Imagine a world where the conventional way of handling file permissions in a Linux environment is completely transformed. A groundbreaking solution has emerged, challenging the traditional methods and ushering in a new era of efficiency and flexibility.
In this visionary paradigm shift, the power of Docker technology is harnessed to revolutionize the way file permissions are managed. Gone are the days of tedious and error-prone manual configurations – now, a seamless and automated process takes center stage, empowering users with a never-before-seen level of control.
Enter the realm of a permission volume, an ingenious concept that redefines the boundaries of possibility. With its immense potential, the permission volume presents a game-changing solution that simplifies the complex nature of file permissions, making it accessible to both novices and experts alike.
Seamlessly integrating with the Linux ecosystem, the permission volume acts as a catalyst for innovation. It provides a secure and isolated environment where files and directories can coexist within distinct realms, each with its own set of permissions. This new approach eliminates conflicts and enhances collaboration, enabling teams to work harmoniously without compromise.
Docker Security: Understanding Linux Authorization Scale
In the world of containerization, ensuring security is of utmost importance. Docker, the popular container platform, offers a range of security features to protect your applications. One crucial aspect to consider is Linux authorization scale, which plays a pivotal role in safeguarding your containers and their associated resources.
Linux authorization scale refers to the comprehensive set of permissions and access controls that can be applied within a Docker environment. It allows you to define who can access certain resources and what actions they can perform on them. By understanding and effectively managing Linux authorization, you can strengthen the security posture of your Docker deployment.
- Managing User Permissions: User permissions are fundamental in controlling access to Docker containers. By assigning appropriate roles and privileges to different users, you can limit their actions and mitigate the risk of unauthorized access.
- Implementing Role-Based Access Control (RBAC): RBAC is a powerful mechanism that enables fine-grained control over permissions. It allows administrators to define roles and assign them to users or groups, ensuring that only authorized individuals can perform specific actions within the Docker environment.
- Using Access Control Lists (ACLs): ACLs provide an additional layer of control by allowing you to define permissions beyond the traditional owner-group-world paradigm. With ACLs, you can grant or revoke specific permissions for individual users or groups, granting granular access to resources.
- Utilizing Mandatory Access Control (MAC): MAC is a security model that goes beyond traditional discretionary access control. By enforcing mandatory access policies, MAC restricts the capabilities of users, even if they have elevated privileges. It provides an additional layer of defense against unauthorized actions.
- Monitoring and Auditing Permissions: Regularly monitoring permissions and auditing access logs is a crucial part of maintaining a secure Docker environment. By keeping a close eye on permissions, you can detect any unauthorized activities or potential security breaches, allowing you to take timely actions.
In conclusion, understanding Linux authorization scale within Docker is vital for securing your containerized applications. By effectively managing user permissions, implementing RBAC, utilizing ACLs, leveraging MAC, and monitoring permissions, you can create a robust security framework that protects your Docker environment from potential threats.
An Introduction to Docker: Understanding containerization technology
Containers have revolutionized the world of software development and deployment, offering a lightweight and efficient approach to running applications. One key player in this field is Docker, a powerful platform that simplifies the process of creating, packaging, and running applications in containers.
What is Docker?
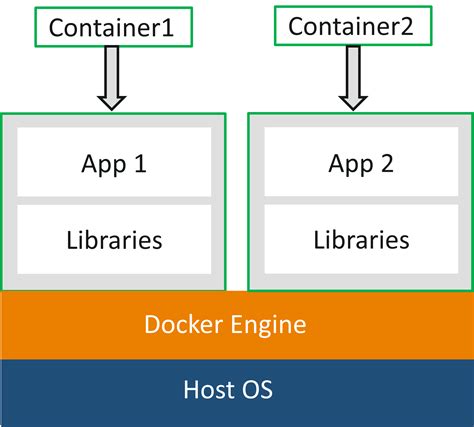
Docker is a containerization platform that allows developers to build and package their applications along with all their dependencies into a self-contained unit called a container. Containers are isolated environments that can run on any system, providing consistency and portability across different environments.
Key Features and Benefits
Docker provides several key features and benefits that make it an attractive choice for developers and system administrators. One of its main advantages is the ability to create lightweight and isolated containers, which consume fewer resources compared to traditional virtual machines. This leads to improved efficiency and scalability, allowing for faster application deployment and easier management.
Moreover, Docker offers a wide range of functionality, including the ability to quickly spin up multiple instances of containers, manage networking and storage, and automate the deployment process. Its flexibility and robust tooling make it a popular choice for building, testing, and deploying applications in various environments.
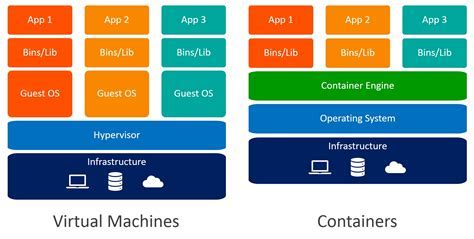
Containerization vs. Virtualization
It's essential to understand the distinction between containerization and virtualization. While traditional virtualization involves running multiple virtual machines on a host operating system, each with its own kernel and system resources, containerization leverages the host operating system's kernel to run multiple containers. This results in better performance, as containers are lighter and have minimal overhead.
Conclusion
Docker has transformed the way applications are packaged and deployed, providing a flexible and efficient approach to containerization. By encapsulating an application along with its dependencies, Docker enables consistent and portable deployments across different environments. Its features and benefits make it a valuable tool for developers and system administrators, streamlining the software development lifecycle and promoting scalability and efficiency.
Understanding the Role of Linux Access Controls in Docker Containers
In the realm of containerization technology, an important aspect to consider is the management of access controls within the Linux environment. These access controls dictate the permissions granted to different entities, such as users and processes, determining what actions they can perform on the system. When it comes to Docker containers, understanding Linux permission volumes becomes crucial in optimizing security and ensuring proper functionality.
Overview of Linux Access Controls
Linux access controls encompass a range of mechanisms that regulate access to resources and actions within the operating system. This includes file permissions, ownership, access lists, and capabilities. These controls are essential for maintaining system integrity, protecting sensitive data, and facilitating the secure execution of processes.
File Permissions: File permissions define the level of access that different users or groups have to a particular file or directory. The three fundamental permission types are read, write, and execute, which can be assigned to the owner, group, or others.
Ownership: In Linux, every file and directory is associated with an owner and a group. The owner has certain privileges and can determine the permissions of others, while the group can be granted specific permissions to the file or directory.
Access Lists: Access control lists (ACLs) extend the basic file permissions by providing more granular control over access rights. They enable the definition of multiple users or groups with distinct permissions to a file or directory.
Capabilities: Linux capabilities allow processes to perform privileged actions without granting them full root privileges. This fine-grained approach enhances security and reduces the attack surface of containerized applications.
By comprehending the intricate nature of Linux access controls, Docker users can effectively manage permissions within their containers. This understanding enables the implementation of appropriate access restrictions, minimizing the risk of unauthorized actions and potential security breaches.
Proven Strategies for Enhancing Security of Containers
In today's rapidly evolving landscape of software development and deployment, Docker containers have emerged as a popular solution for packaging applications along with all their dependencies. However, ensuring the security of these containers is of paramount importance to protect sensitive data and prevent unauthorized access. This section presents a comprehensive set of best practices and strategies to help you fortify the security of your Docker containers.
FAQ
What is Docker?
Docker is an open-source platform that allows developers to automate the deployment and scaling of applications inside containers.
How does Docker create a Linux permission volume?
Docker creates a Linux permission volume by mapping the file system permissions of the host machine to the container. This allows for better control and management of access rights within the containerized environment.
Can you explain the benefits of Docker's Linux permission volume?
Sure! Docker's Linux permission volume offers several benefits. Firstly, it ensures that the containerized applications have the necessary access rights to the host machine's files and directories, while still maintaining isolation and security. Secondly, it simplifies the management of permissions, as any changes made to the host's permissions are automatically reflected within the container. Lastly, it allows for more control over the access privileges granted to different containers, enhancing the overall security of the system.




