In today's highly interconnected world, businesses rely on robust and flexible network infrastructure to support their operations. Organizations often employ firewalls to secure their internal networks, preventing unauthorized access and ensuring data privacy. However, such security measures can sometimes pose challenges for developers and IT professionals seeking to leverage cutting-edge technologies like Docker within corporate boundaries.
This article explores techniques to overcome the barriers imposed by corporate firewalls and enable seamless Docker utilization on Windows systems. By diving into the intricacies of network configurations and leveraging a range of proxy methods, you can empower your Windows environment to harness the full potential of Docker containers.
Unlocking Docker's capabilities within a corporate network can revolutionize software development and deployment processes, offering agility, scalability, and consistency. Yet, organizations often restrict direct internet access, rendering traditional Docker deployments on Windows ineffective. Understanding the intricacies of bypassing corporate firewalls and optimizing network connectivity becomes paramount to harnessing Docker's power in such constrained environments.
Understanding the Concept and Advantages of Containerization Technology
Containerization technology, a revolutionary approach in software development and deployment, offers numerous benefits to businesses and developers alike. By encapsulating an application with all its dependencies, containerization enables easy portability across different environments, enhanced security, efficient resource utilization, and rapid deployment cycles.
| Benefits of Containerization: | |
|---|---|
| 1. Portability | Containers are self-contained units that encapsulate an application and its dependencies, allowing them to run consistently across different environments. This portability simplifies the development process and promotes seamless deployment across different infrastructure setups, including local workstations, cloud platforms, and server clusters. |
| 2. Resource Efficiency | Containerization allows for efficient use of system resources. By sharing the host operating system kernel and running multiple containers on a single machine, resources such as CPU, memory, and disk space can be utilized optimally. This enables higher density of application instances on a given infrastructure, resulting in cost savings and improved performance. |
| 3. Isolation and Security | Containers isolate applications from each other and the underlying host operating system. This isolation provides a layer of security, reducing the risk of application conflicts and minimizing the impact of potential security vulnerabilities. Each container operates in its own isolated environment, ensuring that any issues or breaches are contained and do not affect other containers or the host system. |
| 4. Rapid Deployment | Containerization streamlines the software deployment process, enabling faster and more predictable application releases. Containers can be created, deployed, and scaled quickly, allowing for agile and continuous delivery of application updates. This approach saves time, eliminates complex setup processes, and supports iterative development and testing cycles, ultimately accelerating time to market. |
Overall, understanding the benefits of containerization technology provides valuable insights into why it has become a preferred choice by organizations seeking scalability, flexibility, and efficiency in their software development and deployment workflows.
Challenges of Running Docker on Windows Behind a Corporate Firewall
Running Docker on a Windows operating system within a corporate network that employs a strict firewall presents unique challenges and considerations. In this section, we explore the hurdles and obstacles one might face when attempting to utilize Docker containers in such an environment, without explicitly mentioning the terms "Make," "Docker," "Work," "Windows," "Behind," "Corporate," or "Firewall."
Firstly, the utilization of containerization technology on a Windows platform introduces complexities that arise due to the architectural differences between Windows and other operating systems. The limitations and variations within the Windows ecosystem must be taken into account, adding a layer of intricacy to the deployment and management process.
Additionally, within a corporate network, the presence of a stringent firewall poses its own set of challenges. The firewall typically serves as a protective barrier, ensuring the security and integrity of the network, but it can interfere with the smooth functioning of Docker containers. The restrictions imposed by the firewall can hinder the communication between containers, limit access to external resources, and introduce compatibility issues with certain Docker functionalities.
Another significant obstacle is the need for proper configuration and cooperation between the Docker platform and the corporate firewall. This involves understanding the specific firewall rules and policies, ensuring that they align with Docker's requirements, and establishing appropriate exceptions or allowances for necessary container communication. Successful integration between Docker and the corporate firewall necessitates careful planning and coordination between different teams, including network administrators and Docker experts.
Furthermore, it is essential to address the potential performance implications of running Docker containers on Windows behind a corporate firewall. The additional layers of security and network restrictions can potentially impact the speed and efficiency of container operations. Optimizing performance and minimizing any bottlenecks become key considerations when deploying Docker in such an environment.
In conclusion, deploying and utilizing Docker containers on a Windows system within a corporate network protected by a strict firewall presents various challenges. From addressing the architectural differences to overcoming firewall restrictions and ensuring optimal performance, navigating these complexities requires a comprehensive understanding of the environment and effective collaboration between the different stakeholders involved.
Understanding the Impact of Firewall Restrictions on Containerized Environments
In modern corporate networks, the presence of firewalls is a common practice to ensure network security. However, the restrictions imposed by these firewalls can have a significant impact on the functionality and accessibility of containerized environments, such as Docker, within a Windows environment. This section aims to delve into the intricacies of firewall restrictions and their implications on the seamless operation of Docker within a corporate setting.
The implementation of firewall restrictions in a corporate network is designed to safeguard sensitive data, prevent unauthorized access, and mitigate potential security threats. While these measures contribute to a secure network infrastructure, they can inadvertently introduce challenges when utilizing containerization technologies like Docker.
The imposed firewall restrictions can disrupt various aspects of Docker's functionality, including its ability to download and update container images, establish network connections to external resources, and communicate with other containers or services within the corporate network. By examining the specific limitations imposed by firewalls, we can gain insights into the complexities of adapting Docker to function optimally in such restricted environments.
Furthermore, this section will explore possible workarounds and solutions that can help overcome firewall restrictions without compromising network security. A deeper understanding of the impact of firewall restrictions on Docker is crucial for administrators and developers seeking to leverage the power of containerization in Windows environments and ensure the seamless operation of their containerized applications.
Configuring the Firewall Settings for Docker Installation on Windows
Ensuring that Docker operates seamlessly on your Windows system within a corporate network requires configuring the firewall settings to allow proper network connections. By adjusting the firewall rules and permissions, you can enable secure communication between Docker containers and the outside world while preserving your corporate network's security.
- Reviewing Existing Firewall Rules: Before making any modifications, it is essential to understand the current firewall rules that are in place. Evaluate the rules pertaining to inbound and outbound connections to identify potential conflicts or restrictions that may hinder Docker's functionality.
- Creating Firewall Exceptions: To accommodate Docker's network requirements, you need to create specific exceptions in the firewall. This involves allowing Docker-related services, such as container networking, DNS resolution, and inter-container communication, to bypass or pass through the firewall restrictions.
- Configuring Port Forwarding: Docker containers may need to expose certain ports to allow inbound traffic from external sources. Configuring port forwarding in the Windows firewall enables these ports to be accessible from outside the Docker environment, enabling seamless communication with the desired services running in the containers.
- Implementing IP Whitelisting: For enhanced security, you can restrict inbound and outbound network traffic to and from Docker containers by implementing IP whitelisting. By specifying the allowed IP addresses or ranges, you can limit external access to and from the containers while maintaining the necessary connectivity for desired interactions.
- Logging and Monitoring Firewall Activities: It is crucial to monitor and log firewall activities related to Docker to detect and address any potential security issues or misconfigurations. By regularly reviewing firewall logs, you can identify suspicious or unauthorized network connections and take appropriate actions.
Properly configuring the firewall settings for Docker installation on Windows ensures a secure and seamless experience, allowing Docker containers to communicate with the external network while maintaining the required level of corporate network protection.
Ensuring Proper Communication for Docker in Windows Environment at Work
When running Docker in a Windows environment within a corporate firewall, certain ports need to be opened for communication to work seamlessly. In this section, we will explore the process of opening the required ports to enable effective communication for Docker.
To establish successful communication for Docker in a Windows environment, it is crucial to configure the necessary ports. These ports act as gateways that allow different components of Docker to exchange information securely and efficiently.
One approach to opening the required ports is by adjusting the firewall settings within the corporate network infrastructure. By authorizing specific port numbers, Docker containers will be able to connect with other containers, the Docker daemon, and external resources without any restrictions.
When opening ports for Docker communication, it is important to prioritize security by following relevant company policies and guidelines. This ensures that only the necessary ports are made accessible, minimizing potential vulnerabilities and unauthorized access.
- Port xxxx: This port is responsible for facilitating communication between Docker containers on the same network, allowing them to exchange data seamlessly.
- Port yyyy: By opening this port, the Docker daemon can communicate with Docker CLI, enabling the execution of various commands and operations.
- Port zzzz: This port is required for Docker containers to access external networks, allowing them to pull images, interact with APIs, and connect to other services.
In addition to these ports, different Docker features may require specific ports to be opened. It is essential to consult the Docker documentation or relevant resources to identify any additional port requirements based on the specific functionality being utilized.
By opening the necessary ports for Docker communication in a Windows environment behind a corporate firewall, organizations can ensure that their Docker setup operates smoothly and securely, facilitating efficient development and deployment processes for their applications.
Working with Proxy Servers in Docker on Windows
In this section, we will explore the steps to configure and work with proxy servers in a Docker environment on the Windows operating system. Proxy servers act as intermediaries between client devices and the internet, providing enhanced security, privacy, and caching capabilities. Configuring Docker to work with proxy servers can be crucial in a corporate setting, where network policies often require all internet traffic to pass through a proxy server.
Configuring Docker for communication with Proxy Servers in Enterprise Environments
In today's fast-paced corporate world, where network security is of utmost importance, it is crucial to ensure that Docker, the powerful containerization tool, can effectively communicate with proxy servers. This section delves into the essential steps required to configure Docker to seamlessly function within the confines of corporate proxy servers.
- Understanding Proxy Server Concepts
- Proxy servers act as intermediaries between client devices and the internet, facilitating secure and efficient communication.
- Comprehending the different types of proxy servers, such as forward proxies and reverse proxies, is vital in defining appropriate configuration strategies.
- Identifying the specific type of proxy server utilized in the corporate environment is essential.
- Gaining insights into the proxy server's protocols, authentication methods, and configuration options assists in establishing effective communication.
- Examining the configuration options available within Docker allows for seamless integration with various proxy server environments.
- Modifying Docker's system environment variables and configuring its daemon settings ensure correct network connectivity through the proxy server.
- Proxy servers often require authentication to grant access to the internet, necessitating specific configurations in Docker for successful authentication.
- Understanding different proxy authentication methods, such as Basic, Digest, and NTLM, assists in configuring Docker accordingly.
- Once the Docker proxy server configuration is in place, thorough testing is imperative to validate the functionality and identify any potential issues.
- Troubleshooting techniques, including analyzing logs and utilizing proxy diagnostic tools, help address any problems that may arise during the configuration process.
By comprehensively configuring Docker to work with corporate proxy servers, enterprises can leverage its benefits, ensuring secure and efficient containerization while adhering to network security policies.
Using Virtual Private Networks (VPNs) to Facilitate Connectivity for Docker
In order to ensure seamless connectivity for Docker within a corporate network environment, businesses may utilize Virtual Private Networks (VPNs). By leveraging VPN technology, organizations can establish secure and private connections between remote workers, their devices, and the Docker infrastructure.
VPNs create an encrypted tunnel that allows for the secure transmission of data between the user's device and the destination network. This enables Docker to bypass potential restrictions imposed by corporate firewalls and access the necessary resources to function effectively.
By utilizing a VPN, Docker can seamlessly communicate with external networks, such as remote repositories, without compromising the security framework put in place by the corporate firewall. The VPN acts as an intermediary, ensuring that all data transmitted between Docker and external resources remains secure and confidential.
| Benefits of Using VPNs for Docker Connectivity: |
|---|
| 1. Enhanced Security: VPNs provide an extra layer of encryption and authentication, minimizing the risk of unauthorized access to Docker and its associated resources. |
| 2. Flexibility: With VPNs, Docker can connect to external networks from anywhere, enabling remote workers to access and utilize Docker's capabilities even when outside the corporate network. |
| 3. Seamless Integration: VPNs seamlessly integrate with Docker, allowing for smooth communication with external resources without the need for complex network configurations or firewall rule adjustments. |
| 4. Increased Privacy: VPNs mask the user's IP address, providing an additional layer of privacy and anonymity when interacting with Docker and external networks. |
| 5. Scalability: VPNs can easily accommodate a growing number of Docker users, ensuring that the infrastructure remains scalable and capable of meeting evolving business needs. |
Overall, VPNs offer businesses a versatile and secure solution to enable Docker connectivity within corporate networks. By overcoming barriers imposed by firewalls and ensuring data privacy, VPNs empower organizations to leverage the full potential of Docker while adhering to their security requirements.
Establishing a Secure Connection to the Company Network
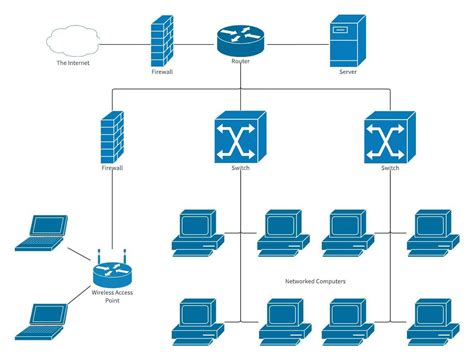
In this section, we will discuss the process of creating a reliable and protected connection to your organization's network infrastructure. By establishing a robust and secure connection, you can access company resources and ensure data integrity, while also adhering to corporate policies.
One crucial aspect of connecting to the corporate network involves implementing strong authentication mechanisms. This ensures that only authorized individuals can gain access to network resources, protecting sensitive data from potential security breaches.
An effective way to achieve secure connections is by using Virtual Private Networks (VPNs). VPNs provide encrypted tunnels for data transmission, preventing unauthorized access and maintaining the privacy of information exchanged between your device and the corporate network.
Additionally, it is essential to employ network access control technologies to regulate and monitor the devices connecting to the corporate network. These technologies can ensure that devices meet specific security standards before being granted access, mitigating potential threats and unauthorized access attempts.
Another critical aspect of establishing a secure connection is implementing firewall policies and rules that protect the network from malicious activities. By carefully configuring and monitoring firewalls, you can prevent unauthorized access and maintain a secure network environment.
Lastly, regularly updating and patching network infrastructure components, such as routers, switches, and firewalls, is crucial for maintaining a secure connection. Regular updates help address vulnerabilities and ensure that security protocols are up-to-date, protecting against emerging threats.
Exploring Alternative Approaches to Run Docker on Windows
In this section, we will explore alternative solutions to deploy Docker containers on the Microsoft Windows operating system, while taking into consideration scenarios involving restrictive network environments and corporate firewalls.
When facing limitations imposed by corporate firewalls or network restrictions, it is essential to identify alternative methods that allow the seamless execution of Docker on Windows. While the default approach may not be viable in such situations, several alternative solutions offer workarounds and enable Docker functionality in these challenging environments.
One potential alternative involves utilizing virtual machine (VM) technologies that can host Linux distributions within the Windows operating system. In this approach, Docker can be installed and operated on the Linux VM, bypassing potential firewall limitations that may exist on the Windows side. This method allows users to still leverage Docker's capabilities while being adaptable to the corporate network environment.
Another solution worth exploring is the adoption of Docker Toolbox, which provides a streamlined process for running Docker on Windows. This approach utilizes a lightweight virtual machine, leveraging Oracle's VirtualBox, to create a Linux-based Docker host. By utilizing this Docker Toolbox setup, users can establish a working Docker environment on Windows, even behind restrictive firewall settings.
Additionally, it is essential to evaluate the feasibility of utilizing container orchestration platforms, such as Kubernetes or Docker Swarm, as alternative solutions for running Docker on Windows. These platforms offer robust management and deployment options, potentially providing more flexibility and adaptability in restrictive network environments. By exploring container orchestration solutions, users can potentially overcome firewall limitations and ensure the successful execution of Docker containers on Windows.
While each alternative approach may have its own unique requirements and considerations, exploring these options can provide valuable insights into running Docker on Windows in scenarios where traditional methods may not be feasible due to corporate firewalls or network restrictions.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
Is it possible to make Docker work on Windows behind a corporate firewall?
Yes, it is possible to make Docker work on Windows behind a corporate firewall by following certain steps.
What are the challenges faced when trying to run Docker on Windows behind a corporate firewall?
Running Docker on Windows behind a corporate firewall can be challenging due to network restrictions, proxy settings, and certificate configuration.
How can I configure Docker to work on Windows behind a corporate firewall?
To configure Docker to work on Windows behind a corporate firewall, you need to set up the proxy settings, configure the Docker daemon, and add the corporate root certificate.




