Keeping your operating system secure is an essential aspect of maintaining the privacy and integrity of your data. In today's digital landscape, safeguarding your Windows system against unauthorized access is not just a necessity but also a responsibility. By implementing effective protective measures, you can fortify your system's defenses and enhance its overall security.
Shielding Your Windows System:
When it comes to safeguarding your Windows operating system, fortifying it with a reliable login protection mechanism is paramount. By assigning a robust and impenetrable password, you can effectively thwart malicious attempts to gain unauthorized access to your system. Creating a strong login password involves utilizing a combination of uppercase and lowercase letters, numbers, and special characters to ensure its complexity.
Securing your Windows system goes beyond simply setting up a strong password. Implementing additional protective measures can significantly enhance your system's security while minimizing vulnerabilities.
Creating a Robust and Distinctive Passcode
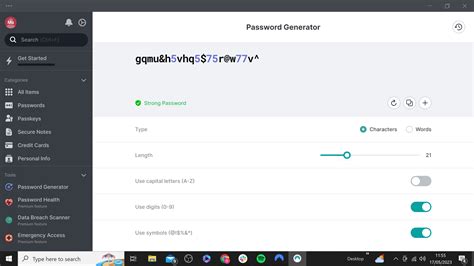
In the ever-evolving digital landscape, it is crucial to fortify your accounts with a sturdy and exclusive passcode. A strong and unique password acts as the first line of defense against unauthorized access to your personal information and sensitive data. In this section, we will delve into effective strategies and techniques to help you craft a password that is virtually impenetrable.
Selecting a combination of characters
When creating a password, it is advisable to go beyond the conventional choices and opt for a diverse combination of characters. This includes a mix of uppercase and lowercase letters, numbers, and symbols. By combining these elements, you enhance the complexity and strength of your password, making it more resilient against brute force attacks and dictionary-based hacking attempts.
Avoiding common and predictable patterns
It is imperative to steer clear of easily guessable patterns or sequences as they undermine the security of your password. Refrain from using common phrases, sequential numbers or keyboard patterns, such as "123456" or "qwerty". By choosing passwords that are unpredictable and devoid of familiar patterns, you significantly reduce the risk of unauthorized access to your accounts.
Length matters
The length of your password plays a pivotal role in its strength. Aim to create a password that exceeds the minimum character requirement set by the platform or service provider. The longer your password, the more permutations and combinations an attacker would need to try, making it increasingly arduous to crack.
Regularly updating your password
The journey towards a secure digital presence doesn't end at creating a strong password; it also requires regular updates. Adopt a habit of periodically changing your passwords to further fortify your accounts. Regularly refreshing your passcodes ensures that even if one account is compromised, the potential damage is limited.
In conclusion, forging a strong and unique password is paramount to safeguarding your digital assets and personal information. By considering a combination of characters, avoiding predictable patterns, prioritizing length, and practicing regular updates, you reinforce the overall security of your accounts.
Choosing a Strong and Secure Password: Essential Tips and Techniques
In the digital world, safeguarding your sensitive information is of utmost importance. Establishing a strong and secure password plays a vital role in protecting your personal data and maintaining your online privacy. This section explores key tips and techniques to help you select an effective password that is resistant to unauthorized access and potential breaches.
1. Length and Complexity: A lengthy password not only makes it more difficult for hackers to crack, but it also enhances its overall security. Encourage yourself to create passwords with a minimum length of 8 characters, combining upper and lowercase letters, numbers, and special characters. Consider utilizing a passphrase, which involves combining multiple English words to create a memorable yet robust password.
2. Avoid Common Passwords: Refrain from using common passwords like "123456" or "password" as they are the first targets for hackers. Avoid incorporating easily guessable information such as your name, birthdate, or pet's name. Opt for a unique combination that has no direct association with your personal life to minimize the chances of a potential security breach.
3. Password Manager Tools: Implementing a password manager can significantly elevate your password security. These tools generate and securely store unique passwords for each of your online accounts. By utilizing a master password, you only need to remember one strong password, enhancing convenience without compromising security.
4. Regular Password Updates: Regularly updating your passwords adds an extra layer of security. It is recommended to change your passwords every 90 days or sooner if any potential breaches are reported. This practice reduces the risk of unauthorized access and minimizes the damage caused by a compromised password.
5. Two-Factor Authentication: Enable two-factor authentication (2FA) whenever possible. This additional security measure requires a secondary form of verification, such as a unique code sent to your mobile device, in addition to your password. 2FA dramatically reduces the likelihood of unauthorized access, providing an added level of protection for your accounts.
By following these tips and techniques, you can significantly enhance the security of your password and protect your sensitive information from potential threats and cyberattacks. Remember, a strong password is the first line of defense in maintaining your privacy and security online.
Enhancing Security through the Use of Password Managers

In today's digital age, ensuring the security of our online accounts and personal information is paramount. One effective approach to enhance security is by utilizing password managers. These tools provide a convenient and secure way to store and manage passwords for various online platforms and applications.
By using a password manager, users can create strong, unique passwords for each online account without the need to remember them all. This eliminates the common practice of using easily guessable passwords or reusing the same password across multiple platforms, which greatly increases the vulnerability and potential for unauthorized access.
With the help of a password manager, individuals can generate and store complex passwords that include a combination of letters, numbers, and special characters. Additionally, password managers often offer features such as auto-fill and password synchronization across devices, further simplifying the login process while maintaining strong security measures.
Moreover, password managers employ encryption techniques to safeguard the stored passwords, making it extremely difficult for hackers to access the information. These tools utilize advanced encryption algorithms and additional security measures such as two-factor authentication to provide an extra layer of protection.
While password managers themselves require a master password to access the stored passwords, it is imperative to choose a strong and unique master password. This password should be memorable to the user but difficult for others to guess or crack. In this regard, employing techniques such as passphrase creation or utilizing a combination of random words can significantly improve the strength of the master password.
In conclusion, password managers offer a reliable and efficient solution to enhance the security of our online accounts. By enabling the creation of strong, unique passwords and securely storing them, these tools minimize the risks of unauthorized access and ensure the protection of sensitive information.
Enhancing Security with Two-Factor Authentication: Fortifying Your Digital Fortress
In this section, we will explore the concept of employing an additional layer of protection - two-factor authentication (2FA) - to safeguard your digital assets and personal information. Today, relying solely on usernames and passwords to secure our online accounts is no longer sufficient. With the growing sophistication of cyber threats, it has become crucial to fortify our defenses. Two-factor authentication provides an extra security measure by requiring users to provide two forms of identification to gain access to their accounts.
Advancing Beyond the Password: A Digital Shield
In the ever-evolving landscape of cybersecurity, relying solely on a password can leave your accounts vulnerable. With the advanced techniques employed by hackers, the password alone might not be enough to deter unauthorized access. By implementing two-factor authentication, you add an additional layer of protection that significantly decreases the chances of your accounts being compromised.
What is Two-Factor Authentication?
Two-factor authentication is a security mechanism that combines two different types of credentials to verify the user's identity. These credentials typically fall into three categories: something you know (e.g., a password or PIN), something you have (e.g., a physical token or a smartphone), or something you are (e.g., biometric data like fingerprint or facial recognition).
How Does Two-Factor Authentication Work?
When two-factor authentication is enabled, after entering your username and password, you will be prompted to provide an additional piece of information to verify your identity. This information could be a unique code sent to your smartphone, a fingerprint scan, or a physical token that generates a temporary code. Only after successfully providing this second form of identification will you gain access to your account.
The Benefits of Two-Factor Authentication
Implementing two-factor authentication provides several key benefits. Firstly, it adds an extra layer of security, making it significantly harder for unauthorized individuals to gain access to your accounts. Secondly, even if your password is compromised, the second form of identification ensures that your information remains secure. Thirdly, it gives you peace of mind, knowing that your accounts are protected by a powerful additional safeguard.
By incorporating two-factor authentication into your security practices, you are taking a proactive step towards fortifying your digital fortress and safeguarding your valuable data from potential breaches.
Exploring the Concept of Two-Factor Authentication
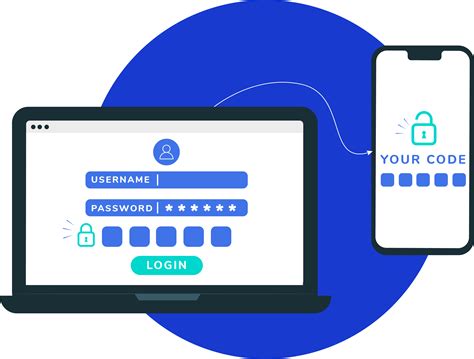
In the realm of digital security, it is vital to go beyond traditional password-based methods to protect sensitive information. This is where the concept of two-factor authentication comes into play. In this section, we will delve into the understanding of two-factor authentication and its importance in securing our digital lives.
- Enhancing Security
- Types of Factors
- How Two-Factor Authentication Works
- The Benefits of Two-Factor Authentication
- Popular Two-Factor Authentication Methods
Two-factor authentication provides an additional layer of security by requiring users to provide two distinct forms of identification before gaining access to a system or account. By combining something the user knows (e.g., a password) with something the user possesses (e.g., a mobile device or security token), the likelihood of unauthorized access is significantly reduced.
There are three primary types of factors used in two-factor authentication: knowledge factors, possession factors, and inherence factors. Knowledge factors involve something the user knows, such as a password or PIN. Possession factors include something the user possesses, such as a smartphone or a physical security token. Finally, inherence factors relate to something the user inherently possesses, such as fingerprints or facial recognition.
Two-factor authentication typically follows a sequence of events. Initially, the user provides their primary form of identification, such as a password. Once the password is verified, the system prompts the user to provide their secondary form of identification, such as a unique code sent to their mobile device or a fingerprint scan. Only when both forms of identification are successfully validated will the user be granted access.
Implementing two-factor authentication offers numerous benefits. Firstly, it serves as a deterrent to potential attackers, as breaking through two layers of security is significantly more challenging. Secondly, it reduces the risk of unauthorized access, providing peace of mind to users regarding the safety of their personal or sensitive information. Additionally, two-factor authentication can help mitigate the impact of data breaches, as even if passwords are compromised, the second factor acts as an additional safeguard.
There are various methods to implement two-factor authentication, including text message verification, mobile apps, physical security tokens, and biometric authentication. Each method has its own advantages and considerations, and organizations or individuals should carefully evaluate which method is most suitable for their specific needs.
FAQ
What are some tips for creating a strong password for Windows?
A strong password for Windows should be at least 8 characters long, include a combination of uppercase and lowercase letters, numbers, and special characters. Additionally, it is recommended to avoid using common words or personal information in the password.
Can I change the password for my Windows account?
Yes, you can change the password for your Windows account. To do so, go to the "Settings" menu, select "Accounts," then choose "Sign-in options." Under the "Password" section, click on "Change" and follow the prompts to set a new password.
Is it recommended to enable two-factor authentication for Windows?
Yes, enabling two-factor authentication adds an extra layer of security to your Windows account. It requires you to provide a second form of verification, such as a code sent to your mobile device, in addition to your password, making it harder for unauthorized users to access your account.




