When it comes to the realm of computer networks, a language of its own emerges, with its own set of commands serving as the key to unlocking hidden treasures of information. The intricate web of ports, facilitating the flow of data between systems, holds a paramount position in this digital landscape. But is there an elusive command in the expansive world of Windows that can empower us to effortlessly navigate, observe, and manipulate these ports?
As we immerse ourselves in the vibrant tapestry of connectivity, the quest to comprehend port mechanisms becomes more pressing. Seeking out the essence of port management amidst countless lines of code and algorithms feels akin to embarking on a thrilling treasure hunt, chasing after elusive knowledge that promises to revolutionize our understanding of network architecture.
So, can we unravel the answer to this lingering question and unearth the hidden command that will allow us to perceive the intricate dance of data transmission through open ports in the Windows environment? Join us as we embark on this exhilarating exploration, armed with curiosity, determination, and a desire to demystify the inner workings of computer networks.
Understanding Open Ports and Their Significance in Windows
In the realm of computer networks, open ports play a crucial role in facilitating the exchange of information between devices. These ports can be thought of as digital doorways that allow data to flow in and out of a system. Each port is assigned a unique number, and different applications and services utilize specific ports to establish connections and transfer data.
Proper understanding of open ports is essential for maintaining a secure and efficient Windows environment. By comprehending how ports function, network administrators and users can effectively manage communication channels, ensure the smooth operation of applications, and protect against potential security threats.
A comprehensive understanding of open ports involves various key concepts. It involves recognizing the distinction between TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) ports, understanding the concept of port numbers, and being aware of the importance of port forwarding. Additionally, a solid understanding of common ports and their associated services enables effective troubleshooting and network optimization.
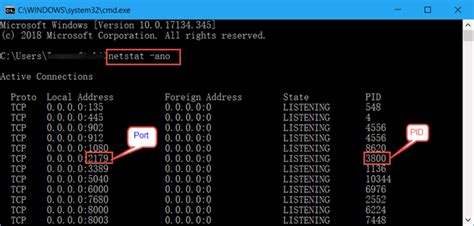
When it comes to managing open ports in Windows, several methods and tools are available. One such tool is the Command Prompt, which provides a command-line interface for executing commands and configuring network settings. Using commands like "netstat" or "nmap," network administrators can view a list of open ports, identify active connections, and monitor network activity.
Furthermore, Windows Firewall serves as a powerful tool for controlling incoming and outgoing traffic through open ports. Administrators can configure specific rules and settings to allow or block traffic on specific ports, thereby enhancing security and protecting sensitive data.
In conclusion, open ports play a vital role in facilitating communication within a Windows network. Understanding the significance of open ports and utilizing appropriate tools to manage and secure them is crucial for maintaining network integrity, optimizing performance, and safeguarding against potential threats.
| Key Concepts | Tools and Methods |
|---|---|
| TCP vs UDP ports | Command Prompt |
| Port numbers | Netstat |
| Port forwarding | Nmap |
| Common ports and services | Windows Firewall |
Understanding the Management of Active Network Connections
When it comes to the administration of active network connections on the Windows operating system, there are various approaches and techniques that can be employed. These methods allow users to effectively handle the state of open ports and manage the network traffic flowing through them.
One fundamental aspect of managing open ports on Windows is the utilization of built-in tools and utilities provided by the operating system. These tools offer a range of functionalities that enable users to monitor, control, and troubleshoot network connections.
Monitoring and Analyzing Network Traffic:
Windows provides a set of powerful command-line tools that assist in monitoring and analyzing network traffic. These utilities provide insightful data on active connections, listening ports, and established connections, allowing users to identify potential vulnerabilities or irregularities.
Additionally, powerful graphical user interface (GUI) applications are available to simplify the process and offer a more visual representation of network traffic. These applications often provide real-time monitoring capabilities, statistics, and advanced filtering options to better understand how open ports are utilized on the system.
Controlling and Managing Open Ports:
Windows offers a range of mechanisms to control and manage open ports. Users can easily configure firewall rules to allow or block specific ports, providing a layer of security for their network connections. This functionality can be accessed through the Windows Defender Firewall or third-party firewall applications.
Moreover, Windows provides programming interfaces and libraries that allow developers to create custom applications for managing open ports. These applications can be utilized to automate port configuration, establish secure connections, or implement advanced network functionalities.
Troubleshooting Network Connectivity:
When encountering issues with open ports or network connectivity, Windows offers a wide range of diagnostic tools for troubleshooting. These tools assist users in identifying and resolving common networking problems, such as incorrect port configurations, firewall issues, or software conflicts.
Furthermore, extensive documentation and online resources are available to facilitate the understanding and troubleshooting of open ports on Windows. These resources provide comprehensive guidance and best practices for managing network connections effectively.
In conclusion, Windows provides a diverse range of tools and techniques to manage open ports, monitor network traffic, control port access, and troubleshoot connectivity issues. By leveraging these resources, users can ensure the efficient and secure operation of their network connections.
The Importance of Port Numbers in Network Communication
In the realm of computer networking, the smooth and secure communication between devices is of paramount importance. To facilitate this communication, port numbers play a critical role in establishing connections and transferring data. Port numbers act as virtual addresses that allow devices to identify and deliver data to specific services or applications running on a computer.
When data is sent over a network, it needs to be directed to the correct application or service on the receiving device. Port numbers act as "doors" that applications use to receive data. By using different port numbers, multiple applications can run simultaneously on a single device, each receiving their respective data streams. This enables efficient and multitasking communication between devices connected on a network.
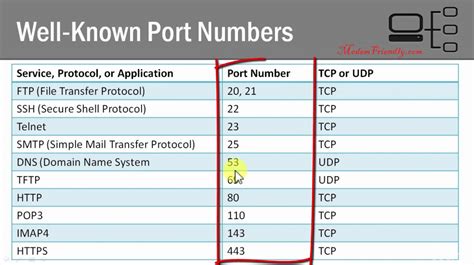
Port numbers are categorized into three ranges: well-known ports, registered ports, and dynamic (private) ports. Well-known ports are reserved for specific services, such as port number 80 for HTTP web traffic or 443 for secured HTTPS connections. Registered ports range from 1024 to 49151 and are assigned to specific applications or services by an authority organization. Dynamic or private ports, ranging from 49152 to 65535, can be used by any application dynamically as needed.
Understanding and managing port numbers is crucial for tasks such as network troubleshooting, security configuration, and setting up network services. By examining the open ports on a Windows machine, administrators can gain insights into the applications and services running, identify potential vulnerabilities, and implement appropriate access control measures.
- Port Scanning: Using specialized tools, administrators can scan for open ports on a Windows machine to detect any unauthorized or unexpected services running. This helps in identifying potential security risks and taking necessary actions to mitigate them.
- Firewall Configuration: Configuring a firewall involves opening or closing specific ports based on services' requirements and the desired level of security. By understanding port numbers, administrators can ensure that only necessary ports are open, reducing the attack surface and enhancing network security.
- Network Services Setup: When configuring network services such as web servers, email servers, or FTP servers, administrators need to specify the appropriate port numbers on which these services will listen for incoming connections. Knowing which port numbers to use ensures smooth and uninterrupted communication between the service and its clients.
In conclusion, port numbers are an essential aspect of network communication in Windows. They enable the accurate delivery of data to the appropriate applications or services, facilitate multitasking capabilities, and play a vital role in network security. Understanding and effectively managing port numbers is crucial for maintaining a secure and efficient network environment.
Tools to Monitor Active Ports on a Windows System
When it comes to managing network security and troubleshooting connectivity issues on a Windows system, having the ability to monitor active ports can be incredibly valuable. By keeping an eye on open ports, users can ensure that their network is secure and efficiently identify any potential vulnerabilities or suspicious activity.
Fortunately, there are several common tools available for checking open ports on a Windows machine. These tools provide users with essential information about the status of ports, such as whether they are open, closed, or filtered. Additionally, they can reveal which processes or applications are currently using specific ports.
| Tool | Description |
|---|---|
| Netstat | Netstat is a built-in command-line tool that provides a comprehensive overview of active network connections, listening ports, and associated processes. It allows users to identify established connections, view the state of ports, and handle various network-related tasks. |
| PortQry | PortQry is a versatile command-line utility developed by Microsoft. It enables users to query listening ports to verify their status and accessibility. PortQry supports different protocols and can test communication over both TCP and UDP ports. |
| Nmap | Nmap is a powerful open-source port scanning tool that provides a wide range of capabilities. It can scan a network for open ports, detect service versions, and identify potential security risks. While Nmap is primarily known for its advanced scanning features, it can also be used to monitor open ports on a Windows system. |
| TCPView | TCPView is a graphical utility developed by Microsoft's Sysinternals suite. It offers real-time monitoring of open TCP and UDP ports, providing users with a visual representation of active processes and their associated ports. TCPView allows for effortless identification of port usage and the ability to terminate unwanted connections. |
These tools serve as indispensable resources for individuals looking to manage and secure their Windows systems effectively. By utilizing them, users can gain valuable insight into the state of their open ports, aiding in network troubleshooting and ensuring a robust and secure network environment.
Managing Ports in Windows through Command Line Options
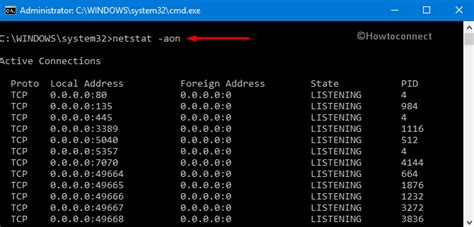
In the realm of Windows operating systems, there exists a robust set of command line options designed to facilitate the effective management of ports. These options serve as powerful tools to control and manipulate the flow of network traffic, enabling users to safeguard their systems and optimize network performance.
By leveraging the capabilities of these command line options, users can exercise granular control over different aspects of port management, ranging from monitoring and troubleshooting to configuring and closing ports. This level of control empowers individuals to address potential security vulnerabilities, identify network bottlenecks, and tailor network settings to suit their specific requirements.
One key capability offered by these command line options is the ability to explore the open ports on a Windows system. Using port enumeration, users can identify the active ports on their machine, gaining insights into the services or applications that are actively listening for incoming network connections. Armed with this information, users can make informed decisions regarding port access, prioritize resources, and ensure efficient network resource allocation.
Furthermore, these command line options allow users to perform critical tasks such as port scanning. By employing port scanning techniques, users can actively probe a target system to identify open ports, potentially uncovering hidden vulnerabilities or unauthorized services. This proactive approach to port management helps administrators fortify their systems against potential security breaches, reinforcing the overall network infrastructure.
Additionally, the command line options provide mechanisms to manage open ports effectively. For instance, users can employ commands to configure port blocking, restrict access to specific ports, or even disable unnecessary services running on certain ports. This fine-grained control ensures that only authorized traffic can pass through designated ports, minimizing the risk of unauthenticated network connections and potential cyber threats.
In conclusion, the command line options available in Windows provide a versatile toolkit for working with open ports. These options empower users to explore, scan, and manage open ports effectively, contributing to enhanced network security, optimized resource allocation, and a robust network infrastructure.
Using Netstat Command to View Open Ports on Your Windows System
Discovering the ports that are open and actively listening on your Windows system can be crucial for various reasons, such as troubleshooting network issues, monitoring network activity, or securing your system against potential vulnerabilities. Luckily, Windows provides a powerful command called Netstat that allows you to obtain detailed information about the open ports on your machine.
Netstat, a shorthand for Network Statistics, is a powerful command-line tool that comes built-in with Windows operating systems. It provides you with an overview of active network connections, routing tables, and open ports on your system. By utilizing Netstat, you can easily identify the processes, IP addresses, and ports associated with active network connections.
With the Netstat command, you can gather crucial information about open ports, such as the protocol (TCP or UDP) used by the port, the local and remote addresses, and the state of the connection (e.g., listening, established, or closed). This information can be invaluable for troubleshooting network-related issues, identifying potential security threats, or simply understanding the network activity on your Windows system.
By using the appropriate Netstat flags and filters, you can tailor the output to your specific needs. For example, you can use the "-a" flag to display all active connections and listening ports, the "-n" flag to prevent DNS resolution and display IP addresses instead of hostnames, or the "-b" flag to include the name of the executable involved in establishing the connection.
By becoming familiar with the Netstat command and its various options, you can better understand the network activity on your Windows system and effectively manage open ports. Being able to view and analyze open ports can help you identify potential security risks, ensure proper network functionality, and enhance your overall system performance.
How to Close Unwanted Ports on Your Windows System
Unwanted open ports on your Windows system can leave your computer vulnerable to potential security threats. By closing these ports, you can protect your system from unauthorized access and ensure a safer computing experience.
One of the ways to close unwanted open ports is by utilizing built-in networking tools available in Windows. These tools allow you to manage and control the ports that are currently open on your system.
| Step | Action |
|---|---|
| 1 | Identify the open ports |
| 2 | Access the Windows Firewall |
| 3 | Review inbound and outbound rules |
| 4 | Close the unwanted ports |
| 5 | Test the closed ports |
Start by identifying the open ports on your system that you wish to close. This can be done by using various network scanning tools or by checking the list of active connections on your computer. Once you have identified the unwanted open ports, proceed to access the Windows Firewall settings.
In the Windows Firewall settings, review both the inbound and outbound rules. These rules allow or block network traffic to and from your computer. Locate the rules that are associated with the unwanted open ports and modify them accordingly to block the traffic.
After modifying the firewall rules, test the closed ports to ensure they are no longer accessible from external sources. You can use port scanning tools or online port checking services to verify the closure of the ports. If the ports are successfully closed, your system will be better protected against potential security risks.
By following these steps, you can effectively close unwanted open ports on your Windows system and enhance the overall security of your computer.
Port Forwarding and Windows: A Comprehensive Guide
In this section, we will explore the concept of port forwarding and its application in Windows operating systems. Port forwarding is an essential technique that allows network traffic to bypass firewalls and reach specific devices or services on a private network. With the increasing need to access devices remotely or host online services, understanding port forwarding in the context of Windows is crucial.
Understanding the Significance of Port Forwarding
Port forwarding plays a critical role in enabling remote access to devices or services located behind a network's router or firewall. By configuring the router to forward incoming connections to the relevant device or service, users can establish remote connections and interact with devices such as cameras, network-attached storage (NAS) devices, or even host web servers.
Synonyms: Port Mapping, Port Redirection, Port Tunneling.
Port forwarding operates by redirecting incoming traffic from a specific port on the router to a designated port on a device within the network. By doing so, it allows external devices or services to communicate directly with the desired device, overcoming any network obstacles. This technique is particularly useful when dealing with network configurations that involve NAT (Network Address Translation) or when the network is protected by a firewall.
Implementing port forwarding in a Windows environment requires a basic understanding of networking concepts, as well as familiarity with the router's configuration interface. This comprehensive guide will provide step-by-step instructions, along with tips and best practices, to successfully set up port forwarding on a Windows computer.
Synonyms: Windows-based Port Forwarding Configuration, Port Forwarding Setup for Windows.
Additionally, we will explore common troubleshooting techniques for resolving issues related to port forwarding, such as port conflicts or misconfigurations. Understanding how to identify and resolve these problems will ensure the smooth operation of remote access to devices or services hosted behind your Windows-based network.
By the end of this guide, you will have a comprehensive understanding of port forwarding in a Windows environment, empowering you to set up and manage port forwarding configurations effectively, enhancing your network's accessibility and convenience.
Security Considerations for Accessing Network Ports on the Windows Operating System
When it comes to network communication, understanding the security implications of open ports in Windows is crucial. Open ports provide a gateway for data to pass through and enable the exchange of information between devices connected to a network. However, it is important to be aware of the potential risks associated with open ports and take necessary precautions to ensure the integrity and confidentiality of network communications.
- Port Scanning: Unauthorized individuals may attempt to identify open ports on a network through port scanning techniques. By identifying open ports, attackers gain insights into potential vulnerabilities to exploit and launch malicious activities.
- Port Forwarding: Port forwarding is a technique that enables access to a specific service or application running on a device behind a firewall. While helpful in some scenarios, port forwarding can expose network resources to potential threats if not properly configured and monitored.
- Firewall Configuration: A firewall acts as a barrier between internal and external networks, allowing or blocking incoming and outgoing traffic based on predetermined rules. Proper configuration of firewalls is crucial in preventing unauthorized access to open ports and securing network communications.
- Access Control: Implementing effective access control measures is essential to restrict access to open ports only to authorized devices or users. This can involve the use of strong passwords, user authentication, and network segmentation to limit exposure to potential threats.
- Regular Monitoring: Regularly monitoring open ports on the Windows operating system allows for the timely detection of any unauthorized access or suspicious activities. By promptly addressing such incidents, potential risks and vulnerabilities can be mitigated.
In summary, understanding the security considerations associated with open ports in the Windows operating system is crucial to maintaining a secure network environment. By implementing appropriate security measures, such as port scanning detection, firewall configuration, access control, and regular monitoring, organizations can reduce the risk of unauthorized access and protect the confidentiality and integrity of network communications.
Troubleshooting Tips for Handling Port Connections in the Windows Environment
When it comes to managing and resolving issues related to port connections in the Windows system, several strategies can be employed. These troubleshooting tips aim to provide practical guidance and assistance in identifying and addressing problems with port connections without relying on specific commands or software specifically designed for this purpose.
- 1. Analyze Network Configuration: It is crucial to thoroughly review and assess the network configuration settings to ensure proper functioning of port connections. This involves examining IP addresses, subnet masks, gateway settings, and DNS configurations. Any discrepancies or errors in these settings can potentially disrupt port connections.
- 2. Check Firewall Settings: Firewalls play a significant role in port connection management. Verify that the firewall software, whether it is built-in or a third-party application, is correctly configured to allow traffic through the required ports. Additionally, ensure that any rules or exceptions relevant to port connections are properly defined.
- 3. Identify Port Conflicts: Sometimes, conflicts may arise between multiple applications attempting to use the same port. Use suitable tools or utilities to identify any conflicting ports and resolve the conflicts by either reassigning the ports or terminating the applications responsible for the conflicts.
- 4. Examine Antivirus Settings: Antivirus programs often include built-in security features that can interfere with port connections. It is important to review the antivirus settings and disable any features that might impede the desired port connections. However, exercise caution and ensure the system's security remains intact.
- 5. Update Network Drivers: Outdated or faulty network drivers can cause issues with port connections. Regularly update the network drivers to the latest versions provided by the hardware manufacturer. This can alleviate potential compatibility problems and improve overall network stability.
- 6. Verify Hardware Components: Faulty network cables, routers, switches, or other network-related hardware can hinder port connections. Inspect and test the physical components to ensure they are functioning correctly. Consider replacing or repairing any defective hardware elements as needed.
By leveraging these troubleshooting tips, users can effectively identify and overcome common challenges associated with port connections in the Windows environment. Remember to exercise caution and seek expert assistance for complex issues to ensure a smooth and secure network operation.
FAQ
Is there a built-in command in Windows for working with open ports?
Yes, Windows provides a command-line tool called "netstat" that allows you to view the open ports on your computer.
How can I use the "netstat" command in Windows to check the open ports?
To use the "netstat" command, open the Command Prompt and type "netstat -a" to display all active connections and the listening ports on your computer.
Is there a way to filter the results of the "netstat" command to show only the open ports?
Yes, you can use the "-o" parameter with the "netstat" command to display the Process ID (PID) associated with each open port. Then, you can use the Task Manager to match the PID with the corresponding process and determine which ports are open.
Are there any alternative tools or commands in Windows for working with open ports?
Yes, apart from the "netstat" command, Windows also provides another command-line tool called "Portqry.exe" that can be used to check the status of TCP/IP ports on a remote computer. Additionally, there are several third-party software options available for port scanning and management.




