When it comes to employing Docker technology on a Windows operating system, organizations face a perplexing dilemma - the obstacle of limited accessibility to Windows containers. This predicament arises from a range of intricate factors that hinder smooth and seamless interaction with Docker containers running on Windows-based platforms. The arduous endeavor of gaining unrestricted access has become a matter of great significance and urgency for enterprises seeking to fully leverage the benefits of Docker in their Windows-based ecosystems.
The Conundrum of Inhibited Interaction
One of the primary hurdles impeding unhindered access to Docker Windows containers is the intricate web of security measures and permissions in place. Windows, being an inherently secure operating system, has implemented stringent protocols to safeguard both the system and user data. Consequently, interacting with Docker containers, which are designed to be agile and portable, can be met with resistance when attempting to establish connections with restricted resources. This conundrum poses a considerable challenge to organizations navigating the terrain of Windows containers, as it stifles the seamless flow of information and inhibits the efficient utilization of Docker's vast capabilities.
The Pursuit of Empowered Utilization
Unlocking the potential of Docker containers within a Windows environment demands a concerted effort to overcome the barriers enforced by the operating system itself. Organizations across industries are actively seeking solutions to bridge the gap between Windows and Docker, enabling fluid interaction without compromising the security offered by Windows. As this demand intensifies, innovation and adaptation emerge as the driving forces behind transformative advancements that aim to empower enterprises in fully embracing Docker's vast possibilities while harnessing the familiarity and reliability of the Windows operating system.
The Growing Challenge of Restricted Entry to Windows Containers in Docker Environment
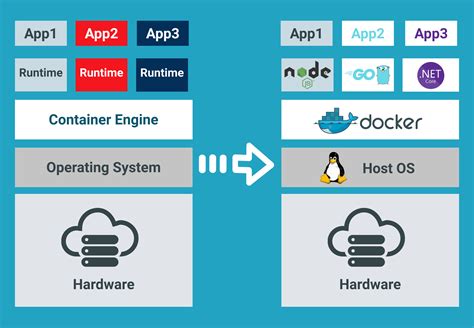
Over the past few years, the use of Windows containers in the Docker ecosystem has been gaining significant popularity. However, along with their increasing adoption, there has emerged a consequential issue hampering the smooth operation of these containers. This challenge revolves around the denied access to Windows containers within the Docker environment, impeding the seamless utilization of their capabilities.
As organizations integrate Windows containers into their development and deployment pipelines, the restricted access problem becomes a pressing concern. The inability to effectively access and utilize the functionalities offered by these containers hinders the efficient deployment of applications and services. Consequently, successfully tackling this growing issue becomes paramount to ensuring the smooth and uninterrupted functioning of Docker Windows containers.
- Emergence of Access Limitations: The first aspect to consider is the increasing prevalence of access limitations encountered while utilizing Windows containers in a Docker environment. These restrictions can arise due to various factors such as misconfigured firewall settings, limited user permissions, or even compatibility issues between the host system and the container.
- Impact on Development and Deployment: The denied access to Windows containers significantly impacts the development and deployment processes. Developers face roadblocks when attempting to access the containerized resources required for debugging, testing, and optimizing their applications. Moreover, limited access can lead to delays in the rollout of new features and updates, hampering the agility of organizations deploying containerized applications.
- Mitigation Strategies: To address this growing challenge, organizations and system administrators can implement several mitigation strategies. These may include fine-tuning firewall configurations to allow secure access, granting appropriate user permissions, and ensuring compatibility between the host system and the containers. Additionally, employing robust monitoring and troubleshooting techniques can assist in identifying and resolving access-related issues more effectively.
- The Role of Containerization Technologies: Understanding the role of containerization technologies, such as Docker, in enabling or exacerbating the restricted access problem is vital. Exploring containerization-specific obstacles and examining potential advancements can provide insights into overcoming the limitations that hinder the successful utilization of Windows containers.
As the utilization of Windows containers in Docker ecosystems continues to expand, addressing the growing challenge of denied access becomes imperative. By acknowledging the emergence of access limitations, understanding their impact on development and deployment processes, implementing relevant mitigation strategies, and exploring the role of containerization technologies, organizations can forge a pathway toward a more seamless and efficient utilization of Windows containers within the Docker environment.
Distinguishing Linux and Windows Containers in Docker
In this section, we will explore the distinctive characteristics and key differences between Linux and Windows containers within the Docker platform.
Docker, known for its versatility and portability, offers support for both Linux and Windows containers. Understanding the fundamental disparities between these two container types is essential for successfully managing and deploying containerized applications.
One of the main differentiating factors lies in the operating systems each container supports. Linux containers are designed to run on Linux-based operating systems, while Windows containers are specifically tailored to run on Windows-based operating systems.
Another key distinction is the mechanism used for isolating processes within the containers. Linux containers rely on lightweight mechanisms such as namespaces and control groups to provide process isolation, while Windows containers utilize isolation techniques based on Windows features like namespaces and capabilities.
Container images also differ between Linux and Windows containers. Linux container images are typically based on lightweight and minimalistic Linux distributions, emphasizing efficiency and small footprint. On the other hand, Windows container images are based on Windows Server Core or Nano Server, offering compatibility with Windows applications and libraries.
Networking is yet another area where Linux and Windows containers diverge. Linux containers leverage the Linux network stack and interfaces, providing a wide range of networking options and flexibility. In contrast, Windows containers utilize the Windows network stack, allowing for seamless integration with Windows-based networking services and protocols.
These distinctions between Linux and Windows containers must be taken into account when selecting the appropriate container type for a specific application or environment. Understanding their subtle yet significant differences is crucial for ensuring smooth deployment and optimal performance of containerized applications within the Docker ecosystem.
Understanding the Significance of Access Control in Docker Windows Container
In today's evolving technology landscape, the aspect of managing access to resources has become increasingly crucial. In the context of Docker Windows Containers, access control plays a vital role in ensuring the security and integrity of the system. This section aims to delve deeper into the significance of access control and its impact on the overall functionality of Docker Windows Containers.
Access control, in the context of Docker Windows Containers, refers to the process of governing and regulating the permissions and privileges bestowed upon users and applications within the container environment. It encompasses a range of mechanisms that enable administrators to define and enforce access policies, ensuring that only authorized entities have the right to access and perform specific operations.
Effective access control mechanisms not only enhance the security posture of Docker Windows Containers but also aid in maintaining the reliability and performance of the system. By implementing granular access controls, administrators can mitigate the risk of unauthorized access, data breaches, and malicious activities that can potentially compromise the containerized environment.
A key aspect of access control is the concept of user authentication and authorization. Through robust authentication processes, Docker Windows Container ensures that only legitimate users with valid credentials are granted access. Additionally, authorization mechanisms allow administrators to assign specific roles and permissions to users based on their responsibilities and requirements, preventing unauthorized actions and enforcing the principle of least privilege.
| Access Control Mechanisms | Benefits |
|---|---|
| Role-Based Access Control (RBAC) | - Enables fine-grained control over user permissions - Simplifies the management of user access - Reduces the risk of unauthorized actions |
| Access Control Lists (ACLs) | - Provides flexibility in defining access rights - Allows for precise control over individual resources - Accommodates complex access scenarios |
| Multi-Factor Authentication (MFA) | - Adds an extra layer of security to the authentication process - Mitigates the risk of unauthorized access - Protects against password-related vulnerabilities |
Overall, understanding and effectively employing access control mechanisms in Docker Windows Containers are paramount in establishing a secure and well-regulated environment. By comprehending the role of access control and leveraging appropriate mechanisms, administrators can fortify the resilience and protect the sensitive assets within the containerized ecosystem.
Common Challenges Faced When Entry is Prohibited to Docker Windows Instance
In the realm of working with Docker Windows containers, certain obstacles might arise when attempting to gain entry into a specific instance. These challenges can vary in nature and complexity, creating hurdles for developers and administrators seeking access to the containerized environment.
One potential hurdle involves the issue of authentication, where access to the Windows container is restricted due to inadequate permissions or misconfigured security settings. This barrier necessitates a thorough investigation into the authentication mechanisms in place and the identification of any potential gaps or misconfigurations.
Another common challenge lies in the establishment of network connectivity to the Docker Windows container. This can be hindered by various factors such as firewall restrictions, network misconfigurations, or non-compliant network policies. Resolving this issue requires a careful examination of the network setup and the implementation of appropriate adjustments to enable seamless connectivity.
Furthermore, a frequently encountered difficulty pertains to resource allocation and utilization within the Windows container. This can manifest in the form of limited memory, CPU overutilization, or constrained disk space, leading to denied access or degraded performance. Effective management of resources through proper monitoring and allocation strategies is essential to overcome this challenge.
Lastly, the challenge of troubleshooting and debugging arises when denied access to a Docker Windows instance prevents effective diagnosis of potential issues and resolutions. Without the ability to delve into the container environment, developers and administrators may face significant hurdles in identifying and resolving underlying problems. Implementing robust logging mechanisms and adopting comprehensive debugging techniques are crucial in addressing this challenge.
Addressing these common challenges, among others, is vital to ensure efficient utilization and accessibility of Docker Windows containers. By understanding the potential barriers and employing appropriate strategies, developers and administrators can overcome denied access and foster a robust and reliable containerized environment.
Exploring the Security Risks Associated with Unauthorized Access to Docker Windows Container
In this section, we delve into the various risks that arise when unauthorized individuals gain entry to a Windows container deployed on a Docker platform. Diving into the realm of container security, we investigate the potential consequences and vulnerabilities that stem from unauthorized access to these valuable resources.
Unauthorized entry into a Windows container poses a myriad of security risks, compromising the integrity and confidentiality of the contained software and data. Such access grants individuals unauthorized privileges, allowing them to manipulate and exploit the container environment for malicious purposes.
One primary security risk associated with unauthorized access is the potential for information leakage and unauthorized data modification. By gaining entry to the container, unauthorized individuals can exfiltrate sensitive data, such as intellectual property or personally identifiable information, jeopardizing the privacy and reputation of the organization.
Additionally, unauthorized access to a Windows container provides a foothold for attackers to launch further attacks within the containerized environment. This includes introducing malware, performing privilege escalation, or exploiting vulnerabilities within the container host and underlying systems.
Furthermore, unauthorized access presents a significant risk to the availability of the containerized application and its associated services. Attackers may disrupt the functionality of the container, causing service outages or denial of service attacks, resulting in financial losses and reputational damage for the organization.
To mitigate these security risks, it is vital for organizations to implement robust authentication mechanisms, access controls, and strict security measures throughout the container stack. This includes employing secure configuration practices, implementing regular patching and updates, and monitoring container activity for any signs of unauthorized access or suspicious behavior.
By understanding and addressing the security risks associated with unauthorized access to Docker Windows containers, organizations can safeguard their containerized environments, protect valuable data, and ensure the integrity and availability of critical applications and services.
Best Practices for Managing Authorization to Docker Windows Containers
In this section, we will discuss some proven strategies to effectively control and manage user access to Windows containers in the Docker environment. By implementing these best practices, organizations can ensure that only authorized users are granted access to Dockerized applications and services.
| 1. Role-Based Access Control (RBAC) | Implementing RBAC enables administrators to define and assign roles to users based on their responsibilities and access requirements. By granting permissions to roles rather than individual users, organizations can easily manage and control access to Docker Windows containers. |
| 2. Two-Factor Authentication (2FA) | Enforcing 2FA adds an extra layer of security to the access control process. By requiring users to provide a second form of authentication, such as a one-time password or a biometric verification, organizations can significantly mitigate the risk of unauthorized access to Docker Windows containers. |
| 3. Network Segmentation | Segmenting the network where Docker Windows containers reside can help limit access to only authorized users or specific IP ranges. By isolating containers in separate network segments, organizations can reduce the attack surface and minimize the potential impact of security breaches. |
| 4. Regular Security Audits | Performing regular security audits allows organizations to identify and address any vulnerabilities or misconfigurations in Docker Windows containers. By conducting thorough assessments, organizations can maintain a robust security posture and ensure that access controls are up to date. |
| 5. Continuous Monitoring and Logging | Implementing continuous monitoring and logging mechanisms enables organizations to track user activities and detect any unauthorized access attempts in real-time. By analyzing logs and monitoring system events, organizations can promptly respond to security incidents and mitigate potential risks. |
By incorporating these best practices into their Docker Windows container management strategies, organizations can establish a secure and controlled environment for running applications and services, safeguarding sensitive data, and mitigating the risk of unauthorized access.
Implementing Access Control Policies to Prevent Unauthorized Entry into Windows Container
Introduction: This section focuses on the implementation of access control policies to tackle the issue faced when individuals are not allowed to enter the confined environment of a specific technological framework on the Windows operating system. By establishing appropriate regulations, the aim is to safeguard against denied access and maintain optimum security within the system.
Tools and Techniques to Detect and Resolve Access Restrictions in Windows Containerized Environments
Access restrictions in Windows containerized environments can pose significant challenges for developers and system administrators. In order to effectively troubleshoot and resolve these issues, it is essential to utilize a range of tools and techniques that can detect and address access restrictions.
- Container Security Scanners: Utilize container security scanners to analyze containers for potential access restrictions or vulnerabilities. These tools can identify potential security risks and suggest appropriate remediation steps.
- Container Logging and Monitoring: Implement robust container logging and monitoring solutions to track access denial events. By monitoring container logs, administrators can gain insights into specific access issues and take corrective actions promptly.
- Container Access Control Lists (ACLs): Define precise access control lists for containers to regulate which processes and users have access to system resources. By carefully configuring ACLs, you can prevent unauthorized access and ensure a secure containerized environment.
- Container Runtime Security Tools: Employ container runtime security tools that provide granular visibility into container environments. These tools can flag access denial events and assist in identifying the root cause of the issue, helping administrators resolve them efficiently.
- System Profilers: Use system profilers to analyze containerized applications and their interaction with the underlying operating system. Profiling tools can detect access restrictions by monitoring system calls and identifying any denied access attempts.
- Container Health Checks: Implement regular container health checks to identify access denial issues proactively. These checks can help ensure that containers have the necessary permissions and access to required resources, minimizing the risk of denied access.
- Container Image Verification: Verify the integrity and authenticity of container images before deploying them. By ensuring that container images come from trusted sources and have not been tampered with, you can reduce the likelihood of access denial issues.
By utilizing a combination of these tools and techniques, developers and system administrators can effectively detect and resolve access restrictions in Windows containerized environments. Understanding and addressing these issues is crucial for maintaining the security and stability of containerized applications.
FAQ
What is the issue of denied access to Docker Windows Container?
The problem of denied access to Docker Windows Container refers to the situation where users encounter difficulties or restrictions when trying to access or run Windows containers within the Docker environment. This can occur due to various reasons, such as incorrect configuration, permission issues, or conflicts with other software components.




