When it comes to enhancing our Windows Subsystem for Linux experience, there are various tools and methods that can immensely improve our workflows. One such tool that stands out is the impressive combination of mitmproxy and Docker, which elevates the way we handle proxies in a Windows environment. This powerful duo allows us to seamlessly intercept, analyze, and modify network traffic, offering endless possibilities for debugging, security testing, and performance optimization.
In this article, we will delve into the intricate world of setting up and utilizing mitmproxy docker in Windows Subsystem for Linux. We will explore the nuances of proxy configuration and how it can be effectively employed for intercepting and manipulating network requests. By harnessing the potential of this dynamic combination, we can effortlessly gain deeper insights into the intricate workings of our applications, ultimately enhancing our development and troubleshooting capabilities.
Throughout this guide, we will dissect the step-by-step process of configuring mitmproxy docker, shedding light on the complexities and providing solutions to potential hurdles along the way. We will explore various techniques and tips to ensure a seamless integration within the Windows Subsystem for Linux environment. Additionally, we will provide insightful examples and use cases to illustrate the practical applications of this powerful combination in real-world scenarios.
Prepare to embark on a journey that will unlock a new realm of possibilities, revolutionizing the way you approach proxy configuration in the Windows Subsystem for Linux environment. Join us as we explore the intricacies of mitmproxy docker, uniting the powers of interception and manipulation to gain unparalleled insights into network traffic and elevate your development and debugging capabilities to unmatched heights.
Setting Up and Running mitmproxy Docker in Windows Subsystem for Linux (WSL)

Setting up and running mitmproxy Docker in Windows Subsystem for Linux (WSL) can be a convenient way to perform intercepting proxy tasks while utilizing the features offered by Docker technology.
Here, we will explore the step-by-step process of configuring mitmproxy Docker in Windows Subsystem for Linux, allowing you to intercept and manipulate network traffic seamlessly.
Prerequisites:
Before we dive into the setup process, ensure that you have the necessary prerequisites in place:
- Windows 10 operating system
- Windows Subsystem for Linux (WSL) enabled
- Docker installed and configured correctly
Step 1: Installing and Configuring mitmproxy Docker Image
In this step, we will guide you through the process of installing and configuring the mitmproxy Docker image, utilizing the powerful capabilities of Docker to provide a seamless setup experience.
Note: In WSL, Docker runs natively without the need for any virtualization.
Step 2: Creating a Docker Network
Now that we have the mitmproxy Docker image ready, we need to create a Docker network to ensure proper communication between the containers and the host system. This will allow us to intercept and analyze network traffic effectively.
Note: Creating a dedicated Docker network ensures better isolation and prevents interference with other network interfaces.
Step 3: Launching mitmproxy Container
With the Docker network set up, it's time to launch the mitmproxy container. This step will guide you through the process of running the container and configuring it to intercept and analyze the desired network traffic.
Note: The mitmproxy container can be customized based on specific requirements, such as SSL interception, traffic manipulation, and script integration.
Step 4: Configuring Client Devices
Now that the mitmproxy container is up and running, we need to configure the client devices, such as browsers or mobile devices, to redirect the network traffic to the proxy. This will enable mitmproxy to intercept and analyze the traffic passing through.
Note: Configuring the client devices may require adjusting proxy settings or installing trusted SSL certificates.
Step 5: Intercepting and Analyzing Network Traffic
Once everything is set up, it's time to start intercepting and analyzing the network traffic through mitmproxy. This step will guide you through the process of navigating mitmproxy's user interface and utilizing its powerful features for tasks like inspecting requests and responses, modifying traffic, and running custom scripts.
Note: Take advantage of mitmproxy's numerous features to gain insights into network communications and perform various security and development tasks.
By following these steps, you can successfully set up and run mitmproxy Docker in Windows Subsystem for Linux (WSL), leveraging the benefits of both Docker technology and the powerful intercepting proxy capabilities provided by mitmproxy.
Introduction to mitmproxy: A Powerful Network Traffic Intercepting Tool
mitmproxy is a versatile and robust tool used for intercepting, analyzing, and modifying network traffic. It provides a comprehensive solution for understanding and manipulating communication between various devices on a network. With mitmproxy, you can gain invaluable insights into the data exchanged between clients and servers.
Understanding network traffic is crucial when it comes to conducting security assessments, debugging applications, or performing network analysis. By intercepting and inspecting traffic, mitmproxy allows you to examine HTTP, HTTPS, WebSocket, and other protocols, enabling you to gain a deeper understanding of how your applications or services interact with the network.
mitmproxy acts as a man-in-the-middle (MITM) proxy, sitting between the client and the server, intercepting and forwarding requests and responses. It provides a user-friendly interactive console and a powerful scripting API, making it an ideal choice for both beginners and advanced users.
Common use cases for mitmproxy include:
- Analyzing and debugging web applications
- Inspecting and modifying API requests and responses
- Testing mobile application traffic
- Reverse engineering and analyzing network protocols
- Simulating network conditions for testing
Whether you are a developer, security researcher, or network administrator, mitmproxy can greatly enhance your capabilities by providing an intuitive and flexible platform for analyzing and manipulating network traffic. By gaining insights into the communication between devices, you can identify vulnerabilities, improve security, and optimize performance.
Installing Docker in Windows Subsystem for Linux
In this section, we will explore the process of setting up Docker in the Windows Subsystem for Linux environment. By following these steps, you will be able to utilize Docker's containerization capabilities within the Linux environment on your Windows machine.
The installation of Docker in the Windows Subsystem for Linux involves a series of steps that ensures a seamless integration of the Docker platform. These steps include preparing the Linux environment, installing the necessary dependencies, and configuring Docker to work within the Windows environment.
First, we need to configure the Linux environment. This involves enabling the Windows Subsystem for Linux feature and selecting a Linux distribution to install. Once the Linux environment is set up, we can proceed by updating the system and installing the required dependencies, such as the kernel headers, build essentials, and package management tools.
Next, we need to download and install Docker. This can be accomplished by retrieving the Docker repository key and adding it to the Linux software repository list. With the repository configured, we can proceed to install Docker using the package manager of our chosen Linux distribution.
After successfully installing Docker, we need to configure it to work seamlessly within the Windows environment. This involves modifying the Docker daemon configuration file to use Windows paths and ensuring that the necessary runtime components are in place. Additionally, we may need to configure environment variables to enable communication between Docker and the Windows Subsystem for Linux.
Once the configuration is complete, we can verify the successful installation and functionality of Docker by running basic Docker commands and checking for expected output. With Docker up and running in the Windows Subsystem for Linux, we can now take advantage of its powerful containerization capabilities for various development and deployment tasks.
By following the steps outlined in this section, you will be able to harness the benefits of Docker within the Windows Subsystem for Linux environment. This integration opens up a world of possibilities for building, deploying, and managing containers seamlessly in a Linux environment on your Windows machine.
Acquiring the mitmproxy Docker Image
The initial step towards working with mitmproxy in a Windows Bash environment involves obtaining the appropriate Docker image. By acquiring the mitmproxy Docker image, you will gain access to all the necessary components and dependencies required to seamlessly run and utilize mitmproxy.
To obtain the mitmproxy Docker image, you can follow the steps outlined below:
- Access a trusted and reliable Docker repository or registry.
- Search for the mitmproxy Docker image using relevant keywords or phrases such as "mitmproxy Docker image" or "mitmproxy container image".
- Review the available options and select the most appropriate version and variant of the mitmproxy image. Ensure that it is compatible with your Windows Bash environment.
- Retrieve the Docker image's download command or instructions from the repository.
- Open the Windows Bash terminal or command prompt and execute the provided command to start the download process.
- Wait for the download to complete. The speed may vary depending on your internet connection and the size of the Docker image.
- Verify the successful acquisition of the mitmproxy Docker image by listing the locally available Docker images using the appropriate command.
Once you have successfully obtained the mitmproxy Docker image, you will be ready to proceed with setting up and configuring mitmproxy within your Windows Bash environment.
Running the mitmproxy Docker Image in WSL
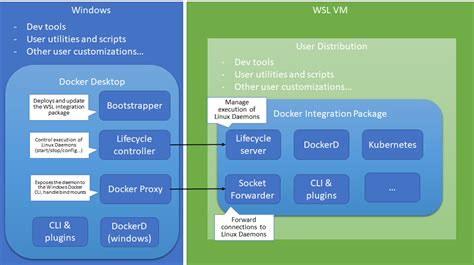
Exploring the possibilities of running the mitmproxy Docker image in the Windows Subsystem for Linux (WSL) opens the door to a wide range of networking and security capabilities. By leveraging the power of WSL, users can seamlessly interact with the mitmproxy Docker image and perform various tasks without the need for a virtual machine or a separate Linux environment.
With the seamless integration of mitmproxy Docker image in WSL, users can enhance their network monitoring and analysis workflows, intercept and inspect network traffic, simulate different network conditions, and even develop and test web applications securely.
Setting up and running the mitmproxy Docker image in WSL is straightforward. The first step involves ensuring that WSL is enabled on the Windows system. After that, obtaining the mitmproxy Docker image from the official Docker repository is a breeze. Once the image is downloaded and the necessary dependencies are installed, users can launch the mitmproxy container and start utilizing the powerful features it offers.
By following the recommended configuration and running the mitmproxy Docker image in WSL, users can take advantage of the vast array of features available, including capturing and modifying HTTP/HTTPS traffic, injecting scriptable code into requests and responses, and even generating SSL certificates on the fly. With these capabilities at their disposal, users can effectively monitor and secure their network communications.
Running the mitmproxy Docker image in WSL not only brings convenience and ease of use, but it also opens up new possibilities for network analysis and security tasks. Whether it's for testing, development, or simply gaining insights into network behaviors, leveraging the combination of mitmproxy and WSL can greatly enhance network-related workflows on Windows systems.
Configuring Your Network to Utilize mitmproxy
To successfully utilize the capabilities of mitmproxy, it is crucial to configure your network settings appropriately. By adjusting network configurations, you can ensure seamless interception of network traffic and gain valuable insights into data exchanges between clients and servers.
Here are some essential steps to configure your network effectively:
- Understanding your network infrastructure:
- Identify the various devices and components within your network, such as routers, switches, and access points.
- Recognize the different layers of your network, including the physical, data link, network, transport, and application layers.
- Comprehend how data flows through these layers and the points where mitmproxy can intercept and analyze the traffic.
- Take into account the security measures implemented in your network, as they might affect mitmproxy's functionality.
- Identify the specific devices or applications you wish to monitor with mitmproxy.
- Redirect the network traffic from these devices or applications towards the machine running mitmproxy.
- Configure routing tables, proxies, or other network settings to ensure the traffic is directed to the appropriate machine.
- Consider the network topology and adjust the settings accordingly to ensure smooth traffic redirection.
- Understand the SSL/TLS certificate trust hierarchy in your network.
- Install the mitmproxy root certificate on the devices or applications you want to intercept HTTPS traffic from.
- Configure the devices or applications to trust the mitmproxy certificate, allowing successful SSL/TLS interception.
- Take necessary precautions and ensure the secure handling of the mitmproxy root certificate to maintain the network's integrity.
- Start mitmproxy on the designated machine to begin intercepting and analyzing network traffic.
- Monitor the traffic exchanged between the clients and servers in your network.
- Inspect HTTP/HTTPS requests and responses, analyzing their content, headers, and other relevant details.
- Implement appropriate filters and rules to selectively capture the desired network traffic for in-depth analysis.
By following these steps and configuring your network accordingly, you can fully leverage the capabilities of mitmproxy and gain valuable insights into your network's data exchanges.
Exploring the Potential of mitmproxy in Windows Applications
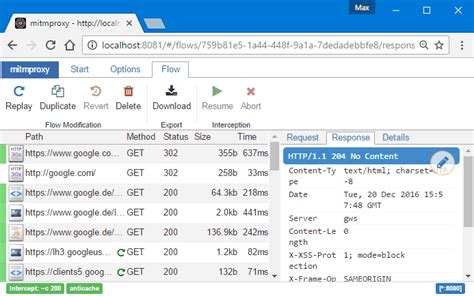
Operating systems play a crucial role in enabling the smooth functioning of modern software applications. This article aims to shed light on the possibilities of incorporating the powerful capabilities of mitmproxy into Windows applications. By leveraging the unique features of mitmproxy, developers can enhance the security, performance, and overall user experience.
- Unlocking Enhanced Security: With mitmproxy, Windows applications gain the ability to intercept, inspect, and modify network communication in real time. This unparalleled level of visibility enables developers to identify and address potential security threats, including vulnerabilities, malicious activities, and data breaches.
- Enhancing Performance and Monitoring: By incorporating mitmproxy in Windows applications, developers gain valuable insights into their network traffic. This allows for performance optimization, identification of bottlenecks, and monitoring the behavior of third-party APIs or services, ultimately leading to a more efficient application.
- Enabling Seamless Debugging: The integration of mitmproxy in Windows applications facilitates the identification and resolution of issues during the development and testing phases. By intercepting and manipulating requests and responses, developers can simulate specific scenarios, debug errors, and ensure smooth interaction with external systems.
- Implementing Custom Features: The flexibility of mitmproxy enables the customization of network requests and responses within Windows applications. This empowers developers to implement tailored features such as traffic shaping, protocol manipulation, or dynamic content injection, enhancing the overall functionality and user experience.
- Fostering Collaboration and Learning: Integrating mitmproxy in Windows applications not only benefits individual developers but also enhances collaboration within teams. By sharing knowledge, addressing specific challenges, and leveraging the vast mitmproxy community, developers can expand their skills and continuously improve their applications.
By harnessing the potential of mitmproxy, Windows applications can elevate their capabilities in terms of security, performance, and user experience. With its unique features and adaptability, mitmproxy opens up a world of possibilities for developers, enabling them to create robust and efficient applications that cater to the demands of today's dynamic digital landscape.
Troubleshooting and Tips for Utilizing mitmproxy Docker in WSL
When working with mitmproxy Docker in the Windows Subsystem for Linux (WSL), it is important to be aware of potential obstacles that may arise. This section provides troubleshooting strategies and valuable tips to enhance your experience and maximize the effectiveness of mitmproxy Docker within the WSL environment.
1. Network Configuration: Ensure that your network settings in WSL are properly configured for seamless communication with the mitmproxy Docker container. Double-check that your WSL instance has the necessary network permissions and can access the internet without any restrictions.
2. Permissions and Mounting Volumes: Take note of the file and folder permissions when working with volumes and mounting them to the Docker container. This is crucial to ensure that mitmproxy Docker has the required access to directories for intercepting and inspecting network traffic effectively.
3. Container Startup: While starting the mitmproxy Docker container, monitor the console output for any potential errors or warnings. These messages can provide valuable insights into potential issues and may aid in troubleshooting. Moreover, be mindful of possible conflicts with existing containers or other services that may be running on the system.
4. Proxy Configurations: Verify that the proxy configurations within the WSL environment align with the mitmproxy Docker settings. Consistency in proxy configurations is essential to ensure that network traffic is appropriately intercepted and forwarded to mitmproxy Docker for inspection.
5. Certificate Configuration: Adjust the certificate settings within the WSL instance to ensure smooth communication between the mitmproxy Docker container and the web applications being tested. Proper certificate configuration is particularly significant when dealing with HTTPS traffic interception.
6. Troubleshooting Tools: Familiarize yourself with various troubleshooting tools available in WSL to efficiently diagnose and resolve issues. Utilize tools such as ping, curl, and dig to confirm network connectivity and troubleshoot DNS-related problems. Additionally, leverage the mitmproxy documentation and online resources to address specific challenges.
7. Environment Updates: Regularly update both the WSL environment and the mitmproxy Docker container to access the latest features, bug fixes, and security enhancements. Staying up to date helps ensure a smoother and more reliable experience while working with mitmproxy Docker in WSL.
By considering these troubleshooting strategies and implementing the suggested tips, you can enhance your usage of mitmproxy Docker within the Windows Subsystem for Linux environment, enabling efficient network traffic analysis and testing.
Docker Tutorial for Beginners
Docker Tutorial for Beginners by Programming with Mosh 2,437,739 views 3 years ago 56 minutes
FAQ
What is mitmproxy docker?
Mitmproxy docker is a tool that allows users to intercept, inspect, and modify network traffic between their device and a server. It acts as a proxy, enabling the user to monitor and analyze all incoming and outgoing data.
Why would I want to use mitmproxy docker?
Mitmproxy docker provides a convenient way to analyze and debug network traffic. It allows you to see the requests and responses between your device and the server, making it easier to troubleshoot issues, test security vulnerabilities, or analyze the performance of your network-connected applications.
Are there any prerequisites to using mitmproxy docker on Windows Bash?
Yes, there are a few prerequisites to using mitmproxy docker on Windows Bash. Firstly, you need to have Docker installed on your Windows system. Additionally, you should be familiar with using Bash commands and have a basic understanding of networking concepts to effectively use mitmproxy docker.




