In the intricate world of Linux administration, one crucial aspect that demands utmost attention is the management of network ports. These virtual endpoints play a pivotal role in establishing connections and facilitating data transfer between different applications and services. However, it is essential to have a comprehensive understanding of port management to enhance security, optimize performance, and maintain overall system stability.
In this article, we delve into the art of controlling network access by exploring various strategies to manipulate port states using the power of the command-line interface. Armed with the Bash shell, a versatile and powerful resource available on most Linux distributions, we will guide you through the process of fine-tuning port settings to suit your needs.
Discover the intricacies of managing port states effectively, leveraging a plethora of techniques encompassing firewall rules, network address translation, and packet filtering. Learn how to skillfully enforce firewall configurations, ensuring only authorized connections pass through, while skillfully dodging unwanted and potentially harmful network activity. By implementing these practices, you will fortify your Linux system against potential security vulnerabilities and guarantee its robust functionality.
Understanding Communication Ports in the Linux Environment

Introduction:
In the Linux operating system, there are various communication endpoints that enable the exchange of data between different processes. These endpoints, commonly known as ports, play a crucial role in establishing network connections and facilitating communication within the system. Understanding the fundamentals of ports in the Linux environment is essential for efficient networking and system administration.
Exploring the Concept of Ports:
Ports can be thought of as virtual points of entry and exit for data communication within a Linux system. Just like the physical ports of a computer, such as USB ports or audio jacks, communication ports enable the transfer of data between processes or devices. Each port is assigned a unique number, known as a port number, which helps identify the specific processes or services associated with that port.
For instance, a web server typically listens on port 80, while secure web traffic is commonly served on port 443. By establishing connections with these ports, clients can interact with the respective services and retrieve or transmit data.
Port Protocols and their Usage:
Port numbers are standardized, and certain port ranges are reserved for specific protocols or services. For example, ports below 1024, known as well-known ports or privileged ports, are commonly utilized by system services to provide essential functionalities. On the other hand, ports above 1024, referred to as dynamic or private ports, are typically allocated to user processes and applications.
Understanding the implications of different port numbers and their associated protocols helps system administrators and network administrators in effectively managing and securing their Linux systems.
Port Status and Security:
Monitoring and controlling the status of ports is crucial for maintaining the security and stability of a Linux system. Open ports can potentially be vulnerable to unauthorized access or exploitation. Therefore, system administrators should regularly assess and close any unnecessary or unused ports to minimize potential security risks.
With a better understanding of port functionality and management, administrators can enhance their ability to secure their Linux systems by closing any unused or unnecessary ports.
Conclusion:
In conclusion, ports serve as vital channels for communication within a Linux system. Understanding the purpose and usage of ports, as well as their associated protocols, is crucial for effective networking, system administration, and security. By gaining a comprehensive understanding of ports in the Linux environment, administrators can optimize their system's performance while ensuring it remains secure against potential threats.
Benefits of Securing Your Network by Blocking Access to Unwanted Connections
Ensuring the security of your network involves various measures, one of which includes closing ports that are not required for your system's operation. By blocking access to these ports, you can prevent unauthorized entities from establishing connections and gaining access to your sensitive data or potentially exploiting vulnerabilities in your system.
Enhancing network security
By closing unnecessary ports, you reduce the attack surface of your system, limiting the potential entry points for malicious activities. This helps safeguard your network from unauthorized access attempts and ensures the confidentiality and integrity of your data.
Minimizing the risk of vulnerabilities
Each open port represents a potential vulnerability that can be exploited by attackers. By carefully evaluating the ports that are truly necessary for your system's functionality and closing the rest, you significantly reduce the risk of exploitation and potential security breaches.
Preventing unauthorized access
Closing unwanted ports ensures that only authorized users or devices can connect to your system. By implementing strict access controls, you can prevent unauthorized individuals or bots from establishing unwanted connections and minimize the risk of unauthorized access, data theft, or malicious activities.
Improving system performance
Unnecessary open ports can consume system resources and impact performance. By closing unused ports, you can optimize your system's resource allocation and ensure that valuable resources are dedicated to the necessary processes, improving overall system performance.
In summary, closing ports that are not required for your system's operation is a crucial step in network security. By reducing the attack surface, minimizing vulnerabilities, preventing unauthorized access, and improving system performance, you can enhance the overall security and stability of your network.
Examining Active Connections to Your Linux System
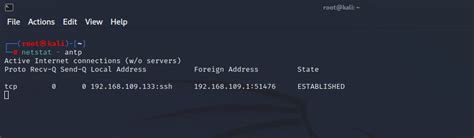
When managing the security of your Linux environment, it is crucial to regularly inspect the open ports and active connections. By understanding which ports are accessible and utilized, you can identify potential vulnerabilities and ensure the integrity of your system.
One way to gain insights into the open ports on your Linux system is to examine the active connections. These connections indicate the communication channels that are currently established between your system and other devices or networks. By checking the active connections, you can pinpoint any unexpected or suspicious activity that may compromise your system's security.
To check the open ports and their corresponding active connections, you can employ various command-line tools available in the Linux Bash shell. These tools offer a practical way to gather information about network connections and identify any potential risks.
netstat is a powerful command-line utility that provides a comprehensive overview of active connections and listening ports on your Linux system. By using the appropriate flags and options, you can customize the output to display the desired information.
Another useful tool is lsof (List Open Files), which allows you to view the active connections and ports by examining the open files associated with them. This tool provides detailed information about the processes and programs responsible for establishing these connections.
By running these commands and carefully analyzing the output, you can effectively monitor the open ports on your Linux system, identify any unauthorized connections, and take appropriate measures to address them. Regularly checking the open ports will help you maintain the security and integrity of your Linux environment.
Identifying the Port to Shut Down
When it comes to managing network connections and securing your Linux environment, it is crucial to have a clear understanding of the ports in use and the services associated with them. In this section, we will explore the process of identifying the specific port that needs to be disabled or closed, emphasizing the importance of comprehensive documentation and network analysis.
| Step | Description |
|---|---|
| 1 | Reviewing Network Services |
| 2 | Inspecting Listening Ports |
| 3 | Identifying Associated Processes |
| 4 | Checking Active Connections |
By following these steps, you will be able to pinpoint the specific port that requires closure in your Linux system. It is essential to perform a thorough analysis to ensure that the correct port is identified, avoiding disruptions to essential services and maintaining the integrity of your network configuration.
Securing your Linux Environment by Deactivating Network Connections
In this section, we will explore the importance of safeguarding your Linux environment by disabling network connections to ensure data integrity and prevent unauthorized access. By deactivating specific ports or connections, you can enhance the security of your system and protect it from potential cyber threats.
| Step | Description |
|---|---|
| 1 | Identifying the target port |
| 2 | Reviewing active network connections |
| 3 | Disabling the selected port |
| 4 | Verifying the closed port |
| 5 | Test the closed port to ensure no connections are allowed |
By following the steps outlined in this section, you will be able to effectively secure your Linux environment by closing off specific ports or connections that are not essential for your system's operation. This proactive measure will help mitigate potential security risks and protect your data from unauthorized access.
Mastering Firewall Rules for Securing Your Network
In this section, we will explore the powerful capabilities of firewall rules to enhance the security and protection of your network. By effectively utilizing firewall rules, you can safeguard your system by controlling network traffic and preventing unauthorized access to your ports and services.
Firewall rules offer a flexible and comprehensive approach to securing your network by allowing you to define specific criteria for filtering and managing incoming and outgoing data packets. By strategically configuring these rules, you can create a robust defense against potential threats and vulnerabilities.
Throughout this section, we will learn about the different types of firewall rules and how they can be effectively implemented to close or block access to specific ports. We will explore the concept of both inbound and outbound rules, understanding how they function and impact your system's security.
- Understanding the role of firewall rules in network security
- Implementing inbound firewall rules to close off unwanted access
- Creating outbound firewall rules to restrict unauthorized outgoing connections
- Utilizing advanced firewall rule configurations for fine-grained control
- Best practices for maintaining and updating firewall rules to adapt to evolving threats
By the end of this section, you will have a deep understanding of how to leverage firewall rules effectively to protect your network from potential security breaches and ensure a safe and secure computing environment.
Using iptables Command to Secure a Port

In order to enhance the security of a network, it's essential to close any open ports that are not in use. By using the iptables command in Linux, you can effectively block access to a specific port, preventing unauthorized connections and potential security threats.
iptables is a powerful and versatile firewall utility that allows you to set up rules for filtering network traffic. By utilizing iptables, you can create a firewall configuration that effectively protects your system from malicious activities, such as unauthorized access attempts or denial-of-service attacks.
By configuring iptables to close a port, you can ensure that only authorized connections are allowed to access your system. This can be particularly useful when dealing with services or applications that are not required to be accessible from the outside world.
To close a specific port using the iptables command, you need to define a rule that blocks incoming traffic to that particular port. This can be achieved by specifying the port number, protocol, and the action to be taken when traffic matches the rule.
For example:
iptables -A INPUT -p tcp --dport 8080 -j DROP
This command adds a rule to block incoming TCP traffic on port 8080 and drops any packets that match this rule. By using the appropriate port number and protocol, you can close any desired port using iptables.
It's important to note that changes made using iptables are not permanent and will be lost upon restarting the system. To make your firewall rules persistent, you can utilize additional tools and techniques, such as iptables-persistent or saving the configuration to a script.
In conclusion, by understanding how to use the iptables command to close a port, you can effectively enhance the security of your Linux system. With careful configuration, you can ensure that only authorized connections are allowed and protect your network from potential threats.
Testing the Blocked Connection
In this section, we will explore how to verify that a connection to a specific port has been successfully closed on a Linux system using the Bash shell. We will go through various tests and methods to ensure that the desired port is indeed inaccessible.
To validate the effectiveness of the port closure, we will employ different techniques, such as attempting a connection to the blocked port using the telnet command. By doing so, we can observe whether the connection is refused, thereby confirming the successful closure of the specified port.
We will also explore the utilization of the netstat command to check the current network connections and ensure that the port we closed does not appear in the list. This provides an additional means of verifying that the port closure has been implemented correctly.
Furthermore, we will discuss the use of the nmap utility, a powerful network scanning tool, to perform a port scan on the local system. By conducting this scan, we can determine whether the closed port remains hidden from external sources and is no longer accessible.
Lastly, we will explore the option of testing the closed port from a different machine on the same network. By attempting to establish a connection to the closed port from an external device, we can ensure that the port closure is effective not only locally but also from other networked machines.
Through these comprehensive tests and procedures, we can confidently determine the success of closing a specified port on a Linux system, ensuring enhanced security and control over network access.
Automating the Shutdown of a Communication Channel
In this section, we will explore the process of automating the termination of a communication channel in a Linux environment, without relying on manual intervention. By developing an efficient and reliable method for closing a specific route for data transmission, it becomes possible to streamline network management and enhance overall system security.
Analyze and Identify
In order to automate the closure of a port, it is essential to first understand the underlying processes and mechanisms involved in the communication channel. By thoroughly analyzing the network infrastructure and identifying the relevant ports in need of closure, we can establish a solid foundation for implementing automated methods.
Develop a Script
With a clear understanding of the target ports, it is now time to develop a script that will facilitate the automated closure process. By leveraging the power of the Bash shell, we can create a reliable and flexible script that meets our specific requirements. This script should include appropriate error handling and validation mechanisms to ensure the successful execution of the port closure procedure.
Testing and Refinement
Once the script has been developed, it is crucial to thoroughly test it in a controlled environment. This step allows us to identify any potential issues or shortcomings in the script, providing an opportunity for refinement and improvement. By conducting extensive testing, we can increase the reliability and efficiency of the automated port closure process.
Implementation and Integration
After ensuring the script's effectiveness through rigorous testing, it is time to implement it in the production environment. Seamless integration with existing systems and workflows is key to maximizing operational efficiency while minimizing disruptions. By following best practices and carefully deploying the script, we can automate the port closure process and significantly enhance overall system security.
Monitoring and Maintenance
Once the port closure process has been automated, it is essential to establish a comprehensive monitoring and maintenance system. Regularly monitoring the closed ports and updating the script based on evolving network requirements and security protocols will ensure continuous protection against potential vulnerabilities. By adopting a proactive approach to monitoring and maintenance, we can maintain a robust and secure system in the long term.
Best Practices for Effective Management of Communication Channels in a Linux Environment
When it comes to optimizing the performance and security of a Linux-based communication network, efficient management of communication channels is crucial. By implementing best practices, you can ensure smooth data flow, prevent unauthorized access, and maintain a stable and secure system.
- Regular Port Monitoring: Implement a systematic approach to regularly monitor the status of open ports on your Linux system. This enables you to identify potential vulnerabilities and take necessary actions to mitigate risks.
- Port Scanning and Auditing: Perform periodic port scanning and auditing to identify unauthorized or unnecessary open ports. This helps in minimizing potential entry points for malicious attacks and improves overall system security.
- Sensible Port Management: Utilize a well thought out port management strategy that involves opening only the necessary ports for legitimate services. Close any unused or deprecated ports to minimize the attack surface and reduce the risk of unauthorized access.
- Implementing Firewall Rules: Configure and maintain robust firewall rules to control incoming and outgoing network traffic. By defining specific rules based on IP address, port number, and protocol, you can filter and control the flow of data, enhancing the overall security of your Linux system.
- Systematic Patch Management: Keep your Linux system up-to-date by regularly applying security patches and updates. This ensures that any known vulnerabilities in the network stack or other communication components are addressed promptly, preventing potential exploits.
- Access Control: Implement strong access control measures, including authentication mechanisms such as secure user credentials, password policies, and two-factor authentication. Restricting access to open ports based on user roles and privileges enhances the security of your Linux system.
- Logging and Monitoring: Enable robust logging and monitoring mechanisms to track and analyze network traffic. Analyzing logs can assist in detecting anomalies, identifying potential security breaches, and proactively mitigating any potential risks.
- Educating System Users: Conduct regular training sessions to educate system users about the importance of port management and the potential risks associated with misuse or unauthorized access. Enhancing user awareness enhances the overall security posture of your Linux system.
- Documenting Port Configuration: Maintain up-to-date documentation of port configurations, including details such as the purpose of each open port, protocol used, and any associated restrictions. This documentation provides valuable information for troubleshooting, auditing, and maintaining the integrity of your Linux system.
By following these best practices for effective management of communication channels in a Linux environment, you can strengthen the security and optimize the performance of your system. Implementing these practices as an integral part of your network management strategy will help safeguard your system and ensure the smooth flow of data.
Linux BASH Shell Script Basics Part 2
Linux BASH Shell Script Basics Part 2 by Joe Collins 28,795 views 5 years ago 37 minutes
FAQ
What is a port in a Linux system?
In a Linux system, a port is a communication endpoint that allows different processes or applications to share data and access network services.
Why would I need to close a port in a Linux system?
You may need to close a port in a Linux system to enhance security and prevent unauthorized access to your system or network services running on that port.
How can I check if a port is open in a Linux system?
You can use the 'netstat' command to check if a port is open. For example, 'netstat -tuln' will display all listening TCP and UDP ports.
What is the Bash shell in Linux?
Bash is a popular command-line shell in Linux that provides an interface for users to interact with the operating system and execute commands.




