In the vast landscape of computer operating systems, there exists a remarkable and highly revered platform that embodies the philosophy of open-source software. Widely regarded for its stability, flexibility, and security, this exceptional system empowers system administrators to wield a variety of powerful commands to comprehensively manage the complex machinery that underpins it. Every adept system administrator must possess an innate understanding of the fundamental instructions necessary to navigate the intricate labyrinth of this revered system.
These ingenious instructions serve as a vital arsenal in the system administrator's toolkit, bestowing them with the ability to configure, monitor, and troubleshoot Linux systems with unparalleled finesse. These humble yet commanding directives offer a window into the inner workings of the system, enabling administrators to ascertain the health of their systems and mitigate any potential issues that may arise. Armed with these guidelines, system administrators are empowered to optimize performance, fortify security, and maintain the seamless operation of their Linux ecosystem.
Efficiency and efficacy reign supreme in the realm of system administration. In the pursuit of these coveted qualities, one must acquaint themselves with an assortment of potent instructions designed to streamline mundane tasks and expedite critical operations. From navigating directory structures to manipulating file permissions, this compendium of Linux commands equips system administrators with the necessary expertise to tackle any challenge that may arise. Furthermore, these imperious instructions possess the remarkable ability to automate repetitive tasks, liberating administrators from the shackles of monotonous labor and enabling them to devote valuable time and resources to more pressing matters.
As the adage goes, "knowledge is power". To grasp the true essence of Linux system administration is to delve into a realm where the picturesque confluence of innovation and pragmatism reigns supreme. As system administrators embark on their journey to unlock the secrets encrypted within the command line, they embark upon an odyssey that promises intellectual enlightenment and a profound understanding of the inner workings of their digital realm. Let these indispensable instructions serve as a beacon, illuminating the path towards mastery and enabling administrators to navigate the Linux landscape with confidence and finesse.
Understanding the Command Line Interface
Exploring the intricacies of the command line interface is essential for managing and operating various Linux systems effectively. In this section, we will delve into the fundamental concepts and functionalities of the command line interface, offering a comprehensive understanding of its significance in system administration.
1. Command Line Interface: An Introduction In this section, we will introduce the concept of the command line interface, discussing its purpose, advantages, and role in system administration. We will explore how the command line interface differs from graphical user interfaces (GUIs) and highlight its inherent power and flexibility. |
2. Navigating the Command Line Here, we will examine the basic commands used for navigating the command line interface, such as changing directories, listing file contents, and manipulating files and directories. Understanding these commands will enable system administrators to efficiently traverse the file system and locate relevant files and directories. |
3. Working with Permissions This section focuses on the crucial aspect of permissions in the command line interface. We will explore how to view and modify file and directory permissions, granting or restricting access to users and groups. A solid understanding of permissions is essential for ensuring security and data integrity within a Linux system. |
4. User and Group Management Managing users and groups is an integral part of system administration, and the command line interface provides powerful tools to accomplish these tasks. We will discuss how to create, modify, and delete users and groups, as well as examine various administrative tasks related to user and group management. |
5. Process Monitoring and Control Monitoring and controlling processes is essential for system performance and troubleshooting. In this section, we will explore commands used to view and manage processes, including starting, stopping, and restarting them. Understanding these commands will enable system administrators to effectively monitor and optimize system resources. |
By gaining a comprehensive understanding of the command line interface through the exploration of these fundamental concepts, system administrators will be equipped with the essential knowledge and skills needed to efficiently manage Linux systems and fulfill their administrative responsibilities.
Working with Files and Directories
Managing the structure and content of your computer's file system is an essential skill for system administrators. This section explores various operations and commands that can be used to efficiently work with files and directories in a Linux environment.
Creating and deleting files and directories is a foundational aspect of managing a Linux system. Understanding how to use commands such as mkdir, touch, and rm allows administrators to organize and control the file system.
Navigating the file system is another key skill for system administrators. By using commands like pwd, cd, and ls, one can efficiently move between directories, list their contents, and identify their current location within the file system.
Copying, moving, and renaming files and directories are common tasks in maintaining the file system. Familiarity with commands like cp, mv, and rename enables administrators to efficiently manage file and directory structures.
Searching for files and directories is an important skill when system administrators need to locate specific files or retrieve information from the file system. Commands such as find and grep allow for targeted searches based on various criteria.
Changing file permissions and ownership is crucial for maintaining the security and integrity of the system. Commands like chmod and chown allow system administrators to grant or restrict access to files and directories based on user and group privileges.
Archiving and compressing files and directories is necessary for backup purposes and efficient storage. Understanding commands like tar, gzip, and zip allows administrators to create compressed archives and extract files from them.
Viewing and editing file content is a daily task for system administrators. Commands like cat, less, and vi provide the ability to view, search, and modify the content of text files directly from the command line.
Performing file and directory comparisons is useful for verifying changes and identifying differences. Commands such as diff and cmp provide methods to compare files and directories and highlight discrepancies.
By mastering the various file and directory operations in a Linux environment, system administrators can effectively manage the file system, ensure data security, and maintain the overall stability and functionality of the system.
Networking Setup and Connectivity
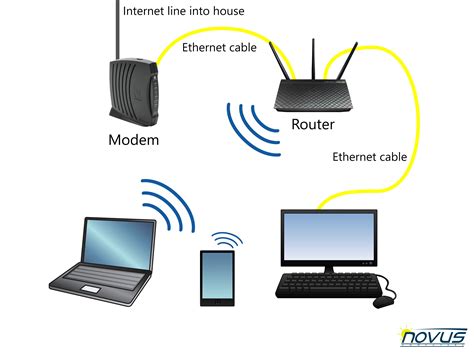
Configuring and establishing network connections is a crucial aspect of managing and maintaining computer systems. In this section, we will delve into the realm of network configuration and explore various techniques to ensure seamless connectivity.
Network configuration: Understanding how to configure network settings is essential for system administrators. This involves setting up IP addresses, subnet masks, default gateways, and DNS servers to establish a solid foundation for network connectivity. Additionally, we will explore the use of network profiles and how they can simplify the management of network settings across different environments.
Network troubleshooting: When it comes to troubleshooting network issues, having a comprehensive understanding of diagnostic tools and techniques is invaluable. We will discuss commands such as ping, traceroute, netstat, and nslookup, which can help identify network connectivity problems, analyze network traffic, and troubleshoot DNS resolution issues.
Network security: Ensuring the security of network connections is of utmost importance in any system administration role. We will explore techniques such as configuring firewalls, setting up VPNs, and implementing network access controls to safeguard sensitive data and protect against unauthorized access.
Remote connectivity: In today's digital landscape, the ability to remotely connect to systems is crucial for efficient system administration. We will delve into protocols such as SSH and VNC, which enable secure remote access, as well as explore techniques for remote file transfer and remote desktop management.
Monitoring and performance optimization: Monitoring network performance and optimizing network settings can greatly enhance system efficiency and user experience. We will discuss tools like ifconfig, iperf, and SNMP, and explore techniques for bandwidth monitoring, network traffic analysis, and optimizing network settings for improved performance.
Network virtualization: Virtualization technologies have revolutionized system administration, and network virtualization is no exception. We will delve into concepts such as virtual LANs (VLANs), virtual routers, and virtual private networks (VPNs), and explore the use of tools like VirtualBox and VMware to create and manage virtual network environments.
By diving into the realm of network configuration and connectivity, system administrators can gain the knowledge and skills required to establish, troubleshoot, secure, and optimize network connections, ensuring a reliable and efficient computing environment.
User and Group Management
In the realm of operating system administration, the efficient management of user accounts and group memberships plays a pivotal role. This section focuses on exploring the essential functionalities and techniques for effectively managing users and groups within a Linux environment.
User Management:
One of the fundamental tasks of system administrators is to create and maintain user accounts. User management involves the creation, modification, and deletion of user accounts, as well as the management of user privileges and access rights. By effectively managing user accounts, administrators can ensure proper security and control over system resources.
Creating user accounts involves defining unique usernames and assigning secure passwords. Administrators can also specify various account properties, such as the user's home directory and default shell. Additionally, user management allows administrators to set account restrictions, such as password expiration policies and account locking mechanisms.
Example command: useradd -m -s /bin/bash username
Modifying user accounts enables administrators to make necessary changes to user properties, such as modifying the user's home directory or shell. It also allows for the resetting of forgotten passwords or adjusting account restrictions. Being able to manage user accounts efficiently enhances the overall system security and adaptability.
Example command: usermod -d /new/home/directory username
Deleting user accounts involves permanently removing user profiles and associated files from the system. This process requires careful consideration to avoid accidentally deleting critical user data. Proper user account deletion ensures that system resources are efficiently utilized and maintains a clean and secure environment.
Example command: userdel -r username
Group Management:
In addition to user management, effective system administration involves managing user groups. Group management allows administrators to organize users into logical groups, simplifying access controls and permissions management.
Creating groups involves assigning a unique group name and assigning users to the group. By creating relevant groups, administrators can easily administer permissions and access controls for a defined set of users. Group management provides a flexible and efficient approach to handle access rights and enhance system security.
Example command: groupadd groupname
Modifying group settings allows administrators to make changes to group properties, such as adding or removing users from the group. This flexibility in group management ensures that access privileges are appropriately assigned and maintained.
Example command: gpasswd -a username groupname
Deleting groups involves the permanent removal of group definitions and associated permissions. Proper group management ensures the accuracy and efficiency of access controls within the system.
Example command: groupdel groupname
Overall, the effective management of users and groups is essential for maintaining system security, optimizing resource allocation, and simplifying access controls within a Linux environment. With a solid understanding and proficiency in user and group management, system administrators can ensure a stable and secure operating system for their organization.
Process Monitoring and Management
Efficiently managing and monitoring processes is a critical aspect of system administration. By keeping track of running processes and their resource usage, administrators can ensure the smooth operation of a system and identify any potential issues promptly. This section explores the techniques and commands used for process monitoring and management, allowing administrators to optimize system performance and troubleshoot problems effectively.
Ensuring Security and Managing Permissions
Security and permissions are vital components of maintaining a robust and secure Linux system. By establishing strong security practices and managing permissions effectively, system administrators can protect sensitive data, prevent unauthorized access, and maintain the integrity and confidentiality of the system.
- User Accounts: Creating and managing user accounts is essential for controlling access to the system. By assigning unique usernames and passwords, administrators can ensure that only authorized individuals can log in and perform specific actions.
- Password Policies: Implementing strict password policies helps to strengthen the security of the system. This includes setting requirements for password length, complexity, expiration, and prohibiting the reuse of old passwords.
- File Permissions: Setting appropriate file permissions is crucial for protecting sensitive files and directories. By assigning read, write, and execute permissions, administrators can control who can access, modify, or execute specific files, reducing the risk of unauthorized changes or data breaches.
- Access Control Lists (ACLs): ACLs provide a more granular level of control over file permissions by allowing administrators to define access permissions for specific users or groups. This enables fine-tuning access restrictions and managing permissions beyond traditional owner, group, and other categories.
- Firewalls: Configuring and managing firewalls is essential for safeguarding the system from network-based attacks. By defining firewall rules and controlling inbound and outbound traffic, administrators can restrict access to specific ports and services, preventing unauthorized access and potential security breaches.
- Encryption: Implementing encryption measures helps protect sensitive data both at rest and during transmission. By utilizing encryption technologies like SSH, SSL/TLS, or implementing file/system-level encryption, system administrators can ensure that sensitive information remains secure and unreadable to unauthorized individuals.
- System Updates: Regularly applying system updates, security patches, and software upgrades is vital for safeguarding the system against known vulnerabilities. By staying up to date with the latest security fixes, administrators can minimize the risk of Exploits and mitigate potential security threats.
Note: This article does not cover all security and permission aspects, but rather provides an overview of essential considerations for system administrators.
Managing System Backups and Restores
In this section, we will explore the fundamental aspects of safeguarding and restoring system data to ensure the continuity and resilience of your operations. We will discuss the importance of performing regular backups, establishing backup strategies, and implementing proper restoration procedures for critical system components.
One of the key responsibilities of system administration is to protect the integrity and availability of system data. A reliable backup and restore system is essential in mitigating the risks associated with data loss due to hardware failures, software issues, or human errors. By implementing effective backup and restore practices, system administrators can minimize downtime, facilitate disaster recovery, and ensure business continuity.
To organize and manage backups efficiently, it is crucial to devise a backup strategy tailored to your system's specific requirements. This strategy should encompass factors such as data prioritization, frequency of backups, storage media selection, and retention policies. By carefully considering these aspects, you can optimize backup operations while balancing storage costs and operational needs.
In addition to backups, having a well-defined restore process is equally important. System administrators must be proficient in implementing effective restoration procedures to quickly recover lost or damaged data. This involves understanding different restoration methods, such as full system restores, file-level recoveries, and database rollbacks. Furthermore, attention should be given to testing the restoration process periodically to ensure its reliability in real-world scenarios.
In many cases, system administrators employ backup software and utilities to automate and streamline the backup and restore tasks. These tools offer features such as compression, encryption, incremental backups, and scheduling capabilities. Familiarity with such software can greatly enhance the efficiency and reliability of your backup and restore operations.
To summarize, managing system backups and restores is vital for system stability and data protection. By adopting a well-planned backup strategy, implementing robust restoration procedures, and leveraging appropriate tools, system administrators can safeguard valuable data and minimize potential disruptions to critical systems.
| Key Points: |
|---|
| - Regular backups and restores are crucial for data protection and system continuity. |
| - Develop a backup strategy tailored to your system's needs, considering factors like data prioritization and storage cost. |
| - Implement effective restoration procedures and periodically test their reliability. |
| - Explore backup software and utilities to automate and enhance backup and restore operations. |
Linux Tutorial For Beginners - 1 | Linux Administration Tutorial | Linux Commands | Edureka
Linux Tutorial For Beginners - 1 | Linux Administration Tutorial | Linux Commands | Edureka by edureka! 2,167,125 views 6 years ago 2 hours, 34 minutes
FAQ
How can I list all the files and directories in a directory using Linux command?
To list all the files and directories in a directory, you can use the "ls" command with the directory path as the argument. For example, to list all the files and directories in the current directory, you can simply run the command "ls". To list the files and directories in a specific directory, you need to provide the path of that directory as the argument to the "ls" command. For example, to list the files and directories in the "/home/user/Documents" directory, you can run the command "ls /home/user/Documents".
How can I change the file permissions using Linux command?
To change the file permissions, you can use the "chmod" command followed by the desired permissions and the file name. The permissions can be represented using three digits or as a combination of letters (r, w, x) for read, write, and execute permissions respectively. For example, to give read, write, and execute permissions to the owner of the file, you can run the command "chmod 700 file.txt", where "file.txt" is the name of the file you want to change the permissions for.
What is the command to terminate a running process in Linux?
The command to terminate a running process in Linux is "kill". The "kill" command is followed by the process ID (PID) of the process you want to terminate. The PID can be obtained by running the "ps" command to list the running processes. For example, to terminate a process with PID 1234, you can run the command "kill 1234". You can also use the "-9" option with the "kill" command to forcefully terminate a process.
How can I create a new directory using Linux command?
To create a new directory, you can use the "mkdir" command followed by the name of the directory you want to create. For example, to create a directory named "new_directory", you can run the command "mkdir new_directory". By default, the new directory will be created in the current working directory. If you want to create the directory in a specific location, you can provide the path of that location as the argument to the "mkdir" command. For example, to create a directory named "new_directory" in the "/home/user" directory, you can run the command "mkdir /home/user/new_directory".
How do I list files and directories in Linux?
To list files and directories in Linux, you can use the "ls" command. By default, the "ls" command will list the files and directories in the current directory. However, you can also provide a specific directory path as an argument to the "ls" command to list the contents of that directory. Additionally, you can use various options with the "ls" command to customize the output, such as "-l" for a long listing format that includes file permissions, ownership, size, and modification time, "-a" to include hidden files and directories starting with a dot, "-h" to display file sizes in human-readable format, and many more.




