In the vast realm of technology and computing, there exists a fascinating tool that promises to revolutionize the way we interact with our operating systems. Within this captivating realm, a method arises that allows us to navigate an intricate labyrinth of commands and programs in a unique and efficient manner. Embrace the power of aliases and shortcuts in the Linux terminal, and witness the birth of a new level of control and convenience.
Imagine a world where you could effortlessly communicate with your machine, where a single word could initiate a sequence of complex operations. Picture the ability to invoke an alternate identity, a "pseudonym," that grants you access to a wealth of predefined commands and shortcuts. With this newfound power, you can navigate the intricate web of your Linux operating system with ease, effortlessly executing an array of tasks.
Indulge in the freedom to express your desires through a simple combination of characters, as you forge a connection with your Linux environment. The art of creating aliases becomes a gateway to unlocking the true potential of your terminal experience. Immerse yourself in a world of boundless innovation and seamless productivity, as you discover the wonders that await within the realm of pseudonyms.
Creating Alternate Identities with Docker Command Line on Linux
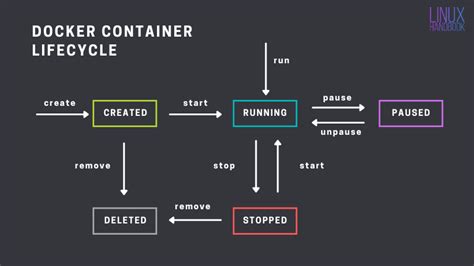
In the world of technology and development, it is often necessary to create alternate identities or pseudonyms for various reasons. The Docker command line in Linux provides a powerful and versatile toolset to accomplish this task. By leveraging the capabilities of the terminal, users can easily create, manage, and access different personas within their Docker environment.
One of the key advantages of using Docker on Linux is the ability to create multiple containers, each acting as a separate entity with its own set of unique attributes. These containers can be thought of as virtual environments that can be configured and customized according to specific requirements. By utilizing the Docker exec command, users can access and interact with these containers, effectively assuming the identity of the persona associated with each container.
Through the Docker exec command on Linux, users can create pseudonyms or alternate identities by launching new containers and assigning them distinct names. These names can represent different individuals, roles, or personas, allowing users to compartmentalize their work and efficiently switch between different contexts. By executing commands within these designated containers, users can operate as specific identities without affecting other containers or processes running on the system.
Furthermore, Docker also provides the flexibility to manage and modify these pseudonyms as needed. Through commands such as Docker rename and Docker rm, users can easily rename or remove containers, effectively changing or eliminating the associated pseudonyms. This level of control allows for seamless management of virtual identities, ensuring smooth transitions and updates within the Docker environment.
In conclusion, the Docker command line on Linux offers a powerful solution for creating pseudonyms and alternate identities. By leveraging the capabilities of Docker containers, users can easily compartmentalize their work, assume different personas, and seamlessly switch between various contexts. This flexibility and control contribute to a more efficient and organized development workflow, enhancing productivity and facilitating the management of multiple identities within the Docker environment.
A Simple Guide to Using Command Line Instructions
In this section, we will provide you with a straightforward guide on how to navigate and interact with your computer's command line interface. The command line interface, often referred to as the terminal, allows you to input specific instructions and execute various tasks efficiently. By mastering a few fundamental command line instructions, you can perform a wide range of actions and manage your computer effortlessly.
- Get Familiar with Basic Commands
- Navigate the File System
- Create and Edit Files
- Execute Programs and Processes
- Use Command Line Tools and Utilities
Before diving deeper into the world of command line instructions, it is essential to become familiar with some fundamental commands. These commands serve as building blocks for more complex instructions and enable you to navigate through your computer's directory structure, create and manipulate files and folders, and perform other essential tasks.
Once you have a good grasp of basic commands, it's time to learn how to navigate your computer's file system using the command line. By understanding how to move between directories, list files and folders, and access different locations on your computer, you can efficiently locate and manage your files without relying on graphical interfaces.
Another crucial skill to develop is the ability to create and modify files directly from the command line. Whether you need to create a new text file, edit an existing document, or even manipulate data within files, understanding how to use command line tools effectively can save you time and effort.
Besides managing files and directories, the command line is also a powerful tool for executing programs and processes. By using command line instructions, you can launch applications, run scripts, and even perform complex system administration tasks. Understanding how to execute programs from the command line empowers you to automate tasks and streamline your workflow.
One of the advantages of working with the command line is the vast array of tools and utilities available. From text processing utilities to network troubleshooting tools, the command line offers a rich ecosystem of applications specifically designed to enhance your productivity and efficiency. In this section, we will explore some commonly used command line tools and demonstrate how to leverage their capabilities.
With the knowledge and skills gained from this simple guide, you will be equipped to tackle various tasks using command line instructions. Whether you're a beginner or an experienced user, mastering the command line can greatly enhance your capabilities and make you more proficient in managing and interacting with your computer system.
Enhancing Security and Privacy in Docker Container

Ensuring the safety and confidentiality of data within Docker containers is of utmost importance for organizations and individuals alike. By implementing robust security measures, one can significantly enhance the privacy and protection of sensitive information.
One essential aspect of fortifying security is implementing access controls. By employing stringent authentication mechanisms, controlling user permissions and privileges, and regularly updating access credentials, organizations can reduce the risk of unauthorized access and potential data breaches.
Another critical consideration for enhancing security is implementing secure network communication within Docker containers. Employing encryption protocols such as Transport Layer Security (TLS) and Virtual Private Networks (VPNs) can significantly bolster data privacy by ensuring that all communications are encrypted and protected from malicious actors.
In addition to access controls and secure communication, actively monitoring and managing container vulnerabilities is crucial for maintaining a secure environment. Regularly scanning for and patching vulnerabilities can prevent potential exploits and keep containers protected from emerging threats.
Moreover, implementing container isolation techniques can prevent the spread of malware and limit the impact of potential security breaches. Utilizing tools like Docker's isolation features, such as container namespaces, resource quotas, and capabilities, can help create a more secure and resilient container environment.
Furthermore, it is essential to keep Docker containers and their underlying host systems up to date with the latest security patches and updates. By promptly applying patches and staying informed about security advisories, organizations can mitigate the risk of known vulnerabilities being exploited.
| Benefits of Enhancing Security and Privacy in Docker Containers: |
|---|
| 1. Protection against unauthorized access and data breaches. |
| 2. Increased data privacy and confidentiality. |
| 3. Reduced risk of malware propagation and containment of security breaches. |
| 4. Compliance with data protection regulations and industry standards. |
| 5. Enhanced trust and confidence from customers and stakeholders. |
Build YOUR OWN Dockerfile, Image, and Container - Docker Tutorial
Build YOUR OWN Dockerfile, Image, and Container - Docker Tutorial by Techno Tim 247,193 views 2 years ago 18 minutes
FAQ
What is Docker Exec Linux?
Docker Exec Linux is a command used to execute a command in a running Docker container.
How do I create pseudonyms using terminal with Docker Exec Linux?
To create pseudonyms using terminal with Docker Exec Linux, you need to first start a Docker container, then use the Docker Exec command to execute a command inside the container. This command can be used to create and manage pseudonyms.
Can I create multiple pseudonyms in a single Docker container?
Yes, you can create multiple pseudonyms in a single Docker container. Each pseudonym will have its own separate environment within the container.
Are the pseudonyms created using Docker Exec Linux persistent?
No, the pseudonyms created using Docker Exec Linux are not persistent. They exist only as long as the container is running. Once the container is stopped or removed, the pseudonyms will no longer be available.
Can I use Docker Exec Linux to execute commands on a remote Docker container?
Yes, Docker Exec Linux can be used to execute commands on a remote Docker container. You just need to specify the appropriate flags and connection details to connect to the remote Docker host.
How do I create pseudonyms using Docker Exec Linux?
To create pseudonyms using Docker Exec Linux, you need to access the terminal and execute the "docker exec" command followed by the container ID or name, and then specify the command to create the pseudonym. This allows you to have multiple pseudonyms for the same container, each with its own unique name.
Can I create pseudonyms for containers in Docker without using the terminal?
No, creating pseudonyms for containers in Docker requires the use of the terminal. The "docker exec" command needs to be executed in the terminal to access the container and create the pseudonyms.




