In today's digital landscape, where data breaches and cyberattacks pose an ever-increasing threat, ensuring the security of our applications and sensitive information has become paramount. As developers and system administrators, we have a responsibility to protect our software environments from potential vulnerabilities.
One crucial aspect of securing our applications is the implementation of SSL/TLS certificates, which establish an encrypted connection between a client and a server, safeguarding the data in transit. By encrypting data, SSL/TLS certificates ensure that it cannot be intercepted or tampered with during transmission. This technology has become instrumental in guaranteeing secure communication over the internet.
While SSL/TLS certificates are commonly used within web servers, their implementation for Docker containers and Dockerfiles in a Windows environment can bring an additional layer of security to our containerized applications. By utilizing SSL/TLS certificates, we can protect sensitive information, such as API keys, login credentials, and user data, even within the dynamic and scalable world of containerization.
In this article, we will explore the intricacies of setting up SSL/TLS certificates for Docker containers and Dockerfiles on the Windows platform. We will delve into the steps involved in generating and installing SSL/TLS certificates, as well as demonstrate how to configure containers and Dockerfiles to use these certificates for secure communication. By the end of this article, you will have a thorough understanding of how to implement SSL/TLS certificates within your Windows-based Docker environment, empowering you to fortify your applications and protect your users' sensitive data.
Advantages of Implementing SSL/TLS Security for Docker Deployment on Windows
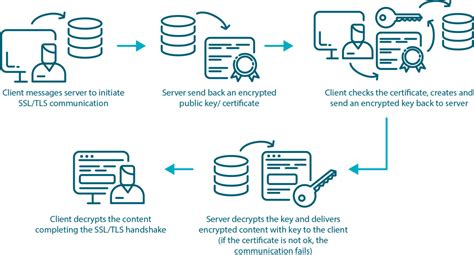
In today's digital era, ensuring secure communication and data privacy has become paramount. It is crucial to adopt robust security measures, such as SSL/TLS certificates, when it comes to deploying Docker containers and Dockerfiles on Windows environments.
| Enhanced Data Protection | SSL/TLS certificates provide a secure channel for data transmission, preventing unauthorized access and mitigating the risk of eavesdropping, interception, or tampering. By encrypting the communication between Docker containers and external entities, you can safeguard sensitive information, like login credentials or customer data, from potential breaches. |
| Trust and Authentication | Implementing SSL/TLS certificates establishes trust in your Docker deployment by verifying the identity of the entities involved. The use of certificates enables mutual authentication, ensuring that both the client and server can validate each other's identities. This adds an extra layer of protection, preventing man-in-the-middle attacks and unauthorized access attempts. |
| Compliance with Security Regulations | SSL/TLS encryption is a fundamental requirement for compliance with various security regulations and industry standards. By adhering to these standards, such as the Payment Card Industry Data Security Standard (PCI DSS) or General Data Protection Regulation (GDPR), you can demonstrate your commitment to data privacy and avoid potential penalties. |
| Securing Communication Across Networks | SSL/TLS certificates enable secure communication not only within a containerized environment but also across networks. This ensures that data remains protected during transit, even when containers are deployed across different nodes or in cloud environments. By encrypting data at the transport layer, SSL/TLS certificates add an extra level of security to your Docker deployment. |
Overall, incorporating SSL/TLS certificates into your Docker deployment on Windows not only safeguards sensitive information but also establishes trust, ensures regulatory compliance, and secures communication across networks. By prioritizing security, you can create a robust and resilient Docker environment, enhancing the overall integrity and confidentiality of your applications and data.
Importance of Securing Docker Instances and Deployment Files
Ensuring the security of Docker containers and deployment files is of utmost importance in today's digital landscape. Safeguarding these elements helps protect sensitive data, prevent unauthorized access, and maintain the integrity of your application infrastructure.
Securing your Docker instances and deployment files involves implementing robust security measures to defend against potential threats and vulnerabilities. This includes utilizing encryption protocols, employing authentication mechanisms, and applying strong access controls.
Why is securing Docker instances and deployment files crucial?
One primary reason is to protect your network from malicious activities such as unauthorized access, data breaches, and cyber attacks. By securing Docker instances and deployment files, you can minimize the potential risks and mitigate any potential damage that could arise.
Another reason is to ensure compliance with industry standards and regulations.
Many industries have specific security requirements that need to be met, such as HIPAA for healthcare, GDPR for data privacy, or PCI DSS for payment card industry compliance. By effectively securing Docker instances and deployment files, you can adhere to these standards and ensure the confidentiality, integrity, and availability of your data.
Moreover, securing Docker instances and deployment files helps build trust with your customers and users. When they know that their data is being handled securely, they will have increased confidence in your services and be more likely to engage with your applications.
How can you secure Docker instances and deployment files?
There are several steps you can take to enhance the security of your Docker infrastructure. This includes implementing SSL/TLS certificates, which encrypt communication between containers and protect sensitive data from unauthorized interception.
In addition, regularly updating and patching your Docker environment, monitoring and logging activities, and following security best practices are essential for maintaining a secure Docker deployment.
By prioritizing the security of your Docker instances and deployment files, you can safeguard your applications, protect sensitive data, and ensure a resilient and trustworthy environment for your users.
Exploring the role of SSL/TLS Certificates in Ensuring Secure Communication
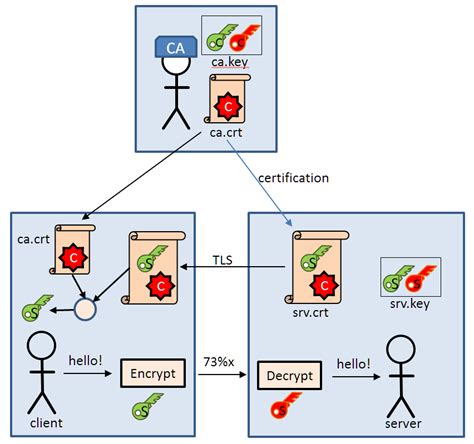
With increasing concerns about data security and the growing number of cyber threats, the need for secure communication has become paramount. SSL/TLS certificates play a critical role in establishing and maintaining a secure connection between servers and clients.
When it comes to data exchanges over the internet, the main objective is to ensure that information stays confidential, integrity is maintained, and it is transmitted between trusted parties. SSL/TLS certificates provide the necessary mechanisms to achieve these goals.
By encrypting data in transit, SSL/TLS certificates protect sensitive information from being intercepted or tampered with by unauthorized entities. This encryption is made possible through the use of cryptographic algorithms, which ensure that only the intended recipient can decrypt and access the data.
Additionally, SSL/TLS certificates enable authentication, allowing the verification of the identities of both servers and clients. This verification is crucial in establishing trust between the communicating parties and mitigating the risk of man-in-the-middle attacks.
In an age where cyber attacks are increasingly sophisticated, SSL/TLS certificates serve as a fundamental tool in safeguarding sensitive information and maintaining the integrity of digital communications. Understanding their role and implementing them appropriately can significantly enhance the security of Docker containers and Dockerfiles in Windows environments.
It is important to note that SSL/TLS certificates are not a one-time solution. To ensure ongoing security, regular certificate management, including renewals and updates, is necessary. Furthermore, choosing reputable certificate authorities and following best practices when configuring SSL/TLS protocols and cipher suites is vital to establish strong encryption and protect against emerging threats.
Emphasizing the significance of SSL/TLS certificates in securing communication within Docker containers and Dockerfiles is crucial for any organization that values data privacy, integrity, and customer trust. By implementing these certificates, organizations can establish secure channels and unleash the potential of robust and protected digital interactions.
Steps to Generate and Install SSL/TLS Certificates in Windows
In this section, we will outline the necessary steps to create and set up SSL/TLS certificates on a Windows operating system. By following these steps, you will be able to secure your applications and websites with encrypted connections, ensuring the privacy and integrity of your data.
Step 1: Generating a Certificate Signing Request (CSR)
To start the process, you will need to generate a Certificate Signing Request (CSR) which includes the necessary information to create the SSL/TLS certificate. This request is then sent to a Certificate Authority (CA) for validation and issuance of the certificate.
Step 2: Submitting the CSR to a Certificate Authority
Once you have obtained the CSR, you need to submit it to a trusted Certificate Authority. The CA will verify the requested information and perform the necessary checks to ensure the authenticity of the applicant. Once validated, the CA will issue the SSL/TLS certificate.
Step 3: Installing the SSL/TLS Certificate
After receiving the SSL/TLS certificate from the CA, you must install it on your Windows machine. This involves importing the certificate into the Windows Certificate Store, which will enable it to be used by the applications and services running on your system.
Step 4: Configuring SSL/TLS on Applications and Websites
Once the SSL/TLS certificate is installed, you need to configure your applications or websites to use the certificate for secure connections. This typically involves updating the application or web server settings to enable HTTPS and specify the location of the certificate files.
Step 5: Testing and Verifying the SSL/TLS Setup
Lastly, it is essential to test and verify the SSL/TLS setup to ensure that the encrypted connections are functioning correctly. This can be done by accessing the applications or websites using HTTPS and checking for the green padlock icon in the browser's address bar, indicating a secure connection.
By following these steps, you will be able to successfully generate and install SSL/TLS certificates on your Windows system, enhancing the security and trustworthiness of your applications and websites.
Configuring Docker Containers and Dockerfiles to Utilize Encryption Certificates

To enhance the security of your Docker containers and Dockerfiles, it is crucial to configure them to use encryption certificates. By implementing SSL/TLS certificates, you can establish a secure connection between your containers and external networks, safeguarding the confidentiality and integrity of the transmitted data.
Securing Containerized Communication
Ensuring the privacy of data exchanged between your Docker containers and external entities is essential in today's interconnected environment. By configuring your containers to utilize SSL/TLS certificates, you can encrypt communications, preventing unauthorized access and eavesdropping.
Enabling Authentication and Trust
SSL/TLS certificates not only encrypt data but also enable authentication and establish trust. By configuring your Docker containers to present valid certificates, you can verify the identity of the communicating parties and validate their authenticity. This authentication mechanism enhances the trustworthiness of your containerized applications.
Integrating Certificates into Dockerfiles
When setting up Docker containers, incorporating SSL/TLS certificates into the Dockerfiles is essential. By including the necessary steps to install and configure certificates within the Dockerfile, you can automate the deployment process and ensure that every container instance is equipped with the required certificates.
Customizing the Certificate Configuration
Every application and container environment may have specific certificate requirements. Configuring Docker containers and Dockerfiles to use SSL/TLS certificates involves tailoring the certificate settings to suit your unique needs. By adjusting parameters such as key lengths, cipher suites, and certificate authorities, you can optimize the security and performance of your containerized applications.
Deploying and Managing Certificate Authorities
In order to establish trust among containers and external entities, deploying and managing a Certificate Authority (CA) infrastructure is also necessary. This involves configuring Docker containers and Dockerfiles to recognize and trust the CA certificates. By centralizing the management of certificates, you can streamline the security and maintain the integrity of your Dockerized applications.
Monitoring and Updating Certificates
Regularly monitoring and updating SSL/TLS certificates is crucial to ensure ongoing security in your containerized environment. By configuring Docker containers and Dockerfiles to detect and handle expiring or compromised certificates, you can prevent potential security risks and maintain a robust and secure Docker infrastructure.
In conclusion, configuring Docker containers and Dockerfiles to utilize SSL/TLS certificates is vital for establishing secure and trusted communication channels. By incorporating encryption and authentication mechanisms into your containerized applications, you can enhance their security posture and protect sensitive data from unauthorized access.
Best Practices for Managing SSL/TLS Certificates in Docker Environment
In this section, we will explore the most effective strategies and recommendations for handling SSL/TLS certificates within Docker deployments. By following these best practices, you can ensure secure and reliable communication within your containerized applications.
1. Centralized Certificate Management:
One key approach is to adopt a centralized certificate management system that allows you to generate, distribute, and manage SSL/TLS certificates across your Docker containers. This ensures consistency and simplifies the certificate renewal process.
2. Secure Certificate Storage:
To safeguard sensitive SSL/TLS certificates, it is essential to store them securely. Utilize secure, encrypted storage solutions or tools specifically designed for managing certificates, such as HashiCorp Vault. This prevents unauthorized access and mitigates the risk of certificate compromise.
3. Regular Certificate Renewal:
SSL/TLS certificates have an expiration date, making regular renewal crucial for maintaining secure connections. Automate the certificate renewal process to avoid any downtime or security vulnerabilities caused by expired certificates.
4. Containerized Certificate Distribution:
When deploying containerized applications, consider using containerization technologies such as Kubernetes, which handle certificate distribution and management seamlessly. This enables secure communication between containers without manual intervention.
5. Implement Certificate Revocation:
In scenarios where an SSL/TLS certificate needs to be invalidated before its expiration date, implementing certificate revocation mechanisms, such as Certificate Revocation Lists (CRLs) or Online Certificate Status Protocol (OCSP), can safeguard against unauthorized access or compromised certificates.
6. Continuous Monitoring and Auditing:
Regularly monitor and audit your SSL/TLS certificate usage and validity. Implement automated monitoring systems to identify any certificate-related issues promptly. This ensures that your containers remain secure and trusted throughout their lifecycle.
By following these best practices, you can establish a secure and efficient SSL/TLS certificate management workflow within your Docker environment. These practices aim to streamline certificate handling, reduce risks associated with certificates, and ensure your containerized applications are protected against potential vulnerabilities.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
What is SSL/TLS certificate and why is it important for Docker containers?
SSL/TLS certificate is a digital certificate that authenticates the identity of a website or server and establishes an encrypted connection. It is important for Docker containers because it ensures secure communication between the containers and clients, protecting sensitive data from potential threats.
Can I use a self-signed SSL/TLS certificate for Docker containers?
Yes, you can use a self-signed SSL/TLS certificate for Docker containers. However, keep in mind that self-signed certificates are not trusted by default by web browsers and may result in security warnings. It is recommended to use a valid SSL/TLS certificate signed by a trusted CA for production environments.




