishing trustworthy and reliable authentication mechanisms is paramount. It provides an efficient way to safeguard sensitive data and ensure that only authorized individuals can access it. In our quest for a secure authentication framework, we will explore a widely-used methodology that guarantees authenticity and integrity without sacrificing performance or usability.
Throughout this step-by-step guide, we will unravel the secrets of a cutting-edge security protocol that has stood the test of time and is widely endorsed by industry experts. By leveraging the power of this protocol, we can create a robust framework for verifying the identity of users on a well-established and widely-adopted operating system. Get ready to embark on a journey that will equip you with the knowledge and skills needed to fortify your authentication infrastructure and protect your sensitive information from unauthorized access.
Understanding the Significance of Kerberos Authentication and its Relevance
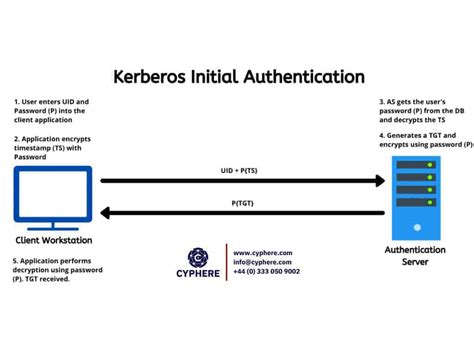
As we dive into the intricacies of setting up Kerberos authentication on a Windows client, it is essential to first grasp the importance and purpose behind this protocol. Kerberos authentication serves as a crucial element in ensuring secure and efficient communication within computer networks.
At its core, Kerberos authentication functions as a robust framework that facilitates secure authentication between a user and various network services. This authentication method is based on the concept of tickets, where Kerberos acts as a trusted third party to verify the identities of the involved entities.
- Vital Security Measures: By employing Kerberos authentication, organizations can enhance their security measures and protect sensitive data from unauthorized access. This protocol employs encryption techniques to safeguard communication channels and prevent malicious activities.
- Ease of Use: Kerberos offers a seamless user experience by enabling single sign-on functionality. Once a user logs in, they gain access to multiple network services without the need for repetitive authentication.
- Efficiency and Performance: With Kerberos authentication, the user's credentials are validated only once during the initial authentication process. This eliminates the need for frequent authentication requests, thereby enhancing network performance and reducing operational overhead.
Comprehending the importance of Kerberos authentication is vital in realizing its potential and grasping the significance of its configuration on a Windows client. By establishing a solid foundation of knowledge regarding this protocol, one can implement a robust security framework that protects critical data and ensures smooth network operations.
System Requirements
Minimum specifications
In order to successfully implement Kerberos authentication on a Windows client, it is essential to ensure that the system meets the minimum requirements. These specifications include hardware, software, and network prerequisites.
Hardware requirements
The hardware requirements for setting up Kerberos authentication on a Windows client vary depending on the specific environment and user needs. It is recommended to have a computer with adequate processing power, sufficient memory, and ample storage capacity to handle the authentication process effectively.
Software requirements
To enable Kerberos authentication, certain software components must be in place on the Windows client. This includes a supported operating system, such as Windows 10 or Windows Server, as well as the installation of appropriate updates and security patches. Additionally, the client must have the necessary Kerberos client software installed to facilitate the authentication process.
Network requirements
Establishing a secure network infrastructure is crucial for successful Kerberos authentication. The network should have adequate bandwidth to support the authentication traffic, and all relevant network protocols and services, such as DNS and Active Directory, should be properly configured and accessible.
Other considerations
In addition to meeting the minimum hardware, software, and network requirements, it is important to ensure compatibility with any existing systems or applications that will be utilizing Kerberos authentication. Proper planning, testing, and documentation will help streamline the implementation process and minimize any potential compatibility issues.
Understanding the Requirements for Implementing Kerberos Authentication

Before diving into the setup process, it is crucial to have a clear understanding of the essential components necessary to establish Kerberos authentication. By comprehending these key requirements, you can ensure a smooth and successful implementation of this secure authentication protocol.
1. Active Directory Infrastructure: To set up Kerberos authentication, a robust Active Directory infrastructure is needed. Active Directory serves as the central repository for authentication data, including user accounts and security policies.
2. Domain Controller: A domain controller is a vital component of the Active Directory infrastructure. It acts as a centralized server responsible for authenticating and authorizing users within a domain, enforcing security policies, and managing user accounts.
3. Service Principal Names (SPNs): SPNs are unique identifiers for services running on computers within a network. They enable clients and services to establish secure communications through Kerberos authentication. Configuring SPNs correctly is crucial for the successful operation of Kerberos.
4. Key Distribution Center (KDC): The Key Distribution Center is a core component of Kerberos infrastructure. It stores and manages cryptographic keys used for authentication, ensuring secure communication between clients and services.
5. Network Time Synchronization: Accurate time synchronization across all participating machines is essential for Kerberos to function correctly. Inconsistencies in time could lead to authentication failures and compromised security.
6. Understanding Kerberos Authentication Process: It is crucial to grasp the fundamentals of the Kerberos authentication process to configure and troubleshoot effectively. Familiarize yourself with the authentication flow, ticket granting process, and how authentication tickets are issued and validated.
By familiarizing yourself with these fundamental requirements and concepts, you will be well-prepared to embark on the step-by-step guide for setting up Kerberos authentication on your Windows client.
Section 1: Installation of the Kerberos Client Software
In this section, we will explore the initial step of setting up a secure authentication system by installing the necessary software required for Kerberos authentication. This involves configuring the essential components and libraries that facilitate secure communication and encryption without specifically mentioning the Kerberos protocol, the Windows operating system, or the authentication process. By following these instructions, you will ensure that your system is equipped with the appropriate tools to establish a robust and reliable authentication framework.
Begin the installation process by acquiring the designated software package for the Kerberos client. This package contains the essential files and dependencies required for secure authentication, ensuring a seamless integration with the overall system architecture.
Once the software package is obtained, navigate to the designated installation directory and execute the installation file. This will initiate the installation wizard, guiding you through the necessary steps to set up and configure the Kerberos client software on your system.
Follow the instructions provided by the installation wizard, carefully reviewing each step before proceeding. Pay close attention to any custom configuration options or additional settings that may enhance the security and functionality of the authentication system.
After completing the installation process, verify the successful installation of the Kerberos client software on your system. This can be achieved by checking the installation logs or using command-line tools to confirm the presence and proper functioning of the installed components.
By diligently following these steps, you will lay the foundation for successful integration of the Kerberos client software into your system, setting the stage for subsequent stages in the authentication setup process.
Getting the Kerberos Client: Download and Installation
In order to start using Kerberos authentication on your Windows system, you need to obtain and install the necessary Kerberos client. This section will guide you through the process of downloading and installing the client software, enabling you to securely authenticate with various network services.
Step 1: Downloading the Kerberos Client
Before you can install the Kerberos client on your Windows system, you must first acquire the necessary software. Head to the official Kerberos client website or a trusted software distribution platform to download the installer package.
Step 2: Installing the Kerberos Client
Once you have downloaded the Kerberos client installer, locate the downloaded file and double-click on it to start the installation process. Follow the on-screen instructions provided by the installation wizard to proceed with the installation.
Step 3: Configuring the Kerberos Client
After successful installation, you will need to configure the Kerberos client on your Windows system. This typically involves specifying the Kerberos realm, server information, and any additional configuration settings required by your network environment. The exact steps for configuring the client may vary depending on the client software version and your specific network setup.
Step 4: Verifying the Installation
Once the Kerberos client is installed and configured, it is important to verify that it is functioning correctly. This can be done by attempting to authenticate with a Kerberos-enabled service and checking for successful authentication. If any issues arise, refer to the official documentation for troubleshooting guidance.
By following these steps to download and install the Kerberos client on your Windows system, you will be ready to utilize the secure authentication capabilities offered by Kerberos for various network services.
Configuring the Kerberos Client: Key Steps to Enable Secure Authentication
In this section, we will explore the essential steps to configure the Kerberos client, enabling a secure and efficient authentication process for your system. By following these steps, you will establish a seamless connection with the authentication server, improving the overall security and integrity of your Windows environment.
- Discover and locate the relevant Kerberos configuration file, which contains the necessary settings and parameters for the client-side authentication process.
- Access and open the configuration file using a text editor, allowing you to modify the required settings based on your specific environment's needs.
- Identify and customize the realm configuration, specifying the realm name and associating it with the appropriate Kerberos Key Distribution Center (KDC).
- Define and configure the encryption types to be used for securing the authentication process, ensuring compatibility and compliance with your system's security policies.
- Adjust the settings related to ticket renewal and expiration, enabling a smooth operation without compromising security.
- Specify the default ticket lifetime and renewal period, aligning them with your organization's requirements and security guidelines.
- Configure the appropriate realm mapping, allowing the client to map user principal names to the correct realm and authenticate against the corresponding KDC.
- Identify and modify advanced settings, such as UDP and TCP port numbers, if necessary, to guarantee efficient communication between the client and the KDC.
- Save the modified configuration file, ensuring that the changes are applied correctly.
- Test the configured Kerberos client by initiating an authentication request and validating the successful establishment of a secure connection with the Kerberos server.
By carefully following these key steps, you will successfully configure the Kerberos client, solidifying the foundation for secure authentication within your Windows system.
Introduction to Configuring Kerberos Authentication on a Windows Device

In this section, we will explore the process of establishing secure and seamless authentication on your Windows device using the powerful and widely adopted Kerberos protocol. By implementing this robust authentication mechanism, you can ensure optimal protection against unauthorized access while enjoying a streamlined login experience. We will delve into the step-by-step configuration process, providing clear instructions and insights to empower you in setting up Kerberos authentication smoothly and effectively.
- Understanding the Importance of Kerberos Authentication
- Preparing Your Windows Device for Kerberos Configuration
- Installing and Configuring the Kerberos Client Software
- Configuring the Kerberos Realm and Domain
- Establishing Trust Relationships with Key Distribution Centers
- Generating and Distributing Kerberos Security Principals
- Configuring Kerberos Authentication Settings for Service Accounts
- Testing and Verifying Kerberos Authentication
By following these comprehensive guidelines, you will be able to successfully configure and leverage the advanced Kerberos authentication mechanism on your Windows client, bolstering your security measures and fortifying your authentication processes.
FAQ
What is Kerberos authentication?
Kerberos authentication is a network authentication protocol that provides strong authentication for client/server applications in a Windows environment.
Why should I use Kerberos authentication?
Kerberos authentication offers several advantages, including improved security, support for single sign-on, and simplified management of user credentials.
How do I enable Kerberos authentication on a Windows client?
To enable Kerberos authentication on a Windows client, you need to modify the client's Group Policy settings. This can be done by following a step-by-step guide, which includes configuring the client's security settings, enabling Kerberos delegation, and setting up key distribution centers (KDCs).
What are the prerequisites for setting up Kerberos authentication on a Windows client?
Before setting up Kerberos authentication, you need to ensure that you have a properly configured Active Directory domain, domain controllers, and a functioning DNS infrastructure. Additionally, you should have administrative access to the Windows client on which you will be enabling Kerberos authentication.
Are there any potential challenges or issues that may arise when setting up Kerberos authentication?
Yes, there can be potential challenges or issues when setting up Kerberos authentication. These can include incorrect configuration of domain controllers, DNS resolution issues, mismatched or expired Kerberos tickets, and various other configuration errors. It is important to carefully follow the step-by-step guide and troubleshoot any issues that may arise.
What is Kerberos authentication?
Kerberos authentication is a network authentication protocol that allows secure authentication between clients and servers on a network.




