Within the expansive realm of information technology, there lies an uncharted territory where the boundaries between different operating systems blur and new possibilities emerge. In this digital landscape, the concept of containerization has revolutionized the way we deploy and manage applications by encapsulating them into lightweight, isolated environments. However, the intricacies of networking within these containers, particularly on Windows systems, remain an enigma awaiting discovery.
As we traverse this unexplored terrain, we embark on a quest to understand the underlying mechanisms that enable Windows containers to seamlessly communicate, collaborate, and exchange information. Like strands in a complex web, the interconnectedness of these systems gives rise to a network that parallels the functionality of a traditional host environment. By delving into the depths of this containerized network, we unravel the threads that bind these isolated entities together, propelling them towards unprecedented levels of efficiency and productivity.
Within the realm of containerized networking, the term "host equivalent analog" characterizes the bridging of disparate systems into a cohesive whole, transcending the limitations that once confined them. In this abstract amalgamation of Windows containers, we witness the rise of synergistic connections that emulate the familiar landscape of a host environment, albeit with a unique twist. By examining the triumphs and challenges inherent in this harmonious convergence, we unravel the untapped potential that awaits those who dare to embrace this innovative approach to network orchestration.
Understanding the Fundamentals of Windows Network in Docker
In this section, we will explore the core principles and concepts behind the networking functionality of Windows within the Docker environment.
Networking plays a crucial role in facilitating communication between various components within a Dockerized Windows environment. Understanding how networking works in this context is essential for effectively managing and troubleshooting network-related issues.
One key aspect to grasp is the notion of network namespaces, which allows for the isolation and segmentation of network resources within a containerized Windows environment. This enables each container to have its own network stack, including distinct interfaces, IP addresses, and routing tables.
| Concept | Description |
|---|---|
| Container Network Types | Explore the different types of container networks available within Docker for Windows, including bridge, host, and overlay networks. |
| Network Driver | Learn about the role of network drivers in Docker, which enable the creation and management of different types of container networks. |
| Port Mapping | Understand how port mapping allows for the mapping of a container's internal ports to external host ports, enabling access to containerized applications from outside the Docker environment. |
| Network Troubleshooting | Discover common network-related issues that may arise in a Dockerized Windows environment and learn troubleshooting techniques to resolve them. |
By gaining a solid understanding of the basics of Windows network within Docker, you will be better equipped to effectively manage network resources, troubleshoot issues, and optimize the overall performance of your containerized Windows applications.
Unveiling the Advantages of Utilizing Docker Windows Network
Discover the multitude of benefits that arise from harnessing the power of Docker Windows Network. By leveraging this innovative technology, users can experience unparalleled flexibility, seamless integration, and enhanced efficiency in their network infrastructure.
- Improved Scalability: Docker Windows Network offers the ability to effortlessly scale applications, allowing them to adapt to the ever-changing demands of a dynamic environment.
- Enhanced Security: With Docker Windows Network, users can achieve heightened security measures through containerization, ensuring that their applications and data remain isolated and protected.
- Streamlined Collaboration: The utilization of Docker Windows Network fosters seamless collaboration between development and operations teams, facilitating efficient workflows and enabling faster time to market.
- Efficient Resource Utilization: By utilizing Docker Windows Network, organizations can maximize resource utilization, optimizing the performance of their network infrastructure and reducing operational costs.
- Easy Deployment and Management: Docker Windows Network simplifies the deployment and management of applications, providing users with the ability to effortlessly spin up containers and efficiently manage their network resources.
Embrace the advantages and revolutionize your network infrastructure with Docker Windows Network. Streamline processes, enhance security, and scale your applications effortlessly, all while experiencing the utmost flexibility and efficiency.
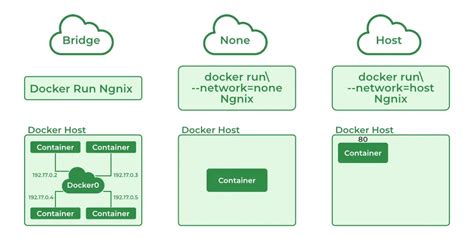
Docker Networking Modes for Windows Containers
In this section, we will explore the various networking modes available for Windows containers in the context of Docker. These modes provide different ways to establish communication between containers, allowing for flexibility and scalability in containerized environments.
- Bridge Mode: This mode creates isolated networks for containers, enabling communication between containers on the same host or across multiple hosts within a cluster.
- Overlay Mode: Overlay networks allow containers to communicate seamlessly across different hosts, even if they are running on different physical or virtual machines.
- Host Mode: With host mode, containers share the network stack of the host system, allowing them to directly access network resources without any isolation.
- MACVLAN Mode: MACVLAN networks provide a way to assign a unique MAC address to containers, allowing them to be directly connected to the physical network, and enabling direct communication with external devices.
- NAT Mode: In NAT mode, containers share the IP address of the host system and are able to access the network through port forwarding.
- None Mode: None mode disables networking for containers, making them completely isolated from any network communication.
By understanding the different networking modes available for Windows containers, you can choose the most appropriate mode based on your specific requirements. Whether you need isolation, scalability, direct access to network resources, or complete network isolation, Docker provides a range of networking options to suit your needs.
Creating a Custom Network for Windows Containers
In this section, we will explore the process of building a unique network interface for Windows containers, designed specifically to meet your organization's requirements. By creating a custom network, you can customize and control the connectivity between containers, allowing them to communicate seamlessly while maintaining isolation.
Designing a Tailored Network
In order to optimize the container networking experience in a Windows environment, it is essential to design a tailor-made network infrastructure that aligns with your specific needs. By creating a custom network, you can tailor parameters such as IP address ranges, subnets, and DNS settings to ensure secure and efficient communication between containers.
Building Seamless Communication
A custom network allows you to establish seamless communication channels between containers, enabling them to exchange information and collaborate efficiently. By defining network bridges, you can connect multiple containers within the same network and grant them access to shared resources, fostering improved collaboration and data transfer.
Enhancing Security and Isolation
Creating a custom network for Windows containers introduces enhanced security and isolation. By isolating containers within their unique network, you can control their access to external resources and restrict communication with other containers. This level of isolation adds an extra layer of protection and minimizes the risk of potential vulnerabilities.
Optimizing Performance
A custom network allows you to optimize the performance of your Windows containers by fine-tuning network settings. By carefully configuring network parameters such as bandwidth allocation and quality of service, you can ensure that your containers operate at peak efficiency and that communication between them is smooth and uninterrupted.
In conclusion, creating a custom network for your Windows containers enables you to tailor and optimize the connectivity between them, enhancing security, isolation, and performance. By gaining control over the networking infrastructure, you can design a network that seamlessly integrates with your organization's requirements and enables efficient collaboration between containers.
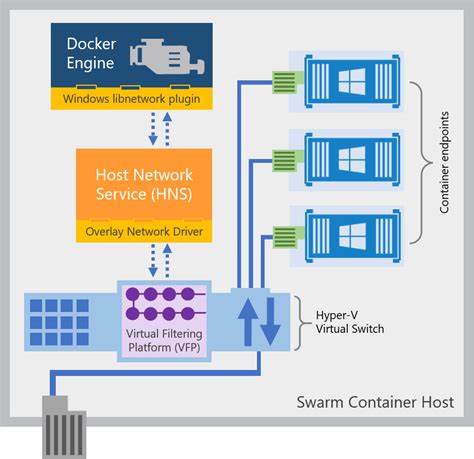
Managing Networks for Windows Containers using Docker CLI
In this section, we will explore the process of managing networks for Windows containers using the Docker CLI, offering a comprehensive overview of the key commands and techniques required to efficiently configure and manage networking in a Windows container environment.
Starting with an outline of the benefits and importance of effective network management for containerized applications, we will then delve into the various commands available within the Docker CLI that facilitate the creation, configuration, and maintenance of container networks. These commands enable the establishment of reliable and secure communication channels between containers, facilitating seamless coordination and data exchange between different containerized services and components.
- We will examine the fundamental networking concepts relevant to Windows containers and discuss how they differ from traditional network setups.
- Throughout the discussion, we will explore the use of Docker networking features, such as bridge networks, overlay networks, and MACVLAN networks, to fulfill different networking requirements and scenarios in a Windows container environment.
- We will also cover the process of linking containers within a network and demonstrate how to establish connectivity between containers while ensuring isolation and security.
- Additionally, we will highlight advanced networking capabilities provided by Docker, such as multi-host networking and port mapping, and explore their benefits in a Windows container context.
By the end of this section, you will have a solid understanding of how to effectively manage networks for Windows containers using the Docker CLI, enabling you to create robust and scalable containerized applications with seamless networking capabilities.
Integrating Docker Windows Network with Existing Infrastructure
Incorporating Docker Windows Network into your current infrastructure allows for seamless integration and enhanced connectivity. By merging the power of Docker and Windows Network capabilities with your existing systems, you can optimize network performance, increase scalability, and streamline operations.
Enhancing Connectivity: Leveraging Docker Windows Network enables improved communication and collaboration between different elements of your infrastructure. This integration eliminates the need for separate network setups and facilitates efficient data transfer and sharing across various components.
Scaling with Ease: Introducing Docker Windows Network into your infrastructure architecture ensures flexibility and scalability. With the ability to easily add or remove containers and applications, you can dynamically adapt your network to accommodate changing business requirements. This scalability empowers your organization to grow without limitations.
Streamlining Operations: Integrating Docker Windows Network with your existing infrastructure simplifies management and administration tasks. This integration consolidates network configurations, allowing for centralized control and monitoring. By streamlining processes, you can reduce complexity, minimize errors, and increase productivity.
Increasing Efficiency: By combining Docker Windows Network with your current infrastructure, you can optimize resource utilization and enhance overall efficiency. This integration allows for efficient allocation and distribution of network resources, ensuring optimal performance and minimizing downtime. As a result, your organization can maximize productivity and deliver seamless user experiences.
Enabling Collaboration: The integration of Docker Windows Network with existing infrastructure promotes collaboration and empowers cross-functional teams. This integration facilitates smooth communication and real-time data exchange between various departments, enabling seamless collaboration and enhancing productivity.
Unleashing Innovation: By embracing the capabilities of Docker Windows Network within your infrastructure, you create a foundation for innovation. This integration empowers your organization to explore new technologies, experiment with different applications, and drive the development of cutting-edge solutions.
Incorporating Docker Windows Network into your existing infrastructure has the potential to revolutionize your network architecture, unlock new possibilities, and drive business success.
Securing Communication within the Docker Windows Environment

When operating in a Docker Windows environment, it is crucial to prioritize the security of network communication, ensuring that data transfers and interactions within the network are protected from unauthorized access and potential vulnerabilities. This section aims to explore various strategies and best practices to secure communication within the Docker Windows environment.
Encryption: One fundamental approach to enhance network security is through encryption, which involves encoding information into a format that can only be accessed by authorized parties. By implementing encryption techniques such as Transport Layer Security (TLS) or Secure Sockets Layer (SSL), organizations can protect sensitive data transmitted between Docker containers and external networks.
Access Control and Authentication: Establishing strict access control and authentication mechanisms are essential to prevent unauthorized access to Docker Windows networks. Employing access control methods, such as firewall rules and network segmentation, can restrict communication to only necessary services and prevent potential lateral movement within the network. Additionally, robust authentication protocols, including password-based authentication or multi-factor authentication, can further enhance network security by ensuring only authenticated users can access Docker containers and their associated services.
Regular Security Updates: Keeping Docker Windows environments up to date with the latest security patches is crucial in minimizing vulnerabilities. Regularly applying security updates and patches to both the underlying host system and the Docker containers can address known security flaws and prevent potential exploits that may compromise the network's integrity.
Network Monitoring: Implementing robust network monitoring tools and practices can enable organizations to proactively detect and respond to potential security incidents within the Docker Windows environment. Employing intrusion detection systems (IDS) and conducting regular network audits can help identify any suspicious activities, unauthorized access attempts, or potential security breaches, allowing for prompt mitigation actions.
Secure Configuration: Configuring Docker Windows networks securely involves implementing best practices such as disabling unnecessary services, limiting communication ports, and utilizing secure communication protocols. By following secure configuration guidelines, organizations can minimize the attack surface and reduce potential vulnerabilities that can be exploited by malicious actors.
Regular Security Assessments: Conducting periodic security assessments and vulnerability scans within the Docker Windows environment can help identify any potential weaknesses and areas that require further attention. By performing such assessments, organizations can proactively address security gaps and implement necessary remediation steps to strengthen the overall network security posture.
In summary, securing communication within the Docker Windows environment is of paramount importance to protect sensitive data, prevent unauthorized access, and maintain the integrity of the network. By implementing encryption, access control measures, regular security updates, network monitoring, secure configuration, and periodic security assessments, organizations can significantly enhance the overall security of their Docker Windows networks.
Troubleshooting Common Issues in Docker Windows Network
In this section, we will explore common challenges that users may encounter when working with Docker on Windows and how to resolve them. We will discuss various problems that might arise within the network environment and provide troubleshooting tips and solutions. By understanding these common issues and their resolutions, users can effectively troubleshoot network-related problems and ensure seamless operations.
One common issue that users may face is connectivity problems within the Docker network. This could include scenarios where containers are unable to communicate with each other or with external sources. Additionally, users might encounter difficulties in accessing container services from the host machine or vice versa. Troubleshooting techniques and solutions will be explored to identify and resolve such connectivity issues.
Another challenge that users might come across is performance degradation within the Docker network. Slow network speeds, high latency, or inconsistent connection stability can greatly impact the performance of containers and applications running within them. We will discuss ways to diagnose performance-related problems and provide optimization methods to enhance network performance in Docker on Windows.
Furthermore, security concerns within the Docker network can also arise. Users might face vulnerabilities, unauthorized access, or other security breaches that can compromise the network's integrity and confidentiality. This section will provide insights into common security issues within Docker on Windows and offer strategies to mitigate these risks, including best practices for securing container and network configurations.
Lastly, we will address some miscellaneous troubleshooting scenarios that users may encounter within the Docker Windows network. These can include issues related to DNS resolution, port conflicts, or container-specific network problems. By discussing these scenarios and providing step-by-step troubleshooting approaches, readers will be equipped with the knowledge and tools to effectively troubleshoot and resolve a wide range of network-related issues in Docker on Windows.
Best Practices for Docker Windows Network Configuration

Introduction: This section highlights the key practices for configuring networks in the Docker environment for Windows. It aims to provide guidelines and recommendations to ensure an efficient and secure network setup without relying on the specifics of Docker, Windows, or equivalent analogs. By following these best practices, users can optimize their network configurations and enhance their overall system performance.
Secure Network Segmentation: A crucial aspect of network configuration involves the segmentation of networks to enhance security and isolate different components. By establishing separate networks or subnets, organizations can minimize the risk of unauthorized access and potential data breaches. Through proper segmentation, system administrators can define boundaries and control the flow of network traffic effectively, while ensuring that sensitive information remains protected.
Proactive Network Monitoring: Regularly monitoring network activity is essential to detect and address potential security threats or performance issues promptly. By implementing proactive network monitoring strategies, organizations can identify any anomalies, such as unusual traffic patterns or suspicious activities, and take necessary actions to mitigate risks. This includes utilizing network monitoring tools and techniques to ensure constant surveillance and prompt response to any network-related incidents.
Efficient Bandwidth Management: Optimizing bandwidth allocation is crucial for maintaining a smooth network environment. By implementing efficient bandwidth management practices, organizations can prioritize critical applications or services, preventing network congestion and ensuring optimal performance. This can include techniques such as Quality of Service (QoS) policies to prioritize specific network traffic, bandwidth limitation for non-essential services, and bandwidth reservation for critical applications.
Load Balancing and High Availability: Load balancing techniques play a significant role in achieving high network availability and preventing resource bottlenecks. By distributing network traffic across multiple servers or endpoints, organizations can ensure optimal utilization of resources, improve network performance, and minimize downtime. Implementing load balancing strategies, such as round-robin, least connection, or session-based distribution, can help achieve high availability and scalability within the network infrastructure.
Effective Firewall Configuration: Proper firewall configuration is essential to safeguard network environments from unauthorized access, malicious attacks, and potential vulnerabilities. It is crucial to define appropriate firewall rules, such as allowing only necessary ports and protocols, implementing a demilitarized zone (DMZ), or utilizing network address translation (NAT) techniques for additional security layers. Regularly reviewing and updating firewall rules can ensure continuous protection and adherence to security best practices.
Conclusion: By following these best practices for Windows network configuration, organizations can establish efficient, secure, and scalable network environments within their Docker or similar setups. Emphasizing secure network segmentation, proactive monitoring, efficient bandwidth management, load balancing, and effective firewall configuration can help optimize network performance, mitigate risks, and ensure the smooth operation of critical applications and services.
Docker Networking Tutorial (Bridge - None - Host - IPvlan - Macvlan - Overlay)
Docker Networking Tutorial (Bridge - None - Host - IPvlan - Macvlan - Overlay) by Anton Putra 10,856 views 2 months ago 20 minutes
FAQ
What is Docker Windows Network?
Docker Windows Network is a networking feature in Docker that allows containers running on Windows to communicate with each other and with the host machine.
How does Docker Windows Network work?
Docker Windows Network uses virtual network adapters on the host machine to create a virtual network for container communication. It also provides NAT (Network Address Translation) to allow containers to access resources outside the virtual network.
Is Docker Windows Network similar to a network on a physical host machine?
Yes, Docker Windows Network acts as an equivalent analog to a network on a physical host machine. It provides similar capabilities and functionality for container communication.
Can containers on Docker Windows Network communicate with containers on a different host?
Yes, containers on Docker Windows Network can communicate with containers on a different host by using IP addresses or DNS names of the host machines. However, it may require additional network configuration and setup.




