In this fast-paced digital age, the security of our devices and personal information has become more crucial than ever before. As technology advances, so do the threats lurking in the shadows of the cyberspace. But fear not, for there is a formidable shield that stands between your computer and the ever-looming danger - the formidable guardian, known as the Firewall.
The Firewall is akin to a digital fortress, a gatekeeper that monitors and controls the flow of data between your computer and the vast expanse of the internet. It acts as a vigilant protector, shielding your system from malicious attacks, unauthorized access, and the perils that lie beyond the virtual walls. Its importance cannot be overstated.
However, like any powerful tool, the Firewall must be well-tuned and properly configured to maximize its effectiveness. It requires an understanding of its intricate workings, as well as the ability to navigate its complex settings and options. In this guide, we will delve into the realm of Firewall configuration, providing you with the knowledge and skills necessary to master its enigmatic nuances, and fortify your system against the ever-evolving threats of the digital realm.
Understanding Windows Firewall
In this section, we will delve into the fundamental concepts of the built-in security feature found within the Microsoft operating system. By gaining a comprehensive understanding of Windows Firewall, you will be equipped with the knowledge necessary to navigate its functionalities and effectively protect your system.
Familiarizing Yourself with Windows Firewall
Windows Firewall acts as a safeguard against unauthorized access to your computer, acting as a protective barrier that filters incoming and outgoing network traffic. This serves as a crucial defense mechanism, shielding your system from potential threats and vulnerabilities that may compromise its security.
The Role of Windows Firewall
One of the primary functions of Windows Firewall is to monitor network connections. Utilizing a set of predefined rules and configurations, it examines each network packet to determine whether it should be allowed or blocked. By utilizing this decision-making process, Windows Firewall helps ensure that only authorized and safe connections are permitted.
Ensuring Network Security
Windows Firewall offers a multi-layered approach to network security. Firstly, it provides the ability to create custom rules, allowing you to specify which applications and services are granted network access. This level of control ensures that potential entry points for unauthorized access are minimized.
Additionally, Windows Firewall employs various filtering techniques, such as stateful packet filtering, application filtering, and port filtering. These techniques actively monitor network traffic, examining the source, destination, and characteristics of each packet to determine its authenticity and legitimacy.
Monitoring and Managing Windows Firewall
Understanding how to monitor and manage Windows Firewall is essential in maintaining an optimized and secure system. By familiarizing yourself with the available tools and configurations, you can customize the firewall settings according to your specific needs and preferences.
Moreover, it is crucial to keep Windows Firewall up to date by regularly installing updates and patches provided by Microsoft. This ensures that the firewall remains equipped with the latest security enhancements and safeguards, effectively protecting your system against emerging threats.
By comprehending the key concepts and functionalities of Windows Firewall, you will be empowered to safeguard your computer against potential risks and maintain a secure network environment.
Introduction to Windows Firewall
Windows Firewall is a vital security feature that acts as a protective barrier between your computer and potential threats from external networks. It is a powerful tool that shields your system from unauthorized access, malicious software, and unwanted network traffic.
Windows Firewall monitors and controls the incoming and outgoing network traffic based on predefined rules and settings. It allows you to create a secure network environment by filtering and blocking suspicious or harmful connections. By implementing Windows Firewall, you can ensure the safety and integrity of your system and data.
This section aims to provide a comprehensive understanding of what Windows Firewall is and its significance in safeguarding your computer. Through the following paragraphs, we will explore the various features, configuration options, and benefits offered by Windows Firewall.
The Importance of Securing Your Network with a Robust Firewall

Safeguarding your network infrastructure has become increasingly crucial in today's digital age. Without a reliable and comprehensive firewall in place, your system and data are vulnerable to various cyber threats.
A firewall acts as a defensive barrier that protects your network from unauthorized access, malicious attacks, and the potential loss of sensitive information. It functions as a security guard, constantly monitoring and filtering the incoming and outgoing traffic to detect any suspicious activity.
By enforcing predefined security rules, a firewall ensures that only legitimate and authorized connections are established within your network, effectively blocking harmful traffic. It serves as a critical line of defense against malware, ransomware, viruses, and other cyber threats that can compromise your system's integrity and compromise your personal or business data.
Implementing a well-configured firewall is of paramount importance to maintain the confidentiality, integrity, and availability of your network. It not only provides an additional layer of protection, but also offers peace of mind, knowing that your data is guarded against unauthorized access and potential cyber attacks.
In conclusion, the significance of a robust firewall cannot be overstated. It plays an essential role in creating a secure network environment and safeguarding your valuable data. With the ever-evolving cybersecurity landscape, it is vital to invest time and effort into configuring and optimizing your firewall to ensure the highest level of protection for your network infrastructure.
Setting up Security for Your System: Managing Firewall Protection
To safeguard your system and protect it from potential threats, it is crucial to configure the built-in security feature responsible for managing network traffic - the firewall. By customizing firewall settings tailored to your specific requirements, you can control the flow of data and ensure that only trusted connections are allowed access.
In this section, we will explore the process of configuring the native firewall software on your operating system, enhancing your system's defense mechanism against unauthorized access, malware, and other potential risks. We will delve into the various aspects and options available for managing firewall protection, without relying on external software or expensive third-party solutions.
- Understanding Firewall Settings: An Overview
- Defining Firewall Zones: Creating Secure Network Boundaries
- Configuring Inbound Connections: Determining Trustworthy Sources
- Managing Outbound Connections: Safeguarding Sensitive Data
- Creating Custom Rules: Personalizing Firewall Behavior
- Enabling Notifications: Staying Informed About Security Events
- Advanced Firewall Techniques: Optimizing Performance and Security
By following the step-by-step instructions and best practices outlined in this guide, you will gain the necessary knowledge to configure your system's firewall effectively. With a well-configured firewall in place, you can give yourself peace of mind, knowing that your system is fortified against potential threats and unauthorized access attempts. Take control of your network security today with Windows Firewall!
Managing Access to Firewall Settings
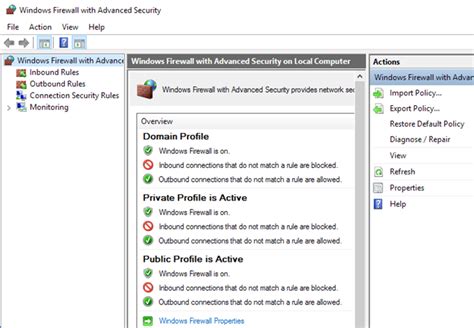
One of the essential aspects of maintaining security on your computer is controlling access to your firewall settings. By managing the configuration of your firewall, you can enhance the protection of your system and ensure that only authorized connections are allowed.
- Understanding Firewall Access Levels
- Limiting Access Permissions
- Configuring Firewall Rules
- Customizing Application Access
- Monitoring Firewall Activity
When it comes to accessing and managing your firewall settings, it is crucial to familiarize yourself with the different access levels available. By understanding the various permission levels and user accounts, you can establish granular control over who can modify the firewall settings on your computer.
To enhance security, it is recommended to limit access permissions to only trusted individuals who require administrative privileges. By implementing this practice, you can minimize the risk of unauthorized modifications or tampering with the firewall settings.
In order to effectively manage your firewall, configuring specific rules is necessary. These rules define which network traffic should be allowed or blocked based on criteria such as the source and destination IP addresses, ports, protocols, and applications. By setting up firewall rules, you can customize the level of protection according to your specific needs.
In addition to general firewall settings, it is essential to customize access for specific applications or programs. This allows you to monitor and control their network activity, ensuring that they can only establish connections deemed safe and necessary. By managing application access, you can prevent potentially malicious or unauthorized programs from compromising your system.
Monitoring firewall activity is also an important aspect of managing access to firewall settings. By regularly reviewing logs and event data, you can identify potential security threats, unusual connection attempts, and system vulnerabilities. This proactive approach enables you to take appropriate actions to protect your computer and network.
In conclusion, managing access to your firewall settings is crucial for maintaining the security of your computer. By understanding firewall access levels, limiting access permissions, configuring rules, customizing application access, and monitoring firewall activity, you can effectively control and protect your system against potential threats.
Setting up Windows Firewall for specific applications
Configuring the built-in security feature of your operating system to allow or block specific applications can enhance your system's protection against potential threats. In this section, we will explore the step-by-step process of customizing the Windows Firewall settings for individual applications, thus providing you with greater control over your system's network connections.
To begin customizing Windows Firewall for specific applications, you need to access the advanced settings of the firewall. Follow the below steps to get started:
| Step 1: | Open the Control Panel and navigate to the "Windows Defender Firewall" option. |
| Step 2: | Click on "Advanced settings" to access the advanced configuration options. |
| Step 3: | In the Windows Defender Firewall with Advanced Security window, select "Inbound Rules" from the left-hand pane. |
Once you have accessed the advanced settings, you can proceed with customizing the firewall rules for specific applications as per your requirements. By creating inbound and outbound rules, you can define how the firewall handles network traffic for individual applications.
To allow a specific application through the Windows Firewall:
| Step 1: | In the "Inbound Rules" section, click on "New Rule" from the right-hand pane. |
| Step 2: | Select "Program" as the rule type and click "Next". |
| Step 3: | Choose "This program path:" and browse to the location of the application executable file. |
| Step 4: | Select the desired action (e.g., "Allow the connection") and click "Next". |
| Step 5: | Select the network types for which you want to allow the connection. |
| Step 6: | Provide a name and description for the rule, and then click "Finish" to complete the process. |
On the other hand, if you wish to block a specific application through the Windows Firewall:
| Step 1: | In the "Inbound Rules" section, click on "New Rule" from the right-hand pane. |
| Step 2: | Select "Program" as the rule type and click "Next". |
| Step 3: | Choose "This program path:" and browse to the location of the application executable file. |
| Step 4: | Select the desired action (e.g., "Block the connection") and click "Next". |
| Step 5: | Select the network types for which you want to block the connection. |
| Step 6: | Provide a name and description for the rule, and then click "Finish" to complete the process. |
By following these steps, you can easily configure the Windows Firewall to allow or block specific applications, thereby enhancing the security and control of your system's network connections.
Allowing and blocking specific ports
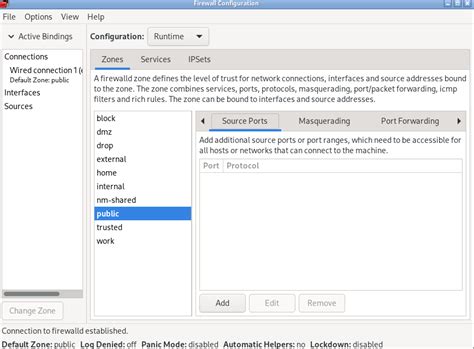
In this section, we will explore the process of managing network connectivity by allowing or blocking specific ports on your system. By controlling the access to ports, you can enhance your system's security and control the flow of information.
When you allow a specific port, you are granting permission for incoming or outgoing network traffic on that port. This can be useful for enabling access to specific applications or services that require communication through a specific port.
On the other hand, when you block a specific port, you are restricting network traffic to or from that port. This can help prevent unauthorized access, protect sensitive data, and mitigate potential security threats.
To allow or block specific ports, you can use the firewall settings on your system. These settings allow you to define rules based on port numbers, protocols, and IP addresses. By creating these rules, you can determine which ports are open or closed and control the flow of network traffic accordingly.
It is important to note that understanding the purpose and potential risks associated with specific ports is crucial before making any changes. By having a clear understanding of the services or applications utilizing those ports, you can make informed decisions and effectively configure your firewall settings.
- Allowing specific ports: To allow specific ports, you can create inbound or outbound rules in the firewall settings. These rules can be based on the port number, protocol (TCP or UDP), and IP address. By allowing specific ports, you enable the system to accept incoming or outgoing traffic on those ports.
- Blocking specific ports: To block specific ports, you can create inbound or outbound rules that deny traffic on those ports. This helps in preventing unauthorized access or restricting the communication of certain applications. By blocking specific ports, you enhance the overall security of your system.
- Considerations when allowing or blocking ports: Before allowing or blocking specific ports, it is important to consider the implications and potential impact on your system's functionality and security. Ensure that you only allow ports that are necessary for the proper functioning of your applications and services, and block ports that are not required or pose a potential security risk.
By effectively managing the access to specific ports, you can ensure the security and integrity of your system's network connectivity. Make informed decisions about which ports to allow or block based on the specific needs and risks of your system, and regularly review and update these settings to maintain optimal security.
Managing Network Traffic: Creating Inbound and Outbound Rules
In the realm of network security, an essential aspect is controlling the flow of incoming and outgoing data. To achieve this, it is vital to establish effective inbound and outbound rules. These rules govern the access permissions and restrictions for network traffic, ensuring the safety and integrity of your system.
The creation of inbound rules allows you to define specific criteria for allowing or denying incoming traffic to your device or network. By utilizing these rules, you can regulate the accessibility of various services, applications, or ports based on predetermined conditions. This proactive measure empowers you to block or permit incoming connections, safeguarding your resources and sensitive information from potential threats.
Similarly, outbound rules serve to manage the data leaving your system. These rules enable you to control what programs or services are allowed to transmit information from your device out onto the network. By setting outbound rules, you can restrict certain applications or services from establishing unauthorized connections, ensuring the security and privacy of your data.
One of the key steps in configuring inbound and outbound rules is defining the criteria upon which the rules will be based. This may include specifying specific IP addresses, port numbers, protocols, or even application names. By carefully selecting and setting these criteria, you can tailor the rules to align with your security requirements, granting access only to trusted sources or reputable services.
To effectively manage inbound and outbound rules, it is recommended to regularly review and update them based on your evolving network environment. By staying vigilant and adapting your rules to address emerging threats or changing needs, you can maintain robust network security and mitigate potential risks.
| Key Considerations: |
|
|---|
Customizing Notifications for Windows Firewall Setup
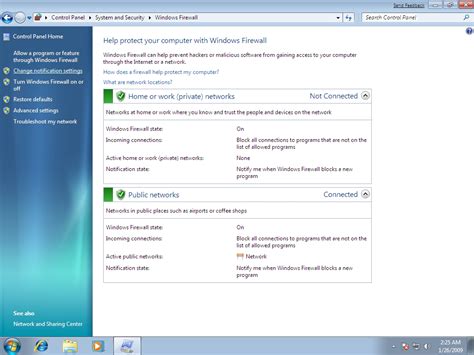
In this section, we will explore the various options available for customizing the notifications in your Windows Firewall setup. Notifications can provide important information about the status and activities of your firewall, allowing you to stay informed and take necessary actions as needed.
Understanding Firewall Notifications:
Firewall notifications play a crucial role in keeping you informed about the security status of your system. They can alert you about incoming or outgoing connections, blocked applications, potential threats, and other security-related events. By customizing these notifications, you can personalize the way your firewall communicates with you, ensuring that you receive relevant and timely information.
Configuring Notification Settings:
Windows Firewall offers a range of settings that allow you to control the type and frequency of notifications you receive. By accessing the Firewall settings, you can choose to enable or disable specific notifications, adjust their importance level, and select the preferred notification method (such as pop-up alerts or email notifications). These configuration options give you the flexibility to set up notifications that align with your security preferences and requirements.
Optimizing Firewall Notifications:
In addition to customizing the settings, it is important to optimize your firewall notifications to ensure they are actionable and effective. This can be achieved by tailoring notification rules, creating exceptions for trusted applications, and regularly reviewing notification logs for any unusual activity. By optimizing your notifications, you can streamline your workflow and enhance the overall security of your system.
Conclusion:
Windows Firewall notifications provide valuable insights into the security status of your system. By understanding and customizing these notifications, you can stay informed and take proactive measures to protect your system from potential threats. By exploring the various configuration options and optimizing your settings, you can enhance the effectiveness of your firewall notifications and ensure the safety of your digital environment.
Exploring Advanced Customization Settings
Once you have mastered the basic configuration options of your operating system's defense mechanism against unauthorized network access, it is time to delve into the realm of advanced customization settings for a truly tailored security experience. This section will introduce you to a range of powerful options that allow you to further refine the protection provided by the firewall, ensuring maximum security for your system and network.
1. Fine-tuning Rule Settings
Take your control to the next level by fine-tuning the rule settings of your firewall. Explore the various parameters that can be adjusted, granting you unprecedented control over incoming and outgoing connections. Customize the scope, source and destination IP addresses, protocols, and ports to allow or block traffic based on specific criteria. By utilizing these advanced rule settings, you can precisely define the network behavior that your system will permit, effectively thwarting any potential security threats.
2. Creating Advanced Rule Groups
Enhance the manageability of your firewall configuration by creating advanced rule groups. This powerful feature allows you to organize your security rules into logical groups, simplifying the administration of complex network environments. By grouping related rules together, you can easily enable or disable entire sets of rules with a single action, granting you fine-grained control over network access for different scenarios.
3. Implementing Custom Responses
Ensure that your system responds appropriately and decisively when a security event occurs by implementing custom responses. Learn how to configure the firewall to take specific actions when a potential threat is detected, such as logging the event, sending notifications, or even blocking the offending IP address. By tailoring the responses based on your specific needs, you can dictate how your system handles security incidents, minimizing the impact of any potential attacks.
4. Advanced Notification Settings
Stay informed about the activities of your firewall by exploring the advanced notification settings. Discover how to configure real-time alerts, email notifications, or integration with third-party security tools to receive timely updates about security events. By customizing the notification settings, you can ensure that you are promptly notified of any potential security breaches, enabling you to take swift action to protect your system and network.
5. Leveraging Firewall Logging
Unlock valuable insights into your network's security posture by leveraging the power of firewall logging. Explore the advanced logging capabilities of your firewall, allowing you to analyze and monitor network traffic in detail. Understand how to configure logging levels, filter logs based on specific criteria, and export logs for further analysis. By harnessing the wealth of information provided by firewall logs, you can gain a comprehensive understanding of your network's security landscape, aiding in the identification and mitigation of potential threats.
The Effective Use of the Advanced Protection Features in Windows Security
Enhancing the safeguarding measures on your computer does not have to be an overwhelming task by solely relying on standard configurations. Windows users can benefit from the inclusion of advanced security features available within the operating system. By leveraging the functionality of Windows Firewall with Advanced Security, individuals can fortify their systems against potential threats and unauthorized access.
Maximizing Security: Windows Firewall with Advanced Security offers an array of robust functionalities designed to significantly enhance the protection of your computer. These advanced features can be employed to create custom security rules, control network traffic and permit secure communication between trusted applications.
Creating Custom Security Rules: In order to effectively manage the flow of network traffic, Windows Firewall with Advanced Security enables users to define and implement custom rules. These rules can specify which connections are allowed or denied, based on various criteria such as IP addresses, ports, protocols, and specific programs. This level of granular control empowers users to establish tailored security policies suitable for their specific needs.
Controlling Network Traffic: Windows Firewall with Advanced Security provides users with the ability to closely regulate network traffic by filtering data packets passing through your system. By defining inbound and outbound rules, it becomes possible to monitor and manage connections based on various parameters such as source IP addresses, destination IP addresses, port numbers, and protocols. This facilitates a proactive approach in protecting your computer from potential threats originating from both internal and external sources.
Secure Communication: Leveraging the advanced security features of Windows Firewall provides a means to ensure secure communication between trusted applications. By manipulating the rule settings, users can allow specific applications to reliably communicate with each other, while blocking all other unauthorized attempts. This layer of protection greatly minimizes the risk of potential breaches, such as unauthorized data leaks or the infiltration of malicious software.
By taking advantage of the comprehensive functionalities offered by Windows Firewall with Advanced Security, users can establish a robust security framework tailored to their specific requirements. The ability to create custom security rules, control network traffic, and establish secure communication between trusted applications empowers individuals to enhance the protection of their valuable data, systems, and networks.




