In an ever-evolving digital landscape, seamless integration between disparate systems is a cornerstone of efficiency. Within the realm of Linux-based Docker containers, versatile connectivity to remote drives becomes an essential requirement for enterprises.
By bridging the gap between Linux and Windows environments, organizations can synergize their operations and harness the power of cross-platform collaboration. However, connecting Windows network drives within Docker containers on Linux distributions presents unique challenges that necessitate innovative solutions.
Within this article, we delve into the intricacies of establishing a robust connection between remote storage on Windows-based networks and Docker containers running on Linux operating systems. Through a comprehensive exploration of alternative terminologies, we shall navigate the intricacies of this process, providing you with valuable insights and step-by-step instructions.
Understanding the Basics of File Sharing on Microsoft Operating Systems
In this section, we will explore the fundamental concepts and principles of file sharing on Microsoft operating systems.
- Introduction to file sharing
- Working with shared folders
- Permissions and access control
- Mapping network drives
- Accessing shared files remotely
- Securing shared resources
File sharing is an essential feature of Microsoft operating systems, enabling users to collaborate and access shared resources across a network. By understanding the basics of file sharing, individuals can effectively manage and control access to shared files and folders, optimizing productivity and enhancing data security.
This section will begin by introducing the concept of file sharing and discussing the benefits it offers to individuals and organizations. It will then delve into the process of creating and managing shared folders, including the various options for setting permissions and controlling who has access to shared resources.
One of the key components of file sharing is mapping network drives, which allows users to assign a drive letter to a shared folder or network location. The section will cover the steps involved in mapping a network drive and explain the advantages it offers in terms of accessing shared files and folders more conveniently.
Additionally, the section will explore the methods for accessing shared files remotely, highlighting the importance of secure remote access protocols and authentication mechanisms to safeguard sensitive information.
Finally, the section will touch upon the topic of securing shared resources, providing insights into best practices for protecting shared files and folders from unauthorized access or potential security breaches.
By grasping the fundamentals of file sharing on Microsoft operating systems, individuals can gain the knowledge and skills necessary to effectively utilize and manage shared resources, enhancing collaboration and ensuring the integrity and security of shared files and folders.
Exploring the Advantages of Implementing Docker Containers
In this section, we will delve into the various benefits and advantages that arise from integrating Docker containers into your development and deployment workflows. By leveraging the power of containerization technology, organizations can achieve enhanced scalability, flexibility, portability, and security for their applications.
- Scalability: Docker containers enable easy and efficient scaling of application components, allowing organizations to handle increased user loads and traffic without compromising performance.
- Flexibility: Containers provide a modular approach to application development, allowing developers to package all the required dependencies and configurations into a single, self-contained unit. This not only facilitates easier development and testing but also simplifies the deployment process across different environments.
- Portability: With Docker containers, applications and their dependencies are encapsulated into a single entity that can be run on any system or platform that supports Docker. This ensures consistent behavior and eliminates compatibility issues, making the application portable across different environments.
- Security: Docker containers employ various isolation mechanisms to separate application components from each other and the host system. This isolation helps prevent the spread of vulnerabilities and enhances overall application security.
- Resource Efficiency: Containers offer efficient resource utilization by sharing the host system's kernel and other resources. This leads to reduced overheads and allows organizations to maximize resource utilization and minimize costs.
- Rapid Deployment: Docker containers enable faster and streamlined deployment processes by providing consistent and reproducible environments. This helps minimize downtime and ensures consistent application behavior throughout the deployment pipeline.
By embracing Docker containers, organizations can leverage these advantages to enhance their development and deployment workflows, ultimately leading to improved productivity, flexibility, and scalability.
Approaches for Establishing Connectivity between Windows File Share and Linux Docker Environment
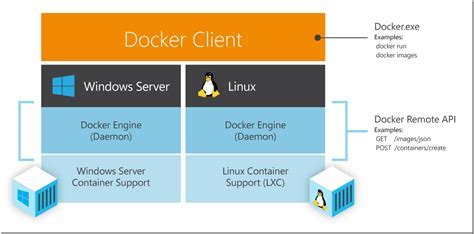
In this section, we will explore various methods that can be employed to establish a connection between a Windows file share and a Linux Docker environment. By leveraging these approaches, users can seamlessly access and utilize files and resources residing in a Windows network drive within their Docker containers, facilitating efficient collaboration and integration workflow.
1. Samba Client
The Samba client provides a reliable and efficient method to connect a Linux Docker container with a Windows network drive by implementing the SMB/CIFS protocol. By configuring the Samba client within the Docker container, users can mount the Windows network drive as a network file system, allowing seamless file access and manipulation.
Example: Setting up the Samba client within the Docker container and configuring it to access the Windows network drive using the appropriate credentials and file path.
2. NFS (Network File System)
Another approach to connect a Windows network drive with a Linux Docker container is by utilizing NFS. By setting up an NFS server on the Windows machine and configuring the Docker container as an NFS client, users can establish connectivity and gain access to the shared network drive. This method ensures efficient and high-performance file access.
Example: Configuring the Windows NFS server to share the designated network drive and configuring the Docker container to mount the NFS share as a file system.
3. SSHFS (SSH File System)
SSHFS offers a secure and convenient method to establish connectivity between a Windows network drive and a Linux Docker container. By utilizing SSHFS, users can mount the Windows network drive as a file system within the Docker container, providing secure file access and seamless integration.
Example: Configuring the SSHFS method to establish a secure connection between the Windows network drive and the Docker container, ensuring encrypted file transfer and secure remote access.
By employing these techniques, users can establish connectivity between a Windows network drive and a Linux Docker environment, enabling efficient collaboration and the utilization of shared resources within the Docker container. It is important to consider the specific requirements and security considerations while implementing these methods.
Mounting CIFS (SMB) Share to Access Files within a Linux-based Environment
In this section, we will explore a method to establish a connection between a Linux-based system and a shared network drive, utilizing the Common Internet File System (CIFS) protocol, also known as SMB (Server Message Block).
When encountering the need to access files stored on a Windows network drive within a Linux environment, establishing a CIFS mount presents a reliable solution. By configuring the mounting process, Linux users can seamlessly navigate and interact with files stored on these network drives as if they were part of the local file system on their Linux machine.
Prerequisites
In order to proceed with this method, it is essential to have a Linux-based system up and running, alongside administrative access or superuser privileges. Additionally, the remote Windows network drive should be accessible and the necessary credentials for authentication must be available.
Configuring CIFS Mount
Before initiating the CIFS mount process, several preparatory steps need to be undertaken. These include installing the required CIFS utility package on the Linux system, specifying the mount point (local directory where the network drive will be attached), and ensuring the necessary authentication details are at hand.
Note: The following instructions may vary slightly depending on the specific Linux distribution being used.
1. Install the CIFS utilities package:
sudo apt-get install cifs-utils
2. Create a directory to serve as the mount point:
sudo mkdir /mnt/network-drive
3. Configure the mount by modifying the /etc/fstab file:
sudo nano /etc/fstab
4. Within the /etc/fstab file, add the following line to mount the network drive:
//server/share /mnt/network-drive cifs username=your_username,password=your_password 0 0
5. Save and exit the file (in nano, press Ctrl + O to save and Ctrl + X to exit).
6. Test the mount by running:
sudo mount -a
Upon successful execution of these instructions, the Windows network drive will be mounted and accessible within the specified mount point on the Linux system. This enables users to interact with the network drive and its files as if they were present on the local machine.
Method 2: Setting up NFS Mounts to Access Windows File Shares
In this section, we will explore an alternative method to connect and access Windows file shares within a Docker container running on a Linux host. Instead of using traditional network drive connections, we will configure NFS mounts to establish a reliable and efficient connection between the host and the container.
- Step 1: Install the necessary NFS packages
- Step 2: Configure the NFS server on the Windows machine
- Step 3: Export the desired Windows file shares to be accessed
- Step 4: Configure the NFS client on the Linux host
- Step 5: Mount the Windows file shares within the Docker container
- Step 6: Verify the successful connection and accessibility of the shared files
By following these steps, you can seamlessly integrate Windows file shares into your Docker container environment, enabling efficient collaboration and data sharing across platforms. The use of NFS mounts provides a robust and scalable solution for accessing Windows network drives within a Linux-based Docker environment.
Method 3: Leveraging External Volumes for Persistent Connections
In this section, we will explore an alternative approach to establishing persistent connections for data storage in a Linux environment within a Docker container. By utilizing external volumes, we can create a reliable and scalable solution for maintaining access to network storage drives.
| Advantages | Disadvantages |
|---|---|
| Seamless integration with the host operating system | Requires additional configuration and setup |
| Efficient and reliable storage management | Potential security risks if proper access controls are not in place |
| Ability to mount multiple external volumes | Dependency on the availability of the external network storage |
To utilize external volumes for persistent connections, we need to follow a series of steps. First, we must configure a suitable external volume source. This can be a network storage device or a remote server that provides access to the desired shared drives.
Once the external volume source is set up, we can proceed with creating and configuring Docker volumes. These volumes act as mount points for the external storage, allowing our containers to access and utilize the shared drives seamlessly.
An important aspect of utilizing external volumes is ensuring proper access control and security measures are in place. This involves implementing authentication mechanisms, setting up appropriate permissions, and regularly monitoring and managing access to the shared drives.
By adopting the approach of leveraging external volumes, we can establish persistent connections to network storage drives within Docker containers running on a Linux environment. This method offers a flexible and scalable solution for managing data storage, enabling efficient collaboration and data sharing within containerized applications.
Best Practices and Considerations for Incorporating Network Storage into Containerized Environments
In containerized environments, the integration of network storage solutions plays a crucial role in ensuring efficient and secure data access. This section will delve into various best practices and considerations for seamlessly connecting and utilizing network storage resources within Docker containers.
| 1. | Optimal Utilization of Shared File Systems |
| 2. | Understanding the Importance of Mounting Options |
| 3. | Ensuring Security and Access Controls |
| 4. | Performance Optimization Techniques |
| 5. | Monitoring and Management of Network Storage |
1. Optimal Utilization of Shared File Systems
Efficient usage of shared file systems is a critical aspect when incorporating network storage into container environments. This section explores strategies for effectively managing shared file systems, including considerations for choosing the appropriate file system type, understanding permissions and file ownership, and ensuring compatibility across different operating systems.
2. Understanding the Importance of Mounting Options
Proper configuration of mounting options is vital in establishing reliable and resilient connections between Docker containers and network storage systems. This section discusses different mounting options available and highlights their impact on performance, fault tolerance, and data integrity.
3. Ensuring Security and Access Controls
Security is of utmost importance when integrating network storage into containerized setups. This section examines best practices for securing network storage connections, employing access controls, implementing encryption, and safeguarding data from unauthorized access or tampering.
4. Performance Optimization Techniques
To achieve optimal performance while utilizing network storage in Docker containers, it is crucial to consider various performance optimization techniques. This section explores strategies such as caching, network bandwidth management, and container resource allocation to ensure efficient data retrieval and transmission.
5. Monitoring and Management of Network Storage
Effectively monitoring and managing network storage resources is essential for maintaining the overall health and performance of Docker containers. This section discusses tools and techniques for monitoring storage metrics, diagnosing issues, and implementing appropriate management practices to ensure seamless operation within the containerized environment.
Ensuring Security and Authentication
Securing access and authenticating users are crucial aspects of connecting a Windows network drive in a Docker container running on Linux. This section explores various strategies to ensure the security and authentication of the network drive connection.
- Implementing robust authentication mechanisms: It is essential to establish secure authentication protocols to verify the identity of users accessing the network drive. This can include methods such as single sign-on (SSO), two-factor authentication (2FA), or certificate-based authentication.
- Encrypting data transmission: To protect sensitive data while it is being transmitted between the Docker container and the Windows network drive, encryption techniques should be employed. This ensures that any intercepted data remains unreadable and secure.
- Controlling access permissions: Assigning appropriate access permissions to users and groups is crucial in maintaining the security of the network drive. Implementing strict access controls, such as role-based access control (RBAC) or access control lists (ACLs), helps prevent unauthorized access and reduces the risk of data breaches.
- Regularly updating security patches: Keeping the Docker container, Linux operating system, and any associated software up to date with the latest security patches is essential to address any vulnerabilities or weaknesses that could be exploited by malicious actors.
- Monitoring and auditing: Implementing robust monitoring and auditing processes allows for real-time detection of any unauthorized access attempts or suspicious activities. Logging and analyzing network drive-related events provide valuable insights that help identify potential security incidents and enable quick responses.
By incorporating these security measures and authentication strategies, organizations can confidently connect Windows network drives in Docker containers on Linux while ensuring the integrity, confidentiality, and availability of their data.
Enhancing Performance and Reliability

In the context of integrating a Linux environment with Windows network resources, ensuring optimal performance and reliability is crucial for seamless and efficient operations. This section explores strategies to enhance the overall performance and reliability of the integration process.
Improving Performance:
Efficient utilization of resources plays a pivotal role in achieving optimal performance. To enhance performance, it is essential to employ techniques such as optimizing network connectivity, reducing latency, and maximizing throughput. By implementing these strategies, system administrators can minimize data transfer delays, improve response times, and ensure smooth and expedient access to network resources.
Additionally, it is imperative to leverage caching mechanisms to mitigate frequent retrieval of data from network drives, resulting in enhanced performance. Caching can reduce the reliance on network communication and facilitate quicker access to frequently accessed files, thereby boosting overall system efficiency.
Ensuring Reliability:
Reliability is paramount when integrating a Linux environment with Windows network drives. One of the crucial factors influencing reliability is robust error handling. Implementing effective error handling mechanisms enables the detection and resolution of any potential disruptions, minimizing system downtime and ensuring uninterrupted access to network resources.
Moreover, incorporating redundant systems and backups for critical data can significantly enhance reliability. This proactive approach protects against unforeseen failures and offers the ability to promptly recover data in case of any disruption.
Employing a comprehensive approach that focuses on optimizing performance and ensuring reliability is vital for a seamless integration between Linux and Windows network resources. By implementing strategies that enhance performance and adopting measures that boost reliability, organizations can achieve smooth and efficient operations, empowering the collaboration between different environments.
Access Folders/Hard Drives Over WiFi (Samba + Docker)
Access Folders/Hard Drives Over WiFi (Samba + Docker) by Madhu 10,317 views 1 year ago 16 minutes
Docker Complete Setup on Windows (With WSL Ubuntu)
Docker Complete Setup on Windows (With WSL Ubuntu) by The Codeholic 232,852 views 2 years ago 11 minutes, 58 seconds
FAQ
How can I connect a Windows network drive in a Linux Docker container?
To connect a Windows network drive in a Linux Docker container, you can use the `cifs-utils` package and mount the network drive using the `mount` command. First, you need to install `cifs-utils` in your Docker container by including it in your Dockerfile or by running the command `apt-get install cifs-utils`. Once installed, you can create a mount point in the container, then use the `mount` command with the correct syntax to mount the Windows network drive.
What is the syntax for mounting a Windows network drive in a Linux Docker container?
The syntax for mounting a Windows network drive in a Linux Docker container using the `mount` command is `mount -t cifs /// -o username= ,password= `. You need to replace ` ` with the IP address or hostname of the Windows drive, ` ` with the name of the shared folder, ` ` with the local directory where you want to mount the drive in the container, ` ` with your Windows username, and ` ` with your Windows password.
Is it possible to automate the process of connecting a Windows network drive in a Linux Docker container?
Yes, it is possible to automate the process of connecting a Windows network drive in a Linux Docker container. You can create a script that includes the necessary `mount` command with the correct syntax to mount the drive, and then run this script when starting the Docker container. Additionally, you can also include the installation of `cifs-utils` in your Dockerfile so that the package is automatically installed when building the container. By automating the process, you can easily connect the Windows network drive without manually executing the commands each time.




