As technology continues to advance at an astonishing pace, the need for efficient and secure application deployment has become paramount. In this era of digital transformation, organizations are constantly seeking innovative solutions to enhance their operational workflows. One such solution is the utilization of Docker containers, which provide a lightweight, portable, and isolated environment for running applications. However, when it comes to running Windows services within a Docker container, the challenge of managing user credentials arises.
Windows services, being an integral part of the operating system, often require user credentials to access system resources and perform various tasks. Traditionally, this has posed a hurdle when running services in a Docker container, as the containerized environment isolates the service from the host system's user accounts and privileges. This limitation prevents seamless integration and hampers the ability to leverage the full potential of Windows services in a containerized environment.
Thankfully, with advancements in containerization technology, it is now possible to overcome this barrier and run Windows services with user credentials in a Docker container. By enabling the use of user credentials within a containerized environment, organizations can unlock new possibilities and enhance the security and flexibility of their applications. This breakthrough allows for seamless integration of Windows services with other containerized applications, enabling efficient resource utilization, improved scalability, and enhanced security measures.
In this article, we will explore the intricacies of creating a Windows service with user credentials in a Docker container. We will delve into the underlying concepts and technologies that make this feat possible, providing a step-by-step guide to help you harness the true potential of Windows services in a containerized environment. Whether you are an IT professional seeking a solution to streamline your organization's application deployment or a developer looking to optimize the performance of your Windows services, this article will equip you with the knowledge and tools to achieve your goals.
Understanding the Integration of Services in Containerized Environments
In this section, we will delve into the concept of integrating services within containerized environments, focusing specifically on the relationship between Windows services and Docker containers. By exploring this topic, we will gain a deeper understanding of how these two components work together to enhance the functionality and flexibility of software applications.
- Exploring the Nature of Windows Services
- Understanding the Benefits of Containerization
- Examining the Relationship Between Windows Services and Docker Containers
Firstly, we will elucidate the nature of Windows services, their role in the Windows operating system, and their significance in facilitating application management and background processes. Additionally, we will highlight the advantages of containerization, including the isolation, scalability, and portability it offers to developers and system administrators.
Furthermore, we will closely examine the integration of Windows services with Docker containers, exploring how these containers provide a lightweight and consistent environment for running applications and services. We will delve into the mechanisms that allow Windows services to be executed within Docker containers and how this integration enables smoother deployment and management processes.
By gaining a comprehensive understanding of the integration of services in containerized environments, we will be better equipped to leverage the capabilities of both Windows services and Docker containers in our software development and deployment workflows.
The Significance of User Authentication in Microsoft Service Applications
User authentication plays a pivotal role in the development and deployment of secure and efficient Microsoft service applications. By validating user credentials, these applications can ensure that only authorized individuals are granted access to sensitive information and functionality. This section delves into the significance of user credentials in the context of creating and maintaining reliable and secure Windows services.
- Enhancing Security Measures
- Controlling Access to Sensitive Information
- Tracking and Auditing User Actions
- Facilitating Personalized User Experiences
User credentials form the bedrock of any robust security framework. By requiring users to provide valid authentication details, Windows services can effectively safeguard against unauthorized access and potential security breaches. Implementing a strong authentication system with rigorous password policies and multi-factor authentication adds an extra layer of protection, making it significantly harder for malicious actors to compromise the service.
User credentials allow Windows services to enforce access control mechanisms for sensitive data. By utilizing user roles and permissions, these services can ensure that only authorized users can retrieve, modify, or delete critical information. This enables businesses to maintain confidentiality, integrity, and availability of sensitive data, protecting it from unauthorized disclosure or manipulation.
User authentication also enables Windows services to track and audit user actions. By linking each action to the corresponding user credentials, these services can generate detailed logs that provide a comprehensive overview of user activities. This traceability is invaluable when troubleshooting issues, identifying malicious activities, or demonstrating compliance with regulatory requirements.
User credentials enable Windows services to personalize user experiences by tailoring functionalities and displaying customized information to individual users. By storing user preferences and settings, these services can enhance user satisfaction and streamline workflows by presenting relevant and personalized options.
In conclusion, user credentials play a critical role in the development and operation of secure Windows services. By implementing strong authentication mechanisms, controlling access to sensitive data, tracking user actions, and facilitating personalized user experiences, services can provide a robust and reliable platform for various applications and ensure the confidentiality, integrity, and availability of information.
Preparing the Docker Environment
In this section, we will focus on the initial setup of the Docker environment necessary for our project. We will establish the foundational components needed to successfully deploy and run the Windows service with user credentials in a Docker container.
First and foremost, we need to ensure that our Docker installation is properly configured. This includes verifying the installation and version of Docker on the host machine. We will also check for any compatibility issues or requirements for running Windows services within containers.
Next, we will set up the appropriate network settings for our Docker environment. This involves configuring the Docker network to support the interaction between the containerized Windows service and other services or applications it may need to communicate with. We will also define and create any necessary network bridges or overlays.
Additionally, we will discuss the considerations and steps involved in preparing the host machine for running Docker containers. This includes reviewing system requirements, ensuring proper access and permissions, and installing any required dependencies or tools to support our project's specific needs.
Lastly, we will cover the process of configuring and managing the Docker images and containers that will host our Windows service. This will include understanding and utilizing Dockerfile and docker-compose configurations to specify the necessary environment variables, volumes, and ports for our service.
By completing the steps outlined in this section, we will have a well-prepared Docker environment that is ready to deploy and run our Windows service with user credentials in a containerized environment.
Designing the Application Process
Introducing the foundation of the application experience and its functionality.
Defining Login Information for the Service
In this section, we will explore the process of specifying the user credentials required for the successful execution of our Windows service within a Docker container. By establishing the appropriate login details, we can ensure secure access and authentication for the service, enabling it to interact seamlessly with other systems and deliver its intended functionality.
User identification
When defining the user credentials, it is crucial to choose an identifier that uniquely represents the user within the system. This identifier, often referred to as the username or login name, must be distinct from others to effectively distinguish and authenticate the user. By incorporating a unique username, we can establish a secure and reliable means of identification, mitigating the risk of unauthorized access and protecting the integrity of the system.
Password protection
Another vital aspect of defining user credentials is the inclusion of a password. The password acts as an extra layer of security, ensuring that only authorized individuals with knowledge of the password can gain access to the service. By incorporating a strong and complex password, containing a combination of alphanumeric characters, symbols, and uppercase and lowercase letters, we can significantly enhance the security of the system and prevent unauthorized access.
Role-based permissions
Additionally, when defining user credentials, it is essential to assign appropriate roles or permissions to each user. Role-based permissions allow for granular control over the functions and actions each user can perform within the service. By assigning specific roles or permissions, we can ensure that users only have access to the necessary features and functionality, reducing the risk of potential security breaches or unintended modifications.
Secure storage and encryption
To maintain the confidentiality of the user credentials, it is imperative to store them securely. Utilizing encryption techniques such as hashing or salting the passwords can provide an added layer of protection against unauthorized access or data breaches. By implementing secure storage measures, we can safeguard the user credentials from potential vulnerabilities or attacks, ensuring the integrity and confidentiality of the service.
Regular password updates
Lastly, it is vital to enforce a policy that mandates regular password updates. By regularly updating passwords, we can minimize the risk of password-based attacks or unauthorized access due to compromised credentials. By encouraging users to change their passwords periodically and providing mechanisms for password expiration and renewal, we can maintain the security and robustness of the service.
Configuring the Environment for the Service
In this section, we will explore the necessary steps to set up the environment for running the service within a Docker container. By configuring the container appropriately, we can ensure the smooth execution of the service with the desired user credentials.
We will discuss the various aspects that need to be considered while preparing the Docker container, such as the necessary dependencies and configurations. Additionally, we will cover best practices for securely storing and accessing user credentials within the container.
Setting up the environment involves identifying and installing any prerequisite software or libraries required by the service to run smoothly. We will dive into the specific dependencies that may be needed, along with guidance on how to install them efficiently within the container.
To ensure the service runs with the desired user credentials, we will explore different techniques for securely storing and accessing these credentials within the container. This includes discussing the usage of environment variables, credential management tools, or specific Docker secrets.
Overall, by carefully configuring the Docker container for the service, we can foster a secure and reliable environment that allows the service to operate smoothly with the necessary user credentials.
Executing the Service Inside a Dockerized Environment
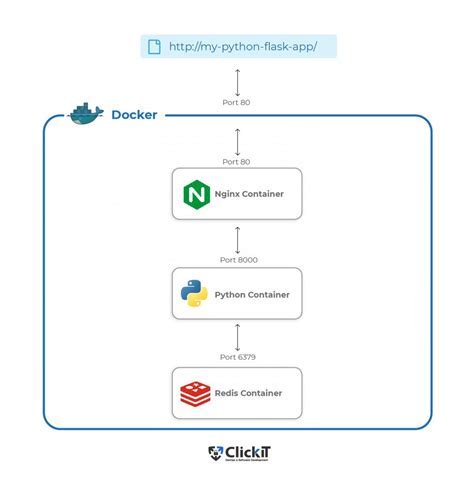
Running your custom service within a Docker container provides numerous advantages for deployment and scalability. In this section, we will explore the steps required to execute the service in the Dockerized environment without compromising security or performance.
To achieve successful execution, we will configure the Docker container to include all the necessary dependencies and configurations for the service. This will involve creating a Docker image that encapsulates the service's code, along with any additional tools or libraries required for its operation.
Once the Docker image is created, we will use Docker commands to run the container, specifying the necessary runtime options and environment variables. This will ensure that the service runs smoothly, utilizing the resources allocated within the confines of the container.
During the process, it is vital to consider security aspects and effectively manage user credentials within the Docker container. This will involve implementing secure authentication mechanisms, such as secure environment variables or secret management systems, to protect sensitive information while allowing the service to access required resources.
Additionally, monitoring and logging play a crucial role in managing the service's performance and troubleshooting any potential issues. We will explore tools and techniques for effectively monitoring the service's behavior within the Dockerized environment, ensuring its stability and efficient operation.
By following the guidelines and best practices provided in this section, you will be able to confidently deploy your Windows service within a Docker container, harnessing the benefits of containerization while maintaining security and performance.
How to install Docker on Windows - 2024 [ step by step guide ]
How to install Docker on Windows - 2024 [ step by step guide ] by TheBinaryBits 32,240 views 4 months ago 4 minutes, 27 seconds
How to create and use a Docker secret from a file
How to create and use a Docker secret from a file by How To Make Tech Work from TechRepublic 7,513 views 8 months ago 2 minutes, 10 seconds
FAQ
Can a Windows service be created within a Docker container?
Yes, it is possible to create a Windows service within a Docker container. Docker provides a platform that allows developers to containerize their applications, including Windows services.
Is it necessary to provide user credentials when creating a Windows service in a Docker container?
Yes, providing user credentials is necessary when creating a Windows service in a Docker container. User credentials are required for the service to run with the necessary permissions and access resources.




