Securing network communications is a fundamental aspect of any modern software system. The use of SSL certificates plays a crucial role in establishing secure connections, ensuring confidentiality, and verifying the authenticity of parties involved. However, even with the widespread adoption of SSL/TLS protocols, issues can arise, giving rise to the need for troubleshooting and finding effective solutions.
One common challenge faced by developers and administrators working with Docker and Windows is the occurrence of x509 certificate errors. These errors may manifest themselves in various ways, such as the inability to establish secure connections, rejection of SSL certificates, or the display of error messages indicating invalid or mismatched names. Identifying the root cause and resolving these issues is crucial to maintain the integrity and security of Dockerized applications.
Addressing the issue of x509 certificate validity
When it comes to SSL certificates, the validity of the certificate is of utmost importance. It ensures that the certificate has not expired and is issued by a trusted certificate authority. However, sometimes Docker and Windows environments may encounter situations where certificates fail to be recognized as valid, resulting in errors that disrupt the smooth functioning of applications.
Next, we will explore the possible causes behind the x509 certificate validation errors in Docker environments and steps to rectify them.
Understanding the Challenge with x509 Authentication in Docker: Unraveling the Complexity
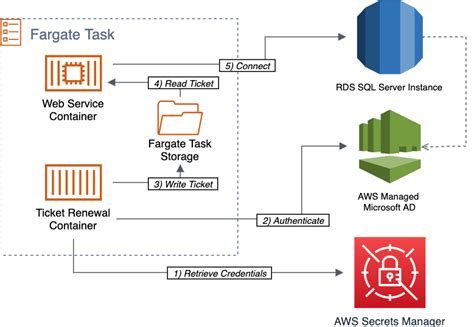
The Docker Windows x509 certificate issue is a stumbling block that many users encounter while dealing with containerization technology. This article aims to shed light on the intricacies surrounding this challenge and provide a comprehensive understanding of the problem at hand.
Exploring the realm of x509 certificate authentication in Docker reveals a labyrinth of potential roadblocks. This intricate system, designed to ensure secure communication and validate identities, relies on a complex web of cryptographic protocols and private-public key encryption. However, even a minor misconfiguration or mismatch can result in an "invalid certificate" error.
To gain a deeper understanding, it is crucial to delve into the inner workings of x509 certificates. These digital documents play a crucial role in establishing trust, verifying the authenticity of parties involved, and enabling secure communication. They contain various pieces of information, including key pairs, expiration dates, and subject identifiers.
Despite the significance of x509 certificates, ensuring their proper configuration and validation can be a daunting task. The "x509 certificate is invalid for any name" error often arises due to issues such as incorrect certificate paths, mismatched subject names, or expired certificates. This section will discuss the common causes of this error and guide readers towards potential solutions.
Furthermore, understanding the troubleshooting process for x509 certificate errors is essential for effectively addressing the issue. This involves examining system logs, verifying certificate paths and subject names, and ensuring that the certificate authority (CA) is trusted and properly configured within Docker.
In conclusion, comprehending the intricacies of x509 certificate authentication in Docker is crucial to overcoming the challenge of the "invalid certificate" error. By exploring the inner workings of these certificates and understanding the potential causes of the issue, readers can gain the knowledge needed to diagnose and resolve this frustrating roadblock effectively.
Understanding the Importance of Docker Windows x509 Certificates
In the world of modern technology, secure communication plays a critical role in ensuring the integrity and confidentiality of data. To establish a secure connection, applications and systems often rely on x509 certificates, which serve as digital credentials. Docker Windows x509 certificates hold an essential role in enabling secure communication between different components of a Docker environment.
These certificates act as a verification mechanism, ensuring that the parties involved in communication are authentic and trusted. By leveraging public key infrastructure (PKI), Docker Windows x509 certificates validate the identity of software components, individuals, or entities involved in data exchange.
The utilization of x509 certificates within the Docker ecosystem addresses the need for secure communication channels by applying encryption and authentication mechanisms. By leveraging cryptographic algorithms, Docker Windows x509 certificates ensure that data exchanged between Docker containers and other components remains confidential and protected against unauthorized access.
Furthermore, Docker Windows x509 certificates offer a level of trust, as they are issued by a trusted certification authority (CA). This authority validates the identity of the certificate owner, giving assurance to other components in the Docker environment that they can rely on the authenticity of the certificate holder.
| Key Points |
|---|
| Docker Windows x509 certificates ensure secure communication within the Docker environment. |
| They serve as digital credentials, verifying the authenticity and trustworthiness of parties involved in data exchange. |
| Docker Windows x509 certificates utilize encryption and authentication mechanisms to protect data confidentiality. |
| They are issued by trusted certification authorities, providing a basis of trust for other components in the Docker ecosystem. |
Causes of x509 Certificate Validation Failure for Different Entities
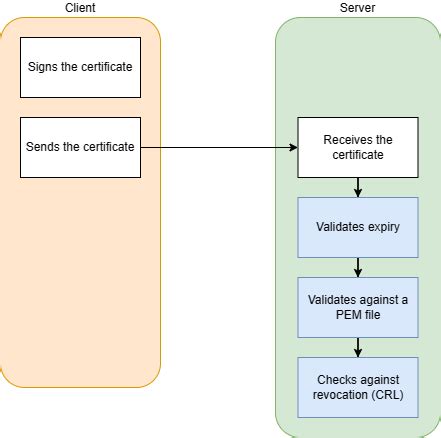
When examining the reasons behind the failure of x509 certificate validation for various entities, it becomes evident that multiple factors contribute to this issue. These causes encompass a wide range of circumstances that might result in the invalidation of the certificate. Below, we delve into some of these causes, outlining their potential impact and shedding light on the complexity of the situation.
| Cause | Description |
|---|---|
| Expired Certificate | One prevalent cause of x509 certificate failure is the expiration of the certificate. When a certificate is no longer valid, it cannot be trusted, resulting in the invalidation of the certificate. |
| Mismatched Common Name | In certain cases, the common name specified in the certificate might not match the entity requesting validation. This discrepancy leads to the rejection of the certificate as it fails to confirm a secure and authentic connection. |
| Revoked Certificate | A certificate may be revoked by its issuer due to compromised security or other reasons. When a certificate is revoked, it loses its trustworthiness, and any attempts to validate it will result in failure. |
| Improper Certificate Chain | Ensuring a proper certificate chain is crucial for successful validation. If any of the intermediate or root certificates in the chain are missing or improperly configured, the validation process will fail as the certificate cannot be properly verified. |
| Weak Encryption Algorithm | Using weak encryption algorithms in the certificate can also lead to validation failure. Organizations and individuals are encouraged to employ robust cryptographic standards to ensure the security and integrity of their certificates. |
It is important for both certificate issuers and certificate consumers to be aware of these potential causes of x509 certificate validation failure. By understanding these factors, they can take appropriate measures to prevent or troubleshoot certificate issues, ensuring the secure and reliable operation of their systems.
Identifying a Certificate Error: Ensuring the Integrity of Digital Identification
In the modern digital world, the use of certificates is essential for establishing secure connections and verifying the authenticity of entities. However, at times, errors may arise when dealing with x509 certificates, causing disruptions or security vulnerabilities. This section aims to shed light on the process of identifying an erroneous x509 certificate, enabling users to mitigate potential risks effectively.
When encountering a certificate error, it is crucial to be able to recognize the signs indicating its invalidity. One common indication is when the certificate fails to match the expected name or identity, leading to doubts about its legitimacy. In such cases, thorough evaluation and investigation become vital in detecting any inconsistencies or discrepancies.
- Pay attention to details: Scrutinize the certificate's information thoroughly, including the issuer, subject, and the domains it covers. Look for any misspellings or unfamiliar entities that may denote a forged or compromised certificate.
- Verify the certificate chain: Check the certificate's chain of trust, ensuring that it is complete and unbroken. Assess the intermediate and root certificates to ensure they have not expired or been tampered with.
- Consider trusted sources: Verify whether the certificate comes from a trusted and reputable source. Be cautious when dealing with self-signed certificates or those issued by unknown or unverified entities.
- Validate the certificate's digital signature: Confirm that the certificate's digital signature is valid and matches the expected cryptographic algorithm. An invalid or mismatched signature can be an indication of an unauthorized alteration.
By being vigilant and meticulous in the examination of x509 certificates, individuals and organizations can effectively identify and address any potential certificate errors. This heightened level of scrutiny promotes a secure digital environment, protecting sensitive information and ensuring the trustworthiness of online interactions.
Resolving the Issue with the Invalid Security Certificate in Docker for Windows
In the realm of Docker for Windows, there exists an occasional glitch that can disrupt the smooth operation of this virtualization tool. Specifically, an error message might appear indicating that the security certificate being used is invalid. However, fear not, as there are effective methods available to troubleshoot and resolve this issue, ensuring that your Docker experience remains uninterrupted.
One potential solution to rectify the invalid security certificate problem is to carefully examine the digital identification document in question. By verifying its authenticity and considering alternative sources, you can obtain a valid certificate that guarantees compatibility with the Windows operating system.
In addition, an alternative approach involves configuring the security settings of your Docker installation. By modifying the parameters and permissions related to the certificate management system, you can restore the proper functioning of Docker on your Windows system.
Furthermore, it may prove advantageous to update the Docker software to ensure that you have the most recent version. This can address any potential bugs or glitches that may have been present in previous iterations, including issues related to x509 certificates.
Ultimately, resolving the issue with the invalid security certificate in Docker for Windows requires a systematic examination of the digital identification document, adjusting relevant security settings, and potentially updating the Docker software. By following these steps and utilizing the appropriate troubleshooting techniques, you can ensure a seamless experience while utilizing Docker for Windows.
Updating Docker Version
In this section, we will explore the process of upgrading your Docker installation to the latest version available. By keeping your Docker version up to date, you can ensure access to the latest features, bug fixes, and security patches that enhance the overall performance and stability of the platform.
Firstly, it is important to regularly check for updates to ensure that you are aware of the latest Docker releases. Keeping your Docker installation updated is crucial for maintaining a secure and efficient container environment. To update Docker, you can follow these steps:
- Check for Updates: Start by checking your current Docker version and compare it to the latest version available on the official Docker website. They often release new versions that include various improvements and bug fixes.
- Backup Existing Environment: Before proceeding with the update, it is essential to create a backup of your existing Docker environment. This backup will allow you to restore your previous settings and configurations in case any issues arise during the update process.
- Download the Latest Version: Visit the official Docker website and download the latest version of Docker compatible with your operating system. Ensure that you select the appropriate version to meet your specific requirements.
- Stop Docker Processes: To prevent any conflicts or unexpected behavior, it is necessary to stop all Docker processes before initiating the update. By doing so, you ensure that the update process can make necessary changes without interference.
- Install the Latest Version: Once the Docker processes are stopped, proceed with the installation of the latest version you downloaded. Follow the installation instructions provided by Docker to complete the process seamlessly.
- Verify the Update: After the installation is complete, verify that the update was successful by checking the Docker version. Make sure it matches the latest version you downloaded and installed.
- Restore Previous Environment: If the update process caused any unintended issues or conflicts, you can revert back to your previous Docker environment by restoring the backup you created earlier. This ensures that your system remains stable and functional.
- Testing and Deployment: Finally, it is crucial to thoroughly test your updated Docker installation to ensure that all your containers and applications function as expected. Once you are confident in the stability and performance of your updated environment, you can proceed with your regular deployment processes.
By following these steps, you can successfully update your Docker installation to the latest version, ensuring access to new features and improvements while maintaining a secure and efficient container environment.
Resolving Issues with the Validity of Certificate Chains
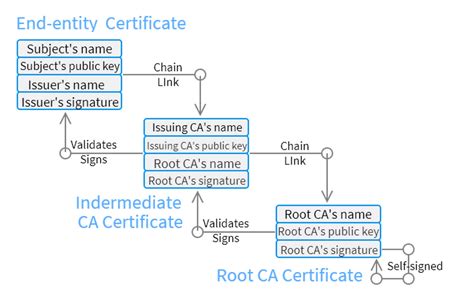
In the context of troubleshooting certificate-related errors, it is crucial to address the problems that can arise due to the incorrect validation of certificate chains. This section will explore the necessary steps to fix these types of errors without referencing specific platforms or certificate types.
A common challenge that many users encounter is navigating through the complexity of certificate chains and ensuring their proper validation. An invalid certificate chain can result in a range of error messages and constraints in the overall functionality of an application or system.
To address these issues, a systematic approach is required, starting with a thorough examination of the certificate chain. This involves verifying the validity and authenticity of all certificates within the chain, as well as investigating any potential issues or inconsistencies that may arise.
| Error Message | Probable Cause | Potential Solution |
|---|---|---|
| Unknown Authority | Missing or incorrect root certificate | Install or update the root certificate |
| Invalid Signature | Certificate tampering or corruption | Obtain a new certificate or restore from trusted backup |
| Expired Certificate | Validity period has passed | Renew the certificate and update the chain |
| Mismatched Hostname | Inconsistency between certificate and hostname | Ensure the correct hostname is specified and matches the certificate |
By identifying the specific error message and understanding its underlying cause, it becomes possible to take appropriate actions for fixing the certificate chain. These actions may involve obtaining updated certificates, installing missing root certificates, or adjusting hostname configurations to ensure compatibility.
Having an understanding of the common errors related to certificate chain validity provides a foundation for resolving such issues in a variety of contexts. By following the prescribed steps and maintaining a proactive approach to certificate management, users can ensure the smooth functioning of their systems and applications.
Working with Self-Signed Certificates in the Docker Windows Environment
Securing connections and ensuring the authenticity of server certificates is crucial for maintaining the integrity of data transfer in the Docker Windows environment. However, when working with self-signed certificates, there might be instances where the certificate validation process fails, leading to potential security vulnerabilities. This section will discuss effective strategies for working with self-signed certificates in Docker for Windows, offering solutions to address certificate validation errors and ensuring secure communication.
Understanding the Challenges: Self-signed certificates are not issued by a recognized certificate authority (CA), which means they are not automatically trusted by default. This lack of trust can result in the "Invalid Certificate" error message when attempting to establish secure connections in the Docker Windows environment. It is essential to familiarize oneself with the challenges that arise when working with self-signed certificates to effectively handle and rectify any validation issues.
Generating Self-Signed Certificates: One solution to overcome the validation error is to generate and use self-signed certificates properly. This process involves using tools such as OpenSSL to create a certificate signing request (CSR), generating the private key and public key, and then signing the certificate. By following the correct procedure for generating self-signed certificates, it is possible to bypass certificate validation errors and establish secure connections within the Docker Windows environment.
Adding Trust to Self-Signed Certificates: To ensure the smooth functioning of secure connections, it is crucial to add trust to self-signed certificates within the Docker Windows environment. This can be accomplished by adding the certificate to the trusted root certification authorities store, which instructs the system to trust the certificate. Carefully following the steps to add trust to self-signed certificates will enable secure communication without encountering any certificate validation errors.
Automating Certificate Management: Managing self-signed certificates in larger Docker Windows deployments can be a complex task. However, by implementing automated certificate management solutions, such as the use of a certificate management tool or creation of Dockerized certificate management containers, organizations can efficiently handle the lifecycle of self-signed certificates. Automating certificate management processes ensures a streamlined approach to handling certificates and minimizes potential errors and security risks.
Educating Users: Finally, it is important to educate users about self-signed certificates, their purpose, and potential security risks. By providing comprehensive documentation and training sessions on the proper usage and handling of self-signed certificates, organizations can empower users to make informed decisions and minimize the occurrence of certificate validation errors. Regularly updating users on best practices and security measures ensures a robust and secure Docker Windows environment.
In conclusion, working with self-signed certificates in the Docker Windows environment requires a thorough understanding of the challenges they pose and the implementation of effective solutions. By generating certificates correctly, adding trust, automating certificate management, and educating users, organizations can establish secure connections without encountering certificate validation errors and maintain the integrity of data transfer within their Docker Windows deployments.
Windows : Add SSL Certificate to Windows Docker Container
Windows : Add SSL Certificate to Windows Docker Container by Hey Delphi 73 views 1 year ago 1 minute, 11 seconds
FAQ
What is the cause of the "Docker Windows x509 Certificate is Invalid for Any Name" error?
The "Docker Windows x509 Certificate is Invalid for Any Name" error occurs when the TLS certificate used by Docker is not valid or does not match the expected name.
How can I fix the "Docker Windows x509 Certificate is Invalid for Any Name" error?
To fix this error, you can try restarting the Docker service, updating Docker to the latest version, or regenerating and reinstalling the TLS certificates.
Is there a way to disable TLS certificate verification in Docker and bypass the "Docker Windows x509 Certificate is Invalid for Any Name" error?
Disabling TLS certificate verification is not recommended as it compromises the security of the Docker environment. It is best to resolve the certificate issue by ensuring the correct certificates are being used.




