Unlock the hidden potential of your Linux operating system to safeguard your network
In the ever-evolving world of cybersecurity, protecting your network becomes paramount. As threats become more sophisticated, it is essential to equip yourself with the necessary tools to defend against them. One such tool that holds the key to fortifying your Linux-based system is the iptables firewall.
Discover the untapped power of iptables for network security
In this comprehensive guide, we will delve into the intricacies of configuring iptables using the versatile bash command shell. By harnessing the power of this command-line tool, you will gain full control over inbound and outbound network traffic, ensuring that only authorized connections are allowed.
Unleash your network's potential with bash command shell
With its rich set of features, iptables enables you to create highly personalized firewall rules tailored to your network's specific needs. Whether you are a network administrator, system engineer, or anyone looking to enhance network security, this article will equip you with the knowledge and skills required to master iptables configuration.
Exploring the Functionality of iptables in a Linux Environment
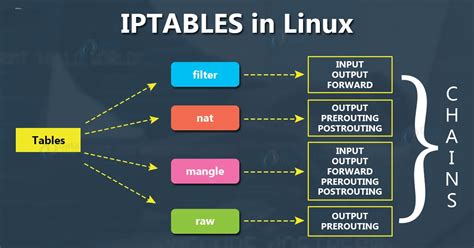
In this section, we will delve into the inner workings of iptables and develop a comprehensive understanding of its capabilities in a Linux system. By examining its features and functionalities, we will gain insight into how iptables can be effectively utilized to manage network security and control incoming and outgoing traffic.
- Examining the Core Concepts of iptables: Gain a deeper understanding of the fundamental principles behind iptables, including its structure, rule hierarchy, and packet filtering mechanisms.
- Analyzing iptables Tables and Chains: Explore the different tables and chains within iptables, such as the filter, nat, and mangle tables, and uncover their respective functionalities and purposes in network security.
- Understanding iptables Rule Syntax: Learn about the syntax used to create iptables rules, including the various components and options available for specifying source and destination IP addresses, ports, protocols, and action targets.
- Exploring Packet Filtering with iptables: Discover how iptables can be leveraged to filter incoming and outgoing network traffic based on specific criteria, such as IP addresses, ports, and protocols, and gain insight into the potential applications of this powerful feature.
- Utilizing iptables for Network Address Translation (NAT): Explore the functionality of iptables in performing network address translation, including techniques such as port forwarding, source/destination NAT, and masquerading, and the benefits they provide in network configuration and management.
- Implementing Advanced iptables Techniques: Dive into advanced iptables techniques, such as connection tracking, stateful filtering, rate limiting, and logging, and understand how these features can enhance network security and optimize performance.
By gaining a solid understanding of iptables and its capabilities, you will be equipped with the knowledge and skills to effectively implement and manage firewall rules in a Linux environment, ensuring the security and integrity of your network.
Essential Commands for Managing your Network Security
When it comes to securing your network in a Linux environment, understanding how to effectively use iptables is crucial. By mastering a few key commands, you can gain control over your firewall configurations and protect your system from potential threats.
- Rule creation: Creating rules is the cornerstone of iptables configuration. With commands like
iptables -Aoriptables -I, you can add new rules to your firewall chain, specifying the necessary criteria for packet filtering. - Rule deletion: It's equally important to know how to delete unnecessary rules. Using commands like
iptables -Doriptables -F, you can remove specific rules or flush an entire chain, respectively. - Listing rules: Being able to view your current firewall rules is crucial for troubleshooting and managing network security. Commands like
iptables -Loriptables -Sallow you to list the existing rules in different formats for better readability and understanding. - Rule modification: Sometimes, modifications are required to fine-tune your firewall settings. Commands like
iptables -Roriptables -Menable you to replace or modify existing rules without having to delete and recreate them. - Logging and auditing: iptables provides options for capturing logs and auditing network activity. Commands such as
iptables -A LOGoriptables -A INPUT -j LOGallow you to create log entries for specific rules or chains, aiding in the analysis of network traffic.
By familiarizing yourself with these essential iptables commands, you can confidently configure and manage your network security, ensuring the protection of your Linux system in an ever-evolving digital landscape.
Configuring Firewall Rules with iptables: Creating a Secure Network Environment

In this section, we will explore the process of setting up and managing firewall rules using the powerful iptables utility. By establishing and maintaining proper firewall configurations, you can enhance the security of your network infrastructure and protect your system against potential threats.
We will delve into various aspects of configuring iptables rules, beginning with the basics of rule creation. We will discuss different types of rules, such as allowing or denying specific types of network traffic, and explore the syntax and options used for rule definition.
In addition, we will examine the process of managing existing firewall rules, including how to modify, delete, or reorder them. Understanding these procedures is crucial for effectively adapting the firewall settings to the evolving needs of your system and network.
To further optimize the firewall configuration, we will explore more advanced concepts such as network address translation (NAT) and port forwarding. By utilizing these techniques, you can redirect incoming network traffic to specific internal services or applications, ensuring seamless connectivity while maintaining stringent security protocols.
Throughout this section, we will provide examples and practical scenarios to illustrate the implementation of various iptables rules. You will also learn about commonly used command-line options, enabling you to customize the firewall configuration according to your specific requirements.
By the end of this guide, you will have a comprehensive understanding of how to configure iptables rules effectively, allowing you to establish a robust and secure network environment for your Linux system.
Testing and Troubleshooting iptables Configuration
In this section, we will explore the various strategies for testing and troubleshooting your iptables configuration in a Linux environment using the bash command shell. It is crucial to verify the effectiveness of your firewall rules to ensure the security and proper functioning of your system.
Verification
To verify the functionality of your iptables configuration, you can employ a variety of techniques. One approach is to simulate network traffic and observe whether the desired rules are applied correctly. This can be accomplished using tools such as ping or curl to test the accessibility of specific services or ports. By sending test requests and examining the responses, you can validate that your iptables rules are functioning as intended.
Another method involves using the iptables command itself to display the current configuration and evaluate if it aligns with your expectations. By using specific options like -L or -S, you can view the currently active rules and chains. This provides a comprehensive overview of your firewall setup, allowing you to identify potential misconfigurations or discrepancies.
Troubleshooting
If you encounter issues with your iptables configuration, it is essential to have a systematic troubleshooting process in place. One crucial step is to check for errors or warning messages that may indicate a problem. These messages can be found in the system log files, such as /var/log/syslog or /var/log/messages. By carefully reviewing these logs, you can identify any errors related to iptables configuration and take appropriate actions to rectify them.
Additionally, if you suspect that a particular rule is causing problems, you can temporarily disable it to isolate the issue. This can be done using the iptables command with the appropriate options to delete or disable a specific rule. By selectively disabling rules and observing the system's behavior, you can pinpoint the problematic rule and adjust it accordingly.
Conclusion
Testing and troubleshooting are vital components of configuring iptables in a Linux system using the bash command shell. By employing various verification techniques and following a structured troubleshooting approach, you can ensure the effectiveness and stability of your firewall rules. Regular testing and monitoring of your iptables configuration will help mitigate any security risks and maintain a secure system environment.
Using `iptables` on Linux
Using `iptables` on Linux by macheads101 39,148 views 10 years ago 8 minutes, 25 seconds
UFW Full Tutorial | HackerSploit Linux Security
UFW Full Tutorial | HackerSploit Linux Security by Akamai Developer 14,180 views 3 years ago 25 minutes
FAQ
What is iptables? How does it work?
iptables is a user-space utility program that allows a system administrator to configure the IP packet filter rules of the Linux kernel firewall. It works by examining the destination and source addresses, ports, and protocols of network packets, and then decides whether to accept, drop, or forward them based on predefined rules.
Why should I configure iptables in my Linux system?
Configuring iptables in your Linux system is important for enhancing the security of your network. By setting up the appropriate rules, you can control incoming and outgoing network traffic, block unwanted connections, and protect your system from various types of attacks.
Can I configure iptables using the bash command shell?
Yes, you can configure iptables using the bash command shell. The iptables command provides a comprehensive set of options and parameters that allow you to create, modify, and delete firewall rules. By using the bash command shell, you can write scripts to automate the configuration process and easily manage your firewall rules.
What is iptables?
iptables is a user-space utility program that allows a system administrator to configure and manage the IP packet filter rules of the Linux kernel.




