Authenticating users and ensuring the security of their sensitive data is a critical aspect of any modern IT infrastructure. One powerful and widely used solution for user authentication is the Remote Authentication Dial-In User Service (RADIUS). In this comprehensive guide, we will explore the step-by-step process of configuring RADIUS authentication on a Linux server, providing you with the knowledge and skills to implement robust user authentication in your environment.
Throughout this guide, we will delve into the intricacies of RADIUS configuration, covering everything from the basic concepts to advanced settings. You will learn how to establish a secure connection between your Linux server and the RADIUS server, ensuring encrypted communications and protecting sensitive user credentials.
By following the step-by-step instructions provided in this guide, you will gain a deep understanding of the inner workings of RADIUS. We will walk you through the necessary configurations, the installation of required packages, and the creation of key files. Moreover, we will discuss best practices and potential pitfalls, enabling you to troubleshoot issues and optimize the performance of your RADIUS setup.
Whether you are a seasoned Linux administrator or a beginner exploring the world of network security, this guide will equip you with the knowledge and skills to successfully configure RADIUS authentication on your Linux system. By utilizing the flexibility and power of RADIUS, you can provide a seamless and secure authentication experience for both your internal users and external entities accessing your network.
Understanding the Significance of RADIUS in Network Authentication
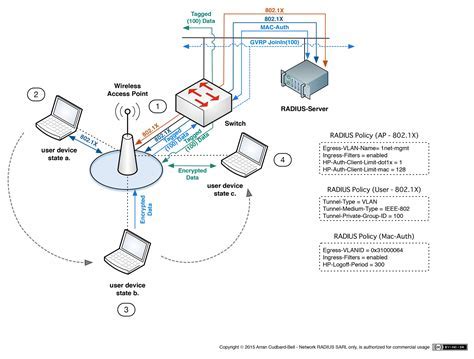
In the realm of network security and user authentication, there exists a vital protocol known as RADIUS, which plays a pivotal role in determining the integrity and confidentiality of network access. This article aims to shed light on the concept and importance of RADIUS, without delving into the specifics of configuring it on a Linux system. Let's explore why RADIUS is a crucial element in the world of network authentication.
Firstly, RADIUS stands for Remote Authentication Dial-In User Service, essentially acting as a centralized authentication and authorization mechanism for network services. It enables secure communication between user devices and network access servers, validating the identity of users seeking network access and allowing them to connect only after successful authentication.
One of the primary merits of RADIUS is its ability to authenticate users across a diverse range of network devices and platforms, thus providing a unified authentication experience. It acts as a middleman between the user and the network access server, ensuring that user credentials are securely transmitted and verified before allowing access to network resources.
Furthermore, RADIUS enhances network security by supporting a variety of authentication methods such as Password Authentication Protocol (PAP), Challenge Handshake Authentication Protocol (CHAP), and even more robust protocols like Extensible Authentication Protocol (EAP). This versatility allows organizations to choose the most appropriate authentication method, based on their security requirements.
Another significant advantage of RADIUS is its ability to centralize user management. With the authentication and authorization processes controlled by a single RADIUS server, network administrators can efficiently manage user accounts, assign access rights, and enforce security policies from a central location. This not only simplifies the management process but also ensures consistency and reduces the risk of unauthorized access.
In conclusion, RADIUS serves as a critical tool in network authentication, providing a secure, scalable, and centralized approach to verifying user identities. Its flexibility, compatibility, and ability to centralize user management make it an indispensable component in ensuring network security and maintaining the integrity of network resources.
Prerequisites
In order to successfully configure the Radius authentication protocol on your Linux system, there are certain requirements that need to be fulfilled. These prerequisites ensure that you have the necessary components and knowledge to carry out the configuration process smoothly.
1. Linux Operating System: You must have a Linux operating system installed on your machine. It is recommended to have a recent version of a popular distribution such as Ubuntu, CentOS, or Debian.
2. Basic Linux Knowledge: Familiarity with basic Linux command line operations and administrative tasks will greatly assist you in configuring Radius on your system. Understanding concepts like user management, file permissions, and networking is crucial.
3. Access to Terminal: You should have access to a terminal or command line interface on your Linux system. This can be achieved either by physically being in front of the machine or by using remote access methods such as SSH.
4. Radius Server Software: Before you can start configuring Radius on your Linux system, you need to have a Radius server software installed. There are various options available, including FreeRADIUS, Radiator, and Microsoft Network Policy Server (NPS).
5. Network Connectivity: A stable network connection is essential for the successful operation of the Radius server. Ensure that your Linux system is connected to the network, either through a wired or wireless connection. Additionally, make sure you have the necessary network configurations, such as IP address and subnet mask, correctly set up.
6. User Account with Administrative Privileges: To configure Radius on your Linux system, you will need administrative privileges. Ensure that you have a user account with sufficient rights to perform system configuration tasks. This will enable you to make the necessary changes and modifications to the system files and settings.
By meeting these prerequisites, you will be well-prepared to move forward with the configuration of Radius on your Linux system. Having a solid foundation and understanding of these requirements will assist you in successfully implementing the necessary steps.
Operating System Compatibility for Radius Configuration
In the realm of configuring a Remote Authentication Dial-In User Service (RADIUS) on a Linux-based system, it is essential to understand the operating system compatibility requirements. This section focuses on exploring the diverse range of operating systems that can seamlessly integrate and support RADIUS configuration, enabling efficient user authentication and authorization processes.
When delving into the world of RADIUS configuration, it is vital to recognize that different operating systems may vary in their support for RADIUS protocols and functionalities. While Linux systems are often preferred due to their flexibility and open-source nature, other operating systems can also play a significant role in facilitating a reliable and secure RADIUS infrastructure.
One notable operating system renowned for its compatibility with RADIUS configuration is Microsoft Windows Server. With built-in support for RADIUS protocols, this widely-used OS offers a straightforward approach for integrating RADIUS services into existing networks, effectively managing user authentication across various devices and platforms.
Another prominent player in the realm of RADIUS configuration compatibility is macOS. Leveraging its robust network security capabilities, macOS provides a robust foundation for deploying RADIUS services, catering to the authentication needs of Mac devices and ensuring seamless integration with other operating systems.
It is worth mentioning that RADIUS compatibility extends beyond popular operating systems like Linux, Windows, and macOS. Various other Unix-based systems, such as FreeBSD and OpenBSD, are also proficient in supporting RADIUS configuration, bolstering network security while ensuring smooth user authentication experiences.
In conclusion, while this article primarily focuses on configuring RADIUS on a Linux system, it is crucial to acknowledge the diverse range of operating systems that can effectively support RADIUS configuration. Whether utilizing Windows, macOS, or other Unix-based systems, understanding operating system compatibility is pivotal in designing a robust and streamlined RADIUS infrastructure.
Installation
In this section, we will focus on the initial setup required to install and configure the Radius server on a Linux-based system. We will walk you through the necessary steps to seamlessly set up the server without any hurdles.
Firstly, you need to prepare your Linux system for the installation. This involves ensuring that all the required packages and dependencies are present. By following the guidelines provided, you will be able to effortlessly install the necessary components.
Next, we will guide you through the installation process itself. This step involves downloading and extracting the Radius server software onto your system, creating necessary directories and files, and setting appropriate permissions. We will specify the essential commands and procedures to follow for a successful installation.
Once the installation is complete, we will help you verify the installation by checking the version and confirming that all the necessary files were correctly installed. This step is crucial to ensure that the Radius server is functioning properly.
In conclusion, this section will provide you with a comprehensive understanding of the installation process of a Radius server on your Linux system. Following our step-by-step instructions, you will be able to install the necessary software components and successfully set up the server.
Installation Procedure for Radius on a Linux Operating Environment
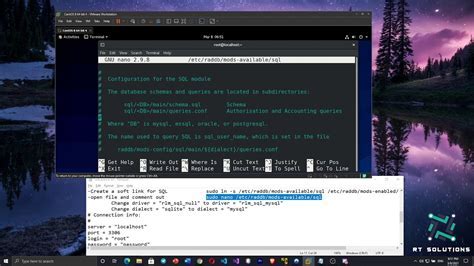
In this section, we will walk you through a step-by-step process for setting up and installing Radius on a Linux-based system. The installation of Radius will enable you to successfully manage and authenticate network access for users.
To get started, ensure that you have root access to your Linux system, as this will be necessary to install the required packages and configure the necessary settings.
| Step | Description |
|---|---|
| 1 | Update the package manager by running the command 'sudo apt update' in the terminal. |
| 2 | Install the necessary packages by running the command 'sudo apt install freeradius' in the terminal. |
| 3 | Configure the Radius server by editing the '/etc/freeradius/radiusd.conf' file and setting up the necessary parameters. |
| 4 | Configure the clients by editing the '/etc/freeradius/clients.conf' file and adding the IP addresses or hostnames of the clients that will be accessing the Radius server. |
| 5 | Configure the users by editing the '/etc/freeradius/users' file and adding the user credentials and attributes for authentication. |
| 6 | Restart the Radius service by running the command 'sudo systemctl restart freeradius' in the terminal. |
| 7 | Test the Radius setup by using a client device to connect to the network and verifying successful authentication and access. |
| 8 | Further customization and configuration options for Radius can be explored by referring to the official documentation and community forums. |
By following these step-by-step instructions, you will be able to install Radius on your Linux system and have it fully functional for managing network access and authentication. Remember to perform regular maintenance and security updates to ensure the smooth operation of your Radius server.
Configuration
In this section, we will explore the process of setting up and customizing the parameters for the Radius authentication protocol on a Linux-based system. This entails adjusting various settings and options to ensure optimal performance and security.
Firstly, it is important to understand the significance of fine-tuning the configuration of the Radius server. By tailoring the settings to the specific requirements and characteristics of your network environment, you can enhance the overall reliability and efficiency of authentication processes.
During the configuration process, several key aspects need attention. This includes the establishment of secure communication channels, defining user access policies and privileges, implementing encryption mechanisms, and setting up logging and auditing procedures. Each of these components plays a vital role in establishing a robust and secure authentication framework.
Additionally, the configuration process involves configuring various network devices and servers to integrate effectively with the Radius server. This ensures seamless authentication and authorization for users across the network, regardless of their physical location.
To aid you in the configuration process, we will provide step-by-step instructions, accompanied by explanations and examples. These instructions will guide you through the necessary configuration files and commands, enabling you to customize the Radius protocol according to your specific network requirements.
Remember, the configuration process is a critical step in the implementation of Radius on your Linux system. By carefully tuning the parameters and customizing the settings, you can establish a reliable, secure, and efficient authentication infrastructure that meets the unique needs of your network environment.
Setting up the RADIUS Server: Simplifying Network Authentication and Authorization
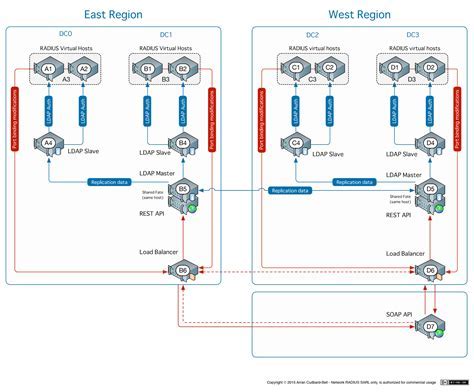
In this section, we will explore the process of configuring a RADIUS server on a Linux-based system, enabling seamless authentication and authorization for network access.
By employing industry-standard protocols and leveraging a centralized authentication mechanism, the RADIUS server facilitates secure access control across networks, reducing the complexity and management overhead associated with individual user credentials for each network device or service.
Throughout this guide, we will delve into the various steps involved in configuring the RADIUS server, covering key aspects such as defining client access policies, configuring user attributes, and implementing encryption for enhanced security.
By the end of this section, you will have a comprehensive understanding of the necessary configurations required to establish a robust RADIUS server on your Linux system, effectively streamlining network authentication and authorization processes.
Let's dive in and explore the step-by-step instructions to configure your RADIUS server, ensuring a seamless network experience for your users!
Configuring Clients for Radius Authentication
In this section, we will explore the process of setting up clients to enable radius authentication on your Linux system. Here, we will delve into the steps required to configure radius authentication for your network devices or applications, allowing them to communicate securely with the central authentication server.
Our focus lies on the configuration aspect, where we will guide you through the necessary settings and parameters to ensure a smooth radius authentication setup. By properly configuring the clients, you can enhance the security and control over user access to your network or system.
We will walk you through the process of defining the necessary client information, such as the shared secret, IP address, and client name. This information will be crucial for the proper establishment of the communication between the client and the radius server. Additionally, we will discuss the importance of securing the shared secret and the significance of selecting strong and unique values.
Furthermore, we will explore the various protocols and ports that need to be enabled on the client's side for successful radius authentication. Understanding which protocols are required and how to configure them correctly will ensure a seamless authentication process and minimize potential security vulnerabilities.
Lastly, we will provide you with troubleshooting tips and common problems that may arise during the client configuration process. By addressing these issues proactively, you can swiftly resolve any complications and ensure a reliable radius authentication for your Linux system.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
What is Radius and why is it important for a Linux system?
Radius stands for Remote Authentication Dial-In User Service. It is a networking protocol that provides centralized authentication, authorization, and accounting for users who connect and use a network service. It is important for a Linux system as it allows for secure access control and management, ensuring that only authorized users can connect to the network.
What are the steps involved in configuring Radius on a Linux system?
The steps involved in configuring Radius on a Linux system include installing the necessary packages, configuring the Radius server, setting up the client, and testing the configuration. Detailed instructions can be found in the "Configuring Radius on a Linux System: Step-by-Step Guide" article.
Can Radius be used for wireless network authentication on a Linux system?
Yes, Radius can be used for wireless network authentication on a Linux system. By configuring a Radius server and setting up the wireless access point as a client, users can authenticate themselves and gain access to the wireless network using their credentials.
What are some common issues that may arise when configuring Radius on a Linux system?
Some common issues that may arise when configuring Radius on a Linux system include incorrect configuration settings, firewall blocking Radius traffic, issues with certificates or encryption, and compatibility issues between the Radius server and client. Troubleshooting these issues may require checking configuration files, ensuring proper network connectivity, and reviewing system logs for error messages.
Is it possible to integrate Radius authentication with other systems on a Linux system?
Yes, it is possible to integrate Radius authentication with other systems on a Linux system. Radius supports various authentication methods, such as PAM (Pluggable Authentication Module), which allows it to integrate with various services like SSH, FTP, and VPN. This provides a unified authentication system for the Linux system.
What is Radius?
Radius, which stands for Remote Authentication Dial-In User Service, is a networking protocol that provides centralized authentication, authorization, and accounting management for users attempting to access a network service.




