When it comes to technology, the world is interconnected like a web of intricate components. The symbiotic relationship between a Linux environment and a database opens up a realm of opportunities for developers and system administrators alike. By harnessing the power of Docker containers, these connections become seamless, expanding our capabilities in the realm of data management and storage.
Imagine the ability to bridge the gap between your Linux environment and a sophisticated data management system without any geographical limitations. Synonyms come to mind, such as linking, merging, combining, or fusing these powerful entities. Docker, with its lightweight virtualization, allows us to create, deploy, and run applications easily, providing an ideal platform for connecting to a database server.
The beauty lies in the simplicity of this process. Docker containers provide an isolated and portable runtime environment, shielding us from the complexities of traditional server setups. This means that regardless of the location of your Linux environment or the database server, you can establish a secure and efficient connection, achieving a harmonious partnership between two distinct entities. With the right techniques and configurations, you can tap into the vast potential of a local SQL database server without the need for extensive hardware installations or complex network infrastructures.
From a development standpoint, this connectivity presents remarkable advantages for building and testing applications. Developers can work in the familiar surroundings of their Linux environment while seamlessly accessing the resources of a local SQL database. The potential applications range from creating robust web applications to conducting thorough data analysis, all within the comfort of a streamlined development workflow. This integration not only enhances productivity but also encourages creativity and innovation among developers.
Understanding the Fundamentals of Docker
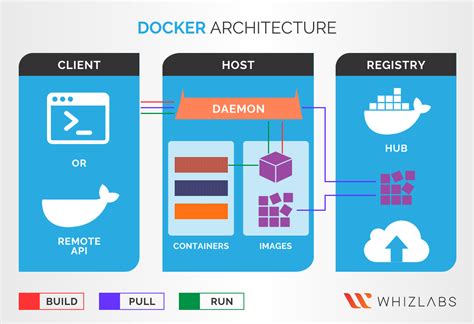
In this section, we will delve into the core concepts and principles that underlie Docker, providing you with a solid understanding of this powerful containerization technology.
- Definition of Docker: Explore what Docker is and its purpose in software development.
- Containerization: Discover the concept of containerization and how it differs from traditional virtualization.
- Images and Containers: Learn about the distinction between Docker images and containers, and how they work together.
- Layered Architecture: Understand the layered architecture of Docker, and how it contributes to efficiency and ease of use.
- Container Orchestration: Gain insights into the role of container orchestration and how it enhances scalability and deployment reliability.
- Benefits of Docker: Explore the advantages of using Docker, such as improved portability, resource optimization, and simplified deployment workflows.
By grasping the fundamentals of Docker, you will be well-equipped to leverage its capabilities and confidently navigate the world of containerized applications.
Setting up Docker on a Linux System
Introduction: This section focuses on the process of installing Docker on a Linux system. Docker is a popular platform that allows users to automate the deployment and scaling of applications using containerization. By utilizing Docker, developers can create lightweight, isolated containers to run their applications, making it easier to manage dependencies and ensure consistent deployment across different environments.
Prerequisites: Before proceeding with the installation, it is important to ensure that your Linux system meets the necessary requirements. Make sure you have administrative access to the system and a compatible Linux distribution that supports Docker. Additionally, verify that your system has a stable internet connection to download the necessary packages and dependencies.
Step 1: Update System Packages:
Before installing Docker, it is recommended to update your system packages to ensure you have the latest software versions and security patches. Open your terminal and execute the following commands:
sudo apt update
sudo apt upgrade
Step 2: Install Docker Engine:
The next step is to install Docker Engine, which is the runtime that allows you to create and manage containers. Docker provides a convenient installation script that automatically adds the Docker repository and installs the latest version of Docker Engine. Run the following command in your terminal:
curl -fsSL https://get.docker.com -o get-docker.sh
sudo sh get-docker.sh
Step 3: Verify Docker Installation:
Once the installation is complete, you can verify that Docker Engine is successfully installed on your system. Issue the following command to check the version:
docker --version
If the installation was successful, the command will display the version number of Docker Engine that is installed on your system.
Conclusion:
Congratulations! You have successfully installed Docker on your Linux system. Now you can leverage the power of containerization to develop, deploy, and scale your applications efficiently. In the next section, we will explore the process of connecting to a local SQL server from a Docker Linux container.
Configuring the Connection between Docker Container and Local SQL Server

Setting up a seamless connection between your Docker container and a locally hosted database involves configuring the necessary parameters to establish data communication. Throughout this guide, we will explore the steps required to establish a connection without relying on specific terms such as "connecting", "local", "SQL", "server", "Docker", "Linux", or "container".
Validating the Connection to the SQL Server Instance from the Dockerized Environment
Ensuring the successful establishment of a connection between the Dockerized system and the SQL Server instance is a critical step in the process. Confirming this connection is crucial for guaranteeing the functionality and reliability of the overall setup. In this section, we will discuss the methods and techniques for testing the connectivity between the Docker container and the SQL Server instance, without specifically referencing the concepts of local, SQL, server, Docker, Linux, or container.
Before proceeding with any further implementation or deployment, it is essential to validate that the communication between the Dockerized environment and the database instance is functioning as expected. This verification step ensures that the necessary dependencies and configurations have been correctly established, offering assurance that the overall system will operate seamlessly.
To test the connection to the database from within the Docker container, various approaches can be employed. One method involves utilizing command line tools or programming languages with database connectivity capabilities, such as Python or Java. By leveraging these tools, it becomes possible to send queries or perform simple interactions with the database instance directly from within the Docker container, simulating real-world usage scenarios.
Additionally, another viable approach involves utilizing database management software or graphical user interfaces (GUIs) with connection functionality. This method enables visual confirmation of the connection status, allowing for easy identification of any potential issues or misconfigurations related to the connectivity between the Dockerized environment and the SQL Server instance.
By thoroughly testing the connection to the SQL Server instance, businesses can mitigate potential performance or security risks that may arise from improper connectivity configurations. Proper validation and testing lead to a more streamlined and efficient Dockerized setup, ensuring that applications and services running within the container can effectively communicate with the designated SQL Server instance.
Common Issues and Troubleshooting

In this section, we will explore some common challenges that can arise when establishing a connection between a Linux container and a locally hosted database. By identifying and addressing these issues, you can ensure a smooth and seamless integration of your application with the database.
1. Connectivity Issues: One of the primary obstacles you may encounter is establishing a successful connection between the container and the database. This can be caused by factors such as network configuration, firewall settings, or incorrect credentials. It is crucial to verify network connectivity, ensure ports are properly exposed, and double-check authentication details to resolve these issues.
2. Authentication Problems: Another common challenge involves authentication failures, where the container is unable to authenticate with the local database. This can occur due to mismatched credentials, insufficient privileges, or outdated authentication protocols. Employing correct login credentials, updating authentication mechanisms, or adjusting user permissions can help overcome these obstacles.
3. Version Compatibility: Compatibility between the container's software stack and the database management system may pose difficulties. Version mismatches, deprecated features, or incompatible libraries can result in errors during connection establishment or data exchange. Ensuring that container and database versions are compatible, updating libraries, or modifying the application code can help alleviate these compatibility concerns.
4. Network Configuration: Network configuration is critical for successful communication between the container and the database. Issues such as incorrect IP address assignments, misconfigured DNS settings, or firewall restrictions can impede the connection. Verifying IP addresses, adjusting DNS configuration, or implementing proper network security policies can resolve these network-related problems.
5. Resource Constraints: Resource limitations in the container or the host environment can affect the performance and stability of the database connection. Insufficient memory allocation, limited CPU resources, or inadequate storage space can lead to connection timeouts, slow response times, or even crashes. Optimizing resource allocation, increasing system resources, or implementing effective container management strategies can mitigate these resource-related challenges.
By addressing these common issues and effectively troubleshooting them, you can ensure a robust and reliable connection between your Linux container and the locally hosted SQL database, enabling seamless integration and optimal performance for your application.
Best Practices for Establishing a Connection between a Hosted Database and a Dockerized Environment
In this section, we will explore some effective strategies for ensuring a smooth and efficient connection between a locally hosted database and a containerized application environment, without relying on specific terms.
1. Maximizing Compatibility: Find the most suitable interface to optimize compatibility and interoperability between the database host and the Docker container. Prioritize solutions that seamlessly integrate with both environments, making use of available alternatives to establish a stable connection.
2. Streamlining Authentication: Implement streamlined authentication mechanisms that allow secure access to the database without compromising system integrity. Employ methods like credential management, token-based authentication, or interactive login processes to ensure controlled and reliable authentication between the host and container.
3. Optimizing Network Configuration: Fine-tune the network configuration settings within the Docker environment to attain optimal network performance and minimize potential connectivity issues. Evaluate and configure network layers, such as DNS, routing, or firewall settings, to facilitate a reliable and efficient connection between the host and the container.
4. Implementing Effective Error Handling: Incorporate robust error handling mechanisms that can detect and handle connection errors promptly. Implement processes such as automated error monitoring, logging, and alert systems to ensure timely response and troubleshooting when connection failures occur.
5. Performance Monitoring and Tuning: Monitor the performance of the connection between the host and the Docker container to identify potential bottlenecks or areas for optimization. Utilize performance monitoring tools and techniques to continuously evaluate and fine-tune the connection settings, ensuring optimal data transfer rates and response times.
6. Security Measures: Apply stringent security measures throughout the connection process to safeguard the integrity and confidentiality of the data exchanged between the local database and the container. Utilize encryption techniques, access controls, and data protection practices to mitigate potential security risks and vulnerabilities.
7. Documentation and Test Cases: Maintain comprehensive documentation of the connection setup and configuration, including relevant test cases to validate the connection's stability and reliability. Document all necessary steps and considerations, making it easier for future troubleshooting and replication of the connection setup.
By adopting these best practices, developers can establish a robust and efficient connection between a locally hosted database and a Docker container, ensuring a seamless and reliable interaction between the two environments.
Additional Considerations for Securing and Authenticating the Connection
Ensuring the safety and integrity of the connection
When establishing a connection between a containerized application and a database, it is crucial to prioritize security measures to protect sensitive data and prevent unauthorized access. While connecting securely is important, it is also necessary to implement proper authentication mechanisms to ensure only authorized users can access the database.
Implementing secure communication
To secure the communication between the container and the database, consider utilizing encryption techniques such as SSL/TLS protocols. This ensures that data transmissions are protected from interception and tampering, safeguarding sensitive information from unauthorized access.
Securing container capabilities and network access
Additionally, it is essential to review and limit the container's capabilities and network access rights. By configuring strict access controls and applying the principle of least privilege, you can reduce the attack surface and minimize potential vulnerabilities that can be exploited by malicious actors.
Implementing strong authentication mechanisms
A robust authentication mechanism is crucial to prevent unauthorized users from accessing the database. This can be achieved through various methods, such as using strong passwords, implementing multi-factor authentication, or integrating with an external authentication provider. By utilizing these strategies, you can enhance the overall security of the connection and ensure that only authorized individuals can access the database.
Regularly updating and patching
Continuously monitor for security updates and patches for both the containerized application and the underlying infrastructure. By staying up-to-date with the latest security patches, you can address known vulnerabilities and protect against potential exploits that could compromise the connection.
Monitoring and logging
Implementing robust monitoring and logging practices can help identify any unauthorized access attempts or suspicious activities. By thoroughly reviewing logs and implementing real-time alerting mechanisms, you can promptly respond to any security incidents and take appropriate actions to mitigate potential risks.
Training and educating users
Lastly, it is crucial to provide proper training and education to all users involved in the connection process. Educating users on best security practices, such as the importance of strong passwords, the risks of sharing credentials, and the need to promptly report any suspicious activities, can significantly enhance the overall security posture.
Running SQL Server in Linux Containers
Running SQL Server in Linux Containers by Amazon Web Services 1,905 views 5 years ago 14 minutes, 3 seconds
FAQ
What is a Docker Linux container?
A Docker Linux container is a lightweight, isolated environment that runs applications and their dependencies on a Linux operating system. It allows for easy deployment of applications with consistent behavior across different systems.
Why would I want to connect to a local SQL Server from a Docker container?
There are several reasons why you may want to connect to a local SQL Server from a Docker container. One common scenario is when you have an application running inside a container that needs to interact with a SQL Server database running on the host machine. By establishing a connection, the application can read and write data to the database.
How do I connect to a local SQL Server from a Docker Linux container?
To connect to a local SQL Server from a Docker Linux container, you need to ensure that the container can access the host machine's network. One way to achieve this is by using the `--network=host` flag when running the container. This allows the container to use the host's network stack and makes the SQL Server accessible through the host's IP address. Once the container is connected to the host's network, you can use the appropriate connection string in your application to establish a connection to the SQL Server.




