Imagine a world where database management is made secure and efficient with the help of cutting-edge technology. In this realm of innovation and reliability, businesses can safely store their valuable information without compromising on performance or security. This is the promise of leveraging the untapped potential of containerization in conjunction with the robustness of Windows authentication on Microsoft SQL Server.
In today's fast-paced digital landscape, organizations need to keep their sensitive data under lock and key. Traditional methods of securing databases are often a cumbersome and time-consuming process, prone to vulnerabilities. However, by embracing the power of containerization, businesses gain the ability to compartmentalize their applications and services, providing an extra layer of protection against unauthorized access and potential threats.
By combining the strength of Windows authentication with the versatility of Microsoft SQL Server, organizations can ensure a seamless and secure interaction between their database and applications. This powerful integration not only adds an extra level of security but also simplifies the process of authentication and authorization, allowing for easier management and monitoring of user access to the database.
The Advantages of Utilizing Docker with Windows Authentication

Incorporating containerization technology like Docker in conjunction with Windows Authentication can provide numerous benefits for organizations. This section explores the advantages that arise from merging these two concepts, highlighting the value they bring to various aspects of operations while ensuring optimal security and user authentication within the environment.
| Streamlined Deployment and Scalability |
| The combination of Docker and Windows Authentication simplifies the deployment process by allowing for rapid containerization and authentication setup. This streamlined approach enables organizations to swiftly scale their applications and services, ensuring efficient utilization of resources without compromising security. |
| Enhanced Portability and Compatibility |
| By utilizing Docker with Windows Authentication, compatibility issues between different operating systems and environments can be mitigated. This enables seamless movement of containers across various platforms, allowing organizations to leverage flexibility and portability without compromising authentication protocols. |
| Improved Security and Access Control |
| Integrating Docker and Windows Authentication provides robust security measures, ensuring only authorized users can access the containerized applications and services. Windows Authentication offers a reliable mechanism for verifying user identities, reducing the risk of unauthorized access and potential security breaches. |
| Efficient Development and Testing Processes |
| With Docker and Windows Authentication, developers can easily create isolated and reproducible environments, allowing for streamlined development and testing processes. By encapsulating the application and its dependencies, developers can confidently make changes within the container without impacting the host system, improving productivity and collaboration. |
| Cost and Resource Optimization |
| The utilization of Docker with Windows Authentication promotes efficient utilization of resources, reducing unnecessary system overhead and saving costs associated with deploying separate virtual machines for each application. Containerization facilitates resource sharing, allowing multiple applications to run concurrently on a single host while leveraging Windows Authentication for secure user access. |
In conclusion, the combination of Docker with Windows Authentication presents advantages in terms of deployment, scalability, portability, security, development processes, and resource optimization. By leveraging these technologies in tandem, organizations can optimize their operations, enhance security protocols, and ensure seamless user authentication within their containerized environments.
Strengthening Security in Database Management Systems
Security plays a critical role in safeguarding the confidential data stored in databases, particularly when it comes to sensitive information like user credentials, financial records, or personal details. In the constantly evolving digital landscape, where cyber threats are becoming more sophisticated, enhancing security measures in database management systems has become imperative.
Protecting sensitive data in a database involves implementing robust security features and employing best practices to prevent unauthorized access, data breaches, or data loss. This section explores various strategies that can be employed to enhance security in a database management system, ensuring data integrity and confidentiality.
- Implementing Strong Authentication Mechanisms: Utilizing advanced authentication methods, such as multi-factor authentication, biometric authentication, or federated authentication, can significantly strengthen the authentication process and reduce the vulnerability to password-based attacks.
- Enforcing Access Control Policies: Implementing granular access control policies allows administrators to control who can access specific data and what actions they can perform on it. Role-based access control (RBAC), access control lists (ACLs), or attribute-based access control (ABAC) are effective mechanisms to enforce access control policies.
- Regular Security Audits: Conducting frequent security audits helps identify any potential vulnerabilities or gaps in the security framework of the database management system. Regular audits not only ensure compliance with security standards but also provide an opportunity to proactively mitigate any identified risks.
- Encryption of Data: Encrypting sensitive data at rest and in transit provides an additional layer of protection against unauthorized access. Utilizing robust encryption algorithms and key management practices are essential to preserving data confidentiality.
- Monitoring and Intrusion Detection: Implementing robust monitoring tools and intrusion detection systems enables administrators to detect and respond to any suspicious activities or unauthorized access attempts promptly.
By implementing these security measures and adhering to best practices, database administrators can significantly enhance the security of their database management systems. Strong authentication mechanisms, precise access controls, regular security audits, encryption of data, and vigilant monitoring help establish a robust security framework, ensuring the confidentiality, integrity, and availability of valuable data.
Seamless Integration of Windows Authentication with Docker
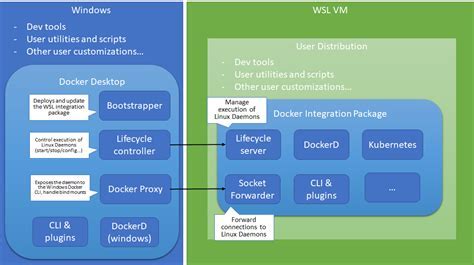
In this section, we will explore the smooth incorporation of Windows-based authentication into the Docker environment. By seamlessly integrating these two technologies, organizations can enhance security measures and streamline user access without compromising user experience.
To achieve this integration, we will delve into the intricacies of ensuring Windows identity authentication is seamlessly incorporated into Docker deployments. By understanding the underlying mechanisms and employing the appropriate tools, organizations can establish a secure environment for accessing containers and their underlying resources.
- Exploring the Need for Windows Authentication in Docker
- Understanding the Fundamentals of Windows Identity
- Utilizing Containerization to Enhance Windows Authentication
- Configuring Windows Authentication within a Docker Environment
- Implementing Best Practices for Secure User Access
- Ensuring Seamless Integration of Windows Authentication and Docker
By delving into the nuances and intricacies of seamlessly integrating Windows authentication with Docker, organizations can ensure a seamless experience for users while maintaining stringent security measures. Through effective configuration and utilization of the appropriate tools, organizations can create an environment that meets their security requirements while leveraging the power and flexibility of Docker containers.
A Step-by-Step Guide to Containerizing a Microsoft Database Server with User Verification
In this section, we will explore the detailed process of configuring a secure container environment for a popular database management system provided by Microsoft. By utilizing a unique set of steps and techniques, we will enable users to authenticate and verify their credentials, ensuring robust access control within the containerized ecosystem.
Introduction

In this section, we will explore the process of preparing your Windows environment for running containerized applications. We will dive into the essential steps required to configure your system and ensure a smooth Docker setup.
Prerequisites
- Windows operating system
- Familiarity with basic computer operations
- Understanding of virtualization concepts
- Administrative access to your Windows machine
Step 1: Enabling Virtualization
Before beginning the Docker setup process, it is crucial to ensure that virtualization technology is enabled on your Windows machine. Virtualization provides the necessary foundation for running containerized applications effectively. To enable virtualization, you can navigate to your system's BIOS settings and enable the corresponding option. It is recommended to refer to your computer manufacturer's documentation for specific instructions.
Step 2: Installing Docker Toolbox
To facilitate the usage of Docker on Windows, we will be installing Docker Toolbox. Docker Toolbox is a comprehensive suite of tools that helps simplify the installation and management of Docker containers on Windows environments. This suite includes essential components such as Docker Engine, Docker Compose, and Docker Machine.
To install Docker Toolbox:
- Visit the official Docker website.
- Download the appropriate version of Docker Toolbox for your Windows operating system.
- Run the installer and follow the on-screen instructions to complete the installation process.
Step 3: Configuring Docker Environment Variables
Once Docker Toolbox is successfully installed, we need to configure the Docker environment variables. These variables will allow Docker to communicate with your Windows system effectively.
To configure the Docker environment variables:
- Access the system's Environment Variables settings.
- Click on "New" to create a new system variable.
- Enter the variable name as "DOCKER_HOST" and the variable value as "tcp://localhost:2375".
- Click "OK" to save the changes.
Step 4: Verifying Docker Installation
A crucial step in ensuring a successful Docker setup is to verify that Docker is correctly installed and functioning on your Windows system. This involves running a simple command to check the Docker version and confirm its availability.
To verify Docker installation:
- Open a command prompt or PowerShell session.
- Type the command "docker version" and press enter.
- If Docker is installed correctly, the command will display the version information and other details.
Conclusion
In this section, we have covered the essential steps to set up Docker on your Windows machine. By enabling virtualization, installing Docker Toolbox, configuring Docker environment variables, and verifying the installation, you have established a solid foundation for running containerized applications successfully.
Configuring Support for Windows Authentication in Database Connections
Ensuring secure access to databases is a critical aspect of data management. One way to achieve this is by utilizing Windows Authentication, which enables users to connect to a database using their Windows credentials. Configuring SQL Server to support Windows Authentication involves a series of steps that enable seamless integration between user identities and the database.
Enabling Secure Access in a Docker Image
Creating a containerized environment with robust security measures is a critical aspect of modern application development. One essential component of ensuring secure access to a Docker image is enabling Windows authentication, which allows users to authenticate themselves using their Windows credentials.
Integrating Windows Authentication:
To build a Docker image with Windows Authentication enabled, it is crucial to configure the necessary components within the image.
Setting up Credential Providers:
Incorporating credential providers can facilitate the seamless integration of Windows Authentication. These providers handle the authentication process and ensure the secure validation of user credentials.
Configuring Authentication Protocols:
To enable Windows Authentication in a Docker image, it is essential to configure the authentication protocols that the image will support. Utilizing protocols like Kerberos and NTLM can enhance the security and reliability of the authentication process.
Establishing Trust Relationships:
To ensure a strong level of trust within the Docker image, establishing trust relationships with Active Directory domains and servers is crucial. This step allows the image to verify user credentials and validate their access rights.
Benefits of Windows Authentication:
Enabling Windows Authentication in a Docker image provides multiple benefits to both developers and end-users. This authentication mechanism offers enhanced security, as it leverages user credentials from trusted Active Directory domains.
Single Sign-On Experience:
By utilizing Windows Authentication, users can enjoy a seamless single sign-on experience. They can access multiple applications and services within the Docker environment without the need to repeatedly provide their credentials.
Scalability and Manageability:
Windows Authentication allows for the scalability and manageability of user accounts. It simplifies the administration process, making it easier to add, remove, or modify user access rights within the Docker image.
Compliance and Auditability:
With Windows Authentication, it becomes easier to meet compliance requirements and maintain audit logs. User authentication activities are logged, allowing for easy tracking and monitoring of access within the Docker environment.
Implementing a Docker image with Windows Authentication enabled ensures that users can securely access the contained applications and services while leveraging their trusted Windows credentials. By following the necessary configuration steps, developers can build a highly secure and user-friendly environment.
Implementing User Authentication in Docker Containers for Running SQL Servers
In this section, we will explore the steps required to effectively authenticate user access within Docker containers, particularly in the context of running SQL servers.
Establishing secured user authentication mechanisms is a crucial aspect of containerizing SQL servers within Docker. By implementing robust authentication protocols, you can ensure that only authorized users can access and interact with the SQL server instances running in your containers.
Below, we will outline the key considerations and techniques involved in setting up user authentication for Docker containers hosting SQL servers. By understanding these concepts, you will have the knowledge needed to effectively secure your containers and mitigate potential security risks.
- Implementing Role-Based Access Control (RBAC) mechanisms for containerized SQL server instances
- Utilizing Secure Sockets Layer (SSL) certificates to secure communication between clients and SQL servers
- Configuring strong password policies and encryption methods to safeguard user authentication
- Utilizing token-based authentication for enhanced security and user management
- Integrating Active Directory services for centralized user authentication within Docker containers
By following the best practices outlined in this section, you can ensure that your Docker containers running SQL servers are protected from unauthorized access and potential security breaches. Implementing user authentication mechanisms is essential for maintaining data integrity and safeguarding sensitive information.
Best Practices for Containerizing Microsoft's Relational Database Software with Active Directory-based Security Mechanism
In this section, we will explore the recommended approaches for deploying Microsoft's powerful relational database software within a containerized environment while leveraging Active Directory-based security mechanisms. By adhering to industry best practices, enterprises can ensure a secure and efficient deployment of their database infrastructure.
1. Utilize Identity and Access Management: Enhance the overall security of your containerized SQL Server instance by implementing rigorous user account management techniques. Leverage Active Directory to centrally manage authentication and access control, allowing for seamless integration within your existing enterprise security framework.
2. Implement Privilege Separation: Reduce the potential for unauthorized access to sensitive data by implementing a strict separation of duties. Assign roles and permissions based on the principle of least privilege, ensuring that each user or service account has the minimum necessary access privileges required for their specific tasks.
3. Enable Transparent Data Encryption: Safeguard the confidentiality of your data by utilizing transparent data encryption (TDE) within your containerized SQL Server environment. By encrypting the data at rest, you can mitigate the risks associated with unauthorized access to physical storage media.
4. Implement Network Segmentation: Segregate your containerized SQL Server environment from other components of your infrastructure by implementing network segmentation techniques. Utilize firewalls and virtual private networks to restrict access to the database instance and ensure that communication occurs only between authorized entities.
5. Regularly Patch and Update: Stay on top of security vulnerabilities by regularly applying patches and updates to your containerized SQL Server instances. Implement a robust patch management process to ensure that your database infrastructure is protected against known vulnerabilities.
6. Monitor and Audit: Maintain a high level of security and accountability by implementing comprehensive monitoring and auditing mechanisms. Regularly review logs and identify any suspicious activities or anomalies. This will allow for timely detection and mitigation of potential security breaches.
By following these best practices, enterprises can enhance the security and performance of their containerized SQL Server instances, ensuring a robust and scalable database infrastructure within an Active Directory-based authentication framework.
Operating System Considerations for the Hosting Environment
In order to successfully implement Docker containers with Windows Authentication on a SQL Server, it is essential to carefully consider the aspects of the host operating system. The host operating system plays a critical role in providing a secure and stable environment for the containers to run efficiently.
Security considerations:
The host operating system must have proper security measures in place to protect the Docker containers and the data they contain. This includes employing robust firewall configurations, implementing access controls for user authentication, and using encryption technologies to safeguard sensitive information.
Stability and performance:
The host operating system should be optimized for stability and performance to ensure smooth operation of the Docker containers. This involves regularly updating the operating system to the latest patches and updates, monitoring system performance to identify and resolve performance bottlenecks, and allocating appropriate system resources to the containers for optimal performance.
Compatibility with containerization:
To ensure seamless integration with Docker containers, the host operating system should be compatible with containerization technologies. This includes supporting containerization frameworks, such as Docker, and providing support for container networking and storage mechanisms.
Resource management:
The host operating system should have effective resource management capabilities to efficiently allocate system resources to the Docker containers. This involves monitoring resource utilization, such as CPU and memory usage, and implementing resource allocation policies to prevent resource contention and ensure fair sharing of resources among the containers.
Scalability:
The host operating system should be capable of scaling the Docker containers as the workload increases. This includes implementing load balancing mechanisms to distribute the workload across multiple containers, deploying container orchestration tools for automated container management, and adapting the host environment to handle increased demands for resources.
Overall, careful consideration of the host operating system is crucial for successful implementation of Docker containers with Windows Authentication on a SQL Server. By ensuring the host operating system meets the necessary security, stability, compatibility, resource management, and scalability requirements, organizations can create a robust and efficient hosting environment for their Docker containers.
Securing Communication Channels

Ensuring that communication channels are secure is crucial for protecting sensitive data and preventing unauthorized access. In the context of Docker with Windows Authentication on SQL Server, securing communication channels involves implementing robust measures to safeguard the transmission of data between different components.
Encryption: One of the key ways to secure communication channels is through encryption. By encrypting data during transmission, it becomes unintelligible to unauthorized parties, thereby reducing the risk of interception or tampering. Implementing strong encryption protocols helps maintain data integrity and confidentiality.
Authentication and Authorization: Proper authentication and authorization mechanisms play a vital role in securing communication channels. Authenticating the identity of the communicating parties ensures that only authorized individuals or systems can access sensitive information. Authorization mechanisms determine what actions and data each authenticated entity can access, helping to prevent unauthorized access or potential data breaches.
Secure Protocols: Utilizing secure protocols is essential for securing communication channels. Implementing protocols like Transport Layer Security (TLS) or Secure Sockets Layer (SSL) adds an additional layer of protection by encrypting data and providing secure communication channels. These protocols ensure that data is transmitted securely, reducing the risk of interception or compromise.
Regular Updates and Patching: Keeping all components of the communication system up to date with the latest security patches is crucial to maintain the overall security posture. Regular updates and patching help address vulnerabilities and weaknesses, ensuring that communication channels remain protected against emerging threats and attack vectors.
Monitoring and Logging: Implementing robust monitoring and logging mechanisms enables administrators to identify and respond to any potential security incidents or breaches promptly. Monitoring communication channels helps detect suspicious activities or unauthorized access attempts, allowing for timely intervention and mitigation.
Awareness and Training: Ensuring that personnel involved in the communication system are aware of security best practices and receive regular training is paramount. Adequate training helps individuals understand the importance of secure communication and enables them to identify and report any potential security vulnerabilities or incidents.
By implementing these measures and prioritizing the security of communication channels, organizations can enhance the overall protection of their Docker environment with Windows Authentication on SQL Server, reducing the risk of data breaches and ensuring the integrity and confidentiality of sensitive information.
SQL Server Quickie #44 - SQL Server on Docker
SQL Server Quickie #44 - SQL Server on Docker by SQLpassion 1,279 views 1 year ago 15 minutes
Run SQL Server in a Docker Container - SQL Server Anywhere!
Run SQL Server in a Docker Container - SQL Server Anywhere! by Roberts Dev Talk 7,271 views 3 years ago 5 minutes, 51 seconds
FAQ
Can I use Windows Authentication with Docker on SQL Server?
Yes, you can use Windows Authentication with Docker on SQL Server. This allows you to leverage the existing Windows user accounts for authentication and access control.
How can I set up Windows Authentication with Docker on SQL Server?
To set up Windows Authentication with Docker on SQL Server, you first need to create a custom Docker image that includes the necessary configuration to enable Windows Authentication. This involves updating the Dockerfile and running some specific commands to install and configure the required components.
What are the benefits of using Windows Authentication with Docker on SQL Server?
Using Windows Authentication with Docker on SQL Server provides several benefits. It allows you to seamlessly integrate with your existing Active Directory infrastructure, simplifies user management and access control, and enhances security by leveraging strong Windows authentication mechanisms.
Can I use Windows Authentication with Docker on SQL Server Express edition?
No, Windows Authentication is not supported on SQL Server Express edition. It is only available in the Standard, Enterprise, and Developer editions of SQL Server. If you need to use Windows Authentication, you will need to upgrade to one of these editions.
Are there any limitations when using Windows Authentication with Docker on SQL Server?
Yes, there are a few limitations to be aware of. First, you need to make sure that your Docker host is joined to an Active Directory domain. Additionally, you may encounter some challenges when using Windows Authentication in multi-container scenarios or with certain networking configurations. It's important to carefully plan and test your setup to ensure smooth operation.
Can I use Windows Authentication with Docker on SQL Server?
Yes, you can use Windows Authentication with Docker on SQL Server. Docker provides support for Windows containers, allowing you to run SQL Server with Windows Authentication in a containerized environment.
How can I configure Windows Authentication for SQL Server in a Docker container?
To configure Windows Authentication for SQL Server in a Docker container, you need to create a custom Docker image that includes the necessary configurations. This involves setting up the container to join an Active Directory domain, configuring the SQL Server instance to use Windows Authentication mode, and mapping the necessary ports for communication. Once the image is built, you can run the container and connect to SQL Server using Windows Authentication.




