Are you ready to delve into the fascinating world of Lightweight Directory Access Protocol (LDAP) setup on your Linux server? This article will guide you through the intricacies of installing and configuring LDAP, enabling you to optimize the efficiency and security of your system. So, let's embark on this journey together and unlock the potential of LDAP!
Discover the Power of LDAP:
LDAP is a powerful directory service protocol that allows for centralized authentication, user and group management, and efficient data storage on your Linux server. By utilizing LDAP, you can ensure seamless access control, minimize redundancy, and enhance the reliability of your system. With its lightweight design and extensible nature, LDAP provides a scalable and flexible solution for managing directory information.
Unleash the Potential of Your Linux Server:
Through this comprehensive guide, we will equip you with the knowledge and skills needed to get LDAP up and running on your Linux-based system. You will learn the step-by-step installation process and gain insights on how to configure LDAP for optimal performance. From defining LDAP schemas to setting up access controls, we will cover every aspect to empower you with a deep understanding of LDAP configuration.
So, whether you are a system administrator seeking to streamline user authentication or a Linux enthusiast excited to explore new technologies, fasten your seatbelt as we embark on a journey into the realm of LDAP configuration on a Linux server!
Understanding the Significance of LDAP in Server Management
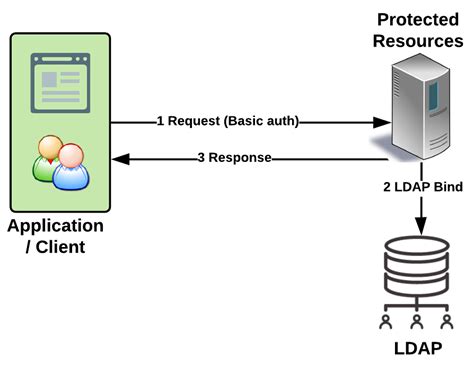
In the realm of server management, there exists a pivotal technology that plays a crucial role in authentication and authorization processes - LDAP (Lightweight Directory Access Protocol). This article aims to provide an in-depth understanding of LDAP's purpose and significance in the context of server management, shedding light on its various applications and benefits.
Defining LDAP:
LDAP, often referred to as the 'white pages' protocol due to its nature of storing directory information, serves as a standard protocol for accessing and managing directory services over a network. It offers a simplified and lightweight approach to directory access, allowing users to query and update information stored within a directory.
The Role of LDAP in Server Management:
LDAP serves as the backbone of server management, ensuring secure and efficient access to resources. By centralizing user account information and access controls, LDAP provides a centralized directory service that simplifies user management and enhances security. It paves the way for seamless integration with various applications, enabling administrators to easily configure and manage user access rights.
Benefits of LDAP in Server Management:
LDAP brings numerous benefits to server management. Firstly, it aids in the consolidation of user account information, streamlining administrative tasks and reducing the risk of inconsistencies. Additionally, LDAP's hierarchical structure allows for the organization and management of users and resources in a scalable and flexible manner.
Furthermore, LDAP facilitates secure authentication by implementing various encryption mechanisms, ensuring that user credentials are transmitted and stored securely. It enables fine-grained access control, granting administrators granular control over user permissions and facilitating effective resource sharing.
In conclusion, LDAP serves as a crucial component in server management, providing a centralized and secure directory service. Its role encompasses various aspects such as user management, access control, and authentication, contributing to streamlined administration and enhanced security.
Preparing the Operating System
Before diving into the installation and configuration of the LDAP server, it is important to ensure that the Linux operating system is properly prepared. This involves performing a series of steps to optimize the system for efficient LDAP management and security.
Firstly, it is recommended to update the operating system to the latest available version to ensure compatibility and access to the latest security patches and bug fixes. Additionally, it is important to install the necessary dependencies and libraries required for LDAP functionality.
After updating the system, it is crucial to create a non-administrative user specifically for managing the LDAP server. This helps to minimize potential risks and enhance security by isolating the LDAP server from privileged system accounts.
Furthermore, configuring the system's firewall to allow incoming LDAP connections and restricting access to authorized IP addresses can greatly enhance the security of the LDAP server. Implementing tight firewall rules and only allowing necessary connections can help prevent unauthorized access and potential attacks.
In conclusion, preparing the Linux server for LDAP installation and configuration involves updating the operating system, installing dependencies, creating a dedicated LDAP management user, and securing the server through firewall configuration. These steps lay the foundation for a stable and secure LDAP server environment.
Ensuring Compatibility and Updating System Requirements

Before proceeding with the installation and configuration of LDAP on your Linux server, it is essential to check the system requirements and ensure that the necessary updates are installed.
To ensure smooth operation and compatibility, it is recommended to thoroughly assess the system requirements and verify if your Linux server meets them. This entails checking the minimum Linux kernel version, available disk space, required memory, and compatible operating systems.
- Verify the compatibility of your server's operating system with the LDAP software.
- Check the minimum Linux kernel version required for the LDAP installation.
- Ensure that the server has sufficient disk space for the LDAP database and related files.
- Verify that the server's memory meets the recommended requirements for optimal LDAP performance.
Once you have ensured compatibility, the next step is to update your system to the latest patches and updates. Keeping your Linux server up to date is indispensable for security and stability. Regularly updating your system will provide you with bug fixes, enhancements, and improved performance.
It is highly recommended to use the package manager of your Linux distribution to update the system. This will allow you to easily apply all available updates and patches. Before proceeding, ensure that your server has an active and stable internet connection.
By checking the system requirements and installing necessary updates, you can ensure that your Linux server is ready for the smooth installation and configuration of LDAP.
Setting up OpenLDAP on a Linux-Based System
In this section, we will explore the process of installing and configuring OpenLDAP, an industry-standard protocol used for managing directory services, on a Linux-based server. This comprehensive guide will provide step-by-step instructions and best practices to successfully set up an OpenLDAP directory server.
First, we will cover the initial steps required to prepare the server environment for the installation process. This includes ensuring the server meets the necessary hardware and software requirements and installing any dependencies that may be needed for OpenLDAP to function correctly.
Next, we will guide you through the process of obtaining the OpenLDAP software package and its associated dependencies. We will explain how to download the package from a trusted source and verify its authenticity using cryptographic signatures. Once the package is obtained, we will show you how to unpack it and prepare the files for installation.
Once the software is ready, we will dive into the installation process, outlining the various installation methods available for OpenLDAP on Linux-based systems. We will provide detailed instructions on using package managers, such as apt or yum, as well as compiling and installing from source code.
After successfully installing OpenLDAP, we will focus on the initial configuration steps. This includes creating and configuring the main LDAP server instance, setting up the directory structure, and defining access control policies. We will explain the necessary configuration files, their locations, and how to modify them to tailor OpenLDAP to your specific needs.
Finally, we will discuss common troubleshooting tips and techniques to help you overcome any potential challenges or pitfalls you may encounter during the installation and configuration process. These insights will enable you to identify and resolve common issues, ensuring the smooth operation of your OpenLDAP server.
By following this guide, you will gain the knowledge and skills required to successfully install and configure OpenLDAP on a Linux-based server, enabling you to leverage the power and flexibility of LDAP for managing directory services in your organization.
A comprehensive guide to setting up the OpenLDAP package on a Linux-based system

In this section, we will take you through a step-by-step process of installing and configuring the OpenLDAP software package on your Linux server. By following these instructions, you will be able to set up a reliable and efficient LDAP (Lightweight Directory Access Protocol) system.
LDAP is a widely-used protocol for accessing and managing directory information. The OpenLDAP software package is a popular open-source implementation of this protocol, offering robust features and high performance for directory services. By installing and configuring OpenLDAP on your Linux server, you can centralize and manage user authentication, access control, and other directory-related functionalities.
Before we begin, it's important to note that this guide assumes you have a basic understanding of Linux system administration and have access to a Linux server. If you are unfamiliar with the Linux operating system, we recommend obtaining the necessary knowledge or seeking assistance from a qualified professional.
Throughout this guide, we will provide detailed instructions and explanations for each step, ensuring that even novice users can successfully install and configure OpenLDAP. We will cover topics such as package installation, configuring the LDAP directory, securing the connection, and managing user accounts and access control.
By the end of this guide, you will have a fully functional OpenLDAP installation on your Linux server, ready to support your directory needs.
Setting up and Customizing the LDAP Server
In this section, we will explore the process of configuring and tailoring the LDAP server to meet your specific needs. Our focus will be on customizing various aspects of the server to ensure optimal functionality and ease of use.
First, we will delve into the necessary steps of configuring the LDAP server, including determining the appropriate directory structure and defining access controls. We will discuss how to create and manage user accounts, groups, and organizational units, and how to assign permissions and privileges.
Next, we will explore the customization options available for the LDAP server. This includes configuring custom schemas, defining attribute types, and setting up object classes to suit the specific requirements of your organization. We will also cover the process of integrating the server with other applications and services, such as email clients and web servers.
Additionally, we will discuss the importance of security and delve into the various security measures that can be implemented to protect the LDAP server and its data. This includes securing network connections, implementing encryption, and enforcing strong password policies.
In conclusion, this section aims to provide you with a comprehensive understanding of how to configure and customize the LDAP server to suit your organization's unique needs. By following the guidelines and best practices outlined here, you can ensure a secure and efficient LDAP environment that seamlessly integrates with your existing infrastructure.
Efficient Management of the LDAP Server
In this section, we will explore the steps required to set up the LDAP server in order to achieve efficient management of user data and directory services. By implementing proper configurations and utilizing various techniques, organizations can enhance the performance and usability of their LDAP server, ensuring smooth and seamless operations.
To begin, it is essential to understand the importance of optimizing the LDAP server's settings. This includes fine-tuning the server parameters, such as cache size, network buffer size, and thread pool size, to achieve optimal resource utilization and responsiveness. Efficient management also involves implementing measures to improve search performance, such as configuring appropriate indexing strategies and optimizing search filters.
A crucial aspect of efficient LDAP server management is ensuring data security and integrity. This can be achieved through the implementation of proper access controls and strong authentication mechanisms. By carefully configuring access control lists (ACLs) and defining appropriate user permissions, organizations can effectively restrict unauthorized access and ensure that sensitive data remains protected.
Furthermore, efficient management of the LDAP server necessitates the establishment of reliable backup and recovery procedures. Regularly backing up the LDAP server's data and defining a solid disaster recovery plan will help mitigate the risk of data loss and ensure uninterrupted access to critical information. Organizations should also consider implementing monitoring and alerting mechanisms to proactively detect and address any performance or security issues that may arise.
Finally, the use of automation tools and scripts can significantly streamline administrative tasks and improve the overall efficiency of LDAP server management. These tools can assist in automating routine tasks, such as user provisioning and data synchronization, reducing administrative overhead and minimizing the potential for manual errors.
| Key Points: |
| - Optimize server settings for resource utilization and responsiveness. |
| - Enhance search performance through proper indexing and filter optimization. |
| - Implement robust access controls and authentication mechanisms for data security. |
| - Establish reliable backup and recovery procedures to safeguard critical data. |
| - Utilize monitoring and alerting mechanisms to proactively address performance or security issues. |
| - Automate administrative tasks using tools and scripts to improve efficiency. |
Creating and Managing LDAP Users
This section focuses on the process of creating and managing users in the Lightweight Directory Access Protocol (LDAP) system. By following these steps, you will be able to efficiently organize and control user access to your network resources. LDAP offers a streamlined approach to handling user information, providing a centralized directory for managing user accounts and their associated attributes.
To begin, it is essential to understand the key concepts of LDAP user management. User entries in an LDAP directory contain attributes that define their characteristics, such as username, password, email address, and other relevant information. These attributes are organized in a structured manner, allowing for easy retrieval and modification of user details.
Creating new LDAP users involves the process of adding user entries to the directory. This can be done using LDAP management tools or by writing LDIF (LDAP Data Interchange Format) files. Utilizing user templates can simplify user creation by providing predefined attribute values that can be customized as needed.
Once user entries have been created, it is crucial to manage them effectively. This includes modifying existing user attributes, such as updating contact information or changing passwords. Additionally, LDAP allows for user grouping, making it easier to apply user-specific policies and permissions.
In order to maintain accurate user information, it is important to regularly review and update user entries. This includes identifying and deactivating accounts that are no longer in use or belong to inactive users. By regularly managing LDAP users, you are able to ensure data integrity and minimize potential security risks.
In conclusion, creating and managing LDAP users is a fundamental aspect of maintaining an efficient and secure network environment. By understanding the concepts and following the recommended practices outlined in this section, you will be able to effectively organize and control user access to your resources.
Managing User Accounts in LDAP
In this section, we will explore how to add, modify, and delete user accounts within an LDAP directory. These operations are fundamental for maintaining a well-organized LDAP environment and ensuring efficient user management. By mastering these techniques, you will be able to seamlessly keep track of user accounts and their attributes, making necessary updates as required. Let's dive into the details below.
Adding User Accounts: When adding new user accounts to your LDAP directory, you need to ensure that the relevant attributes are correctly specified. These attributes typically include the user's name, email address, login credentials, and any additional information that is necessary for user authentication and identification. To facilitate the process, you can use various LDAP tools or utilities. One commonly used tool is the ldapadd command, which allows you to import LDIF (LDAP Data Interchange Format) files containing the necessary user account details. Alternatively, you can manually add user entries using an LDAP client, such as phpLDAPadmin or Apache Directory Studio.
Modifying User Accounts: As user account information evolves over time, it is crucial to be able to modify user attributes within the LDAP directory. This might involve updating a user's contact details, changing their password, or adjusting any other configurable attributes. To modify user accounts, one can use the ldapmodify command or LDAP client tools. These tools enable you to specify the desired changes to the user accounts through an LDIF file or an interactive interface. It is essential to practice proper caution and validate any modifications before applying them to ensure data integrity and accuracy.
Deleting User Accounts: When users leave an organization or are no longer required to have access to the LDAP system, their user accounts need to be appropriately removed. This process involves deleting the relevant user entry from the LDAP directory while ensuring that any dependencies or associated data are also accounted for. To effectively delete user accounts, one can use the ldapdelete command or LDAP client tools, which allow you to specify the entry to be deleted either through DN (Distinguished Name) or by using a filter statement. It is crucial to exercise caution when deleting user accounts to prevent accidentally removing the wrong entries or causing data inconsistencies.
| Operation | Command/Tool | Description |
|---|---|---|
| Adding User Accounts | ldapadd | Imports LDIF files or manually adds user entries to the LDAP directory |
| Modifying User Accounts | ldapmodify | Allows for modifications to user account attributes in the LDAP directory |
| Deleting User Accounts | ldapdelete | Removes user entries from the LDAP directory |
Managing LDAP Groups and Permissions
In this section, we will explore how to configure and manage groups and permissions within the LDAP environment. By utilizing LDAP groups, you can efficiently organize and control access rights for various users and resources. By assigning permissions to these groups, you can define what actions individual users can perform on specific resources.
Group Management:
Creating and managing LDAP groups is essential for effective user and resource management. You can create groups based on different criteria such as user roles, departments, or project teams. By organizing users into groups, you can easily assign and revoke permissions for multiple users simultaneously. Additionally, you can make use of nested groups to create hierarchical structures and streamline group management.
Example: Suppose you have an LDAP group named "EngineeringTeam" which consists of all the users belonging to the engineering department. You can assign specific permissions to this group, such as read access to engineering-related documents or write access to shared engineering project folders.
Permission Assignment:
Assigning permissions within LDAP involves linking specific access rights to individual groups or users. By defining the appropriate access controls for each group, you can ensure that users only have the necessary privileges required to perform their tasks. These access controls can include read, write, delete, or modify permissions, among others.
Example: Let's say you have an LDAP group called "Managers" who should have write access to a particular directory. By assigning the appropriate permission to this group, you can enable managers to create, edit, and delete files and folders within the specified directory.
By effectively managing LDAP groups and permissions, you can establish a robust and secure system that aligns with your organizational needs. These practices enable efficient user management, ensure proper access controls, and enhance overall security within your LDAP environment.
Creating groups and assigning permissions to LDAP users

In this section, we will explore the process of creating groups and assigning permissions to users in the LDAP directory on your Linux-based server. By organizing users into groups and defining their access rights, you can efficiently manage user permissions and ensure secure and controlled access to resources.
- To create a group, you can utilize the LDAP server's administrative tools or the command-line interface.
- When creating a group, it is important to assign a unique name and a meaningful description that accurately represents the purpose or role of the group.
- After creating the group, you can add LDAP users to the group by specifying their distinguished names (DNs) or unique identifiers (UIDs).
- Assigning permissions to LDAP users involves defining access rights for specific resources or functionalities based on the group they belong to.
- You can configure permissions at various levels, such as directory, file, or service level, depending on the specific requirements of your system.
- LDAP provides a flexible and customizable permission model that includes features like read, write, execute, create, or delete access permissions.
- By effectively organizing users into groups and assigning granular permissions, you can ensure the principle of least privilege and enhance the security of your Linux server.
- Regularly reviewing and updating group assignments and permissions is essential to accommodate changes in user roles or system requirements while maintaining a secure and efficient LDAP environment.
By following these guidelines, you can successfully create groups and assign permissions to LDAP users, enabling seamless user management and secure access control on your Linux server.
Enabling LDAP Authentication
In this section, we will explore the process of enabling LDAP authentication on your Linux-based system. LDAP authentication allows users to access various resources and services using a single set of login credentials stored in a centralized LDAP directory.
The first step in enabling LDAP authentication is to configure the LDAP client on your Linux server. This involves specifying the LDAP server address, port number, and any necessary security settings. Once the LDAP client is properly configured, the server will be able to communicate with the LDAP directory and authenticate users against it.
After configuring the LDAP client, the next step is to set up user accounts in the LDAP directory. Each user account will have a unique DN (Distinguished Name) within the LDAP directory structure. User attributes such as username, password, and group membership can be specified within the user account entries.
Once the user accounts are set up, it is important to test the LDAP authentication by attempting to log in with a sample user account. This will ensure that the LDAP client is properly connected to the LDAP directory and that the authentication process is functioning correctly.
In addition to basic authentication, LDAP can also be used for authorization purposes. By configuring the LDAP server to map LDAP groups to Linux system groups, you can control access to various resources based on group membership. This provides a centralized and flexible way to manage user permissions across multiple systems.
In summary, enabling LDAP authentication on your Linux server involves configuring the LDAP client, setting up user accounts in the LDAP directory, testing the authentication process, and utilizing LDAP groups for authorization. This allows for centralized user management and enhances security and efficiency in accessing resources on your Linux-based system.
Installation et Configuration du serveur LDAP server sous Ubuntu
Installation et Configuration du serveur LDAP server sous Ubuntu by Saad Bouayad 28,003 views 7 years ago 15 minutes
Configure LDAP on Debian 11 + WEB GUI interface config
Configure LDAP on Debian 11 + WEB GUI interface config by IT Wizard 1,702 views 1 year ago 48 minutes
FAQ
What is LDAP and why is it important to install and configure it on a Linux server?
LDAP stands for Lightweight Directory Access Protocol and it is a protocol used for accessing and managing directory information over a network. It is important to install and configure LDAP on a Linux server because it allows for centralized user authentication, management, and access control across multiple applications and systems.
Can you explain the steps to install LDAP on a Linux server?
Sure! To install LDAP on a Linux server, you first need to update the package lists, then install the necessary packages such as slapd and ldap-utils. Once the packages are installed, you need to configure LDAP by editing the slapd.conf file, which involves specifying the domain name, root DN, and other settings. After the configuration is complete, you can start the LDAP server and test it by performing basic queries.
What are the potential benefits of using LDAP for user management on a Linux server?
Using LDAP for user management on a Linux server offers several benefits. Firstly, it allows for centralized authentication, which means that users only need to remember one set of credentials. Secondly, LDAP provides a flexible and scalable solution that can handle large numbers of users and systems. Additionally, LDAP allows for easy integration with other applications and services, making it more convenient for administrators to manage user accounts.
Are there any security considerations when installing and configuring LDAP on a Linux server?
Yes, there are several security considerations to keep in mind when setting up LDAP on a Linux server. It is important to properly secure the LDAP server by implementing SSL/TLS encryption for data transmission, employing strong passwords and access controls, and regularly updating the server software to address any security vulnerabilities. Additionally, it is essential to regularly monitor and audit the LDAP server to detect and respond to any potential security breaches.
Is it possible to back up and restore LDAP data on a Linux server?
Yes, it is possible to back up and restore LDAP data on a Linux server. The most common method is to use the slapcat command to export the LDAP database to an LDIF file, which contains all the data and configuration settings. To restore the data, the slapadd command is used to import the LDIF file back into the LDAP server. It is important to regularly back up LDAP data to prevent data loss in case of server failure or accidental deletion of data.
What is LDAP?
LDAP stands for Lightweight Directory Access Protocol. It is a protocol used to access and manage directory information. It provides a directory service arranged in a hierarchical structure and is commonly used for authentication, centralized user account management, and storing other types of information.
Why would I need to install and configure LDAP on a Linux server?
You might need to install and configure LDAP on a Linux server if you want to set up centralized authentication and user management across multiple systems. LDAP allows you to have a single source of truth for user accounts and their credentials, making it easier to manage and control access to various services and resources within your network.




