Exploring the intricate depths of a computer's underlying architecture, we embark on a journey to decode the hidden secrets of optimizing security measures. Today, our focus lies on unlocking the potential of the Pluggable Authentication Modules (PAM) framework. This powerful tool acts as the gatekeeper to your Linux environment, safeguarding access and reinforcing protective barriers.
As we navigate this expansive landscape, we delve into the art of fine-tuning authentication mechanisms without compromising the seamless user experience. By familiarizing ourselves with PAM's inner workings, we unearth a myriad of possibilities to heighten system security, utilizing a wide array of strategies to fortify your digital fortress.
Within these realms, the power of flexibility reigns supreme. Harnessing the versatility of PAM, you gain unparalleled control over authentication methods, enabling seamless integration with numerous applications and services. Unleash the full potential of your Linux ecosystem by mastering the intricate art of PAM configuration, bolstering your defenses against unauthorized attempts and ensuring the utmost protection for your sensitive data.
Understanding the Significance of PAM in Enhancing Security for Linux Environments
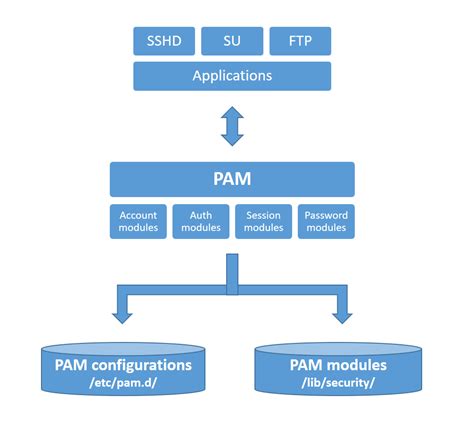
In the realm of Linux security, one essential component that plays a vital role in safeguarding the system is the Pluggable Authentication Modules (PAM). These modules function as a flexible framework, ensuring reliable authentication methods and access control mechanisms for various Linux applications.
At its core, PAM serves as the gateway to user authentication, managing the process of verifying users' identities and granting or denying access to the system. This powerful framework enables system administrators to implement multifactor authentication, enforce password policies, and control user privileges efficiently.
- Authenticating Users: PAM allows the utilization of diverse authentication methods, including passwords, tokens, biometrics, and smart cards, to verify users' identities. This flexibility enables organizations to implement the most suitable authentication mechanisms based on their specific security requirements.
- Enforcing Access Controls: With PAM, system administrators can easily define access policies to determine which users or groups are granted access to specific resources or services. By configuring PAM modules and access control rules, organizations can establish granular control over user privileges, enhancing overall system security.
- Facilitating Centralized Authentication: PAM simplifies the process of centralizing authentication mechanisms by allowing the integration of various authentication sources, such as LDAP directories, Active Directory, or radius servers. This consolidation streamlines user management, eliminates duplication of efforts, and enhances administrative efficiency.
- Enhancing Security with Customization: PAM modules provide the flexibility to customize authentication and access control mechanisms. System administrators can implement additional security measures, such as two-factor authentication, account lockouts, or session restrictions, to fortify the overall security posture of the Linux system.
Given its critical role in authentication and access control, understanding the importance of PAM in a Linux environment is vital. By leveraging PAM's capabilities, organizations can strengthen the security of their Linux systems, mitigate risks associated with unauthorized access, and protect sensitive data from potential threats.
Understanding the Architecture and Functionality of PAM
PAM, an acronym for Pluggable Authentication Modules, forms a vital part of the authentication process in Linux-based systems. This article takes a deep dive into the architecture and inner workings of PAM, shedding light on its significance in securing user access and managing authentication mechanisms.
At its core, PAM relies on a modular structure comprised of configurable libraries and plugins that collaborate to authenticate and authorize user access to various resources. By understanding the PAM architecture, administrators gain insight into how different modules interact with each other and the underlying system to grant or deny access to users.
- PAM Modules: PAM modules serve as the building blocks of the PAM framework and are responsible for performing specific authentication tasks. Each module can be configured independently, enabling administrators to design a customized authentication flow.
- Authentication Stack: The PAM framework contains a stack of modules called the authentication stack. This stack defines the order in which the modules are executed during the authentication process. Understanding stack configuration is crucial for designing a robust and secure authentication system.
- PAM Configuration Files: PAM configuration files define how the PAM framework operates. These files specify the PAM modules used for each authentication service and determine the desired behavior when authenticating users.
- PAM Functions: PAM provides a set of functions that developers can use to interact with PAM modules programmatically. These functions allow for dynamic authentication and enable the customization of authentication workflows based on specific needs.
By comprehending the PAM architecture and its underlying concepts, system administrators can effectively configure and manage authentication mechanisms, enhancing the overall security of their Linux systems. With a solid understanding of PAM's functionality, administrators are equipped to make informed decisions regarding authentication, authorization, and access control in diverse environments.
The Role of the PAM Library and Its Modules
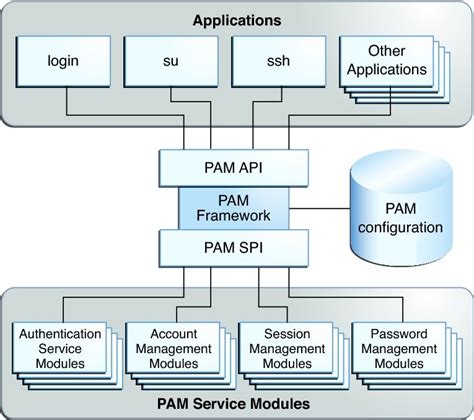
The PAM (Pluggable Authentication Modules) library plays a crucial role in the security infrastructure of a Linux-based operating system. It provides a flexible, modular framework that enables administrators to configure and manage user authentication and authorization processes. PAM supports a wide range of authentication methods, allowing system administrators to implement various security policies tailored to their specific needs.
At the core of the PAM library are its modules, which are small software components that implement specific authentication tasks. These modules can be dynamically loaded and configured to perform different actions during the authentication process. Some common modules include password authentication, account management, session management, and session access control.
Each module in the PAM library has a specific role and set of functions. For example, the password authentication module is responsible for verifying the user's password against the system's password database. On the other hand, the account management module checks if the user's account is valid and current, ensuring that access restrictions or account expiration dates are enforced.
The ability to configure and customize the behavior of PAM modules is what makes the PAM library so powerful. Administrators can define different authentication policies for various system services, allowing for fine-grained control over access to sensitive resources. Using the PAM configuration file, administrators can specify which modules should be used for each authentication phase and define the order in which they are invoked.
Moreover, PAM modules can also be extended or replaced with custom modules, providing system administrators with the flexibility to implement their own authentication mechanisms or integrate with external authentication sources. This modularity makes it possible to adapt the system's authentication capabilities to evolving security requirements and to integrate with various centralized user directories or single sign-on systems.
In summary, the PAM library and its modules are fundamental components in the authentication and authorization process of a Linux system. Their flexibility and extensibility enable system administrators to implement robust security policies tailored to their organization's needs. Understanding the role and capabilities of the PAM library is vital for effectively managing user access control and maintaining the overall security of a Linux system.
The PAM stack and its configuration file
A fundamental aspect of securing a Linux environment involves configuring the Pluggable Authentication Modules (PAM) stack. Understanding the structure and organization of the PAM stack and its associated configuration file is essential for ensuring proper authentication and access control on a Linux system.
The PAM stack consists of a collection of dynamically linked libraries, commonly referred to as PAM modules. These modules allow for the implementation of different authentication mechanisms, such as passwords, tokens, or biometrics, and the enforcement of various access control policies.
The configuration file that governs the behavior of the PAM stack is typically located in the /etc/pam.d/ directory and named after the application or service it is associated with. This file contains a series of directives, each specifying the PAM module to be used and its associated configuration options.
By carefully configuring the PAM stack and its corresponding configuration file, system administrators can control the authentication and authorization processes of the Linux system. They can enforce password complexity requirements, define account lockout policies, enable two-factor authentication, and more.
When configuring the PAM stack, it is important to consider the order in which the PAM modules are listed. This order determines the sequence in which the authentication checks are performed, allowing for flexibility and customization in the authentication process.
The PAM stack and its configuration file serve as a critical component in the overall security posture of a Linux system. Properly understanding and configuring this powerful framework contributes to a robust and secure authentication and access control mechanism.
Exploring PAM Authentication Configuration
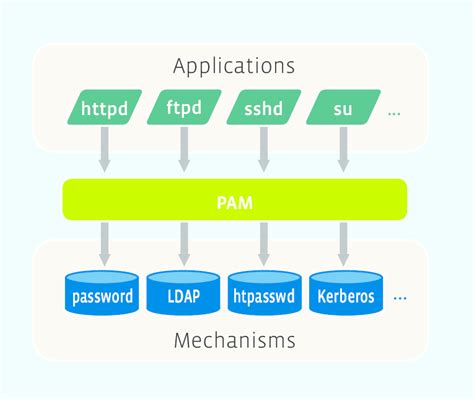
Enhancing security measures and ensuring authorized access to a Linux operating environment are essential for system administrators. The use of Pluggable Authentication Modules (PAM) provides a flexible and customizable framework for authenticating users.
With PAM, administrators can configure a variety of authentication methods, such as passwords, biometrics, or smart cards, to ensure robust access control. This section delves into the process of configuring PAM authentication, enabling system administrators to tailor the authentication process to their specific security requirements.
By understanding the intricacies of PAM configuration, administrators can fine-tune authentication policies, manage user access, and reinforce the overall security posture of the Linux system. Through the careful selection and arrangement of PAM modules, administrators can balance convenience with security, taking into account factors like user roles, hardware requirements, and system policies.
Throughout this section, we will explore various authentication options available within the PAM framework, examining the configuration files and parameters necessary for their implementation. Additionally, we will consider best practices and recommendations for ensuring a reliable and robust authentication process.
By the end of this section, administrators will be equipped with the knowledge and understanding to effectively configure PAM authentication, bolstering system security and mitigating the risk of unauthorized access on a Linux system.
Exploring Various Authentication Modules and Customization Options in PAM
In the realm of Linux system administration, securing user authentication is of utmost importance. The Pluggable Authentication Modules (PAM) framework provides a flexible and customizable approach to authentication on Linux systems. PAM allows system administrators to configure authentication policies by selecting and configuring various authentication modules.
This article delves into the realm of PAM authentication modules and explores their functionality and customization options. It will provide an in-depth understanding of the commonly used authentication modules and how to tailor their options to suit specific security requirements.
- PAM Unix Module: This module authenticates users by checking against local system accounts in the /etc/passwd file. It offers options to enforce password policies, such as password aging and complexity requirements.
- PAM LDAP Module: The LDAP module enables authentication against Lightweight Directory Access Protocol (LDAP) servers. It allows organizations to centralize user account management and facilitates seamless authentication across multiple systems.
- PAM SSSD Module: SSSD (System Security Services Daemon) is a feature-rich authentication framework that integrates with various backends, including LDAP, Active Directory, and Kerberos. We'll explore the SSSD module and the possibilities it offers for secure authentication.
- PAM Two-factor Authentication Module: This module adds an extra layer of security by requiring users to provide a second form of authentication, such as a one-time password or a hardware token, in addition to their regular credentials.
Each authentication module comes with its own set of options that can be customized to meet specific security requirements. This article will discuss the various configuration options available for each module and their impact on user authentication and system security.
By understanding the capabilities and customization options of different PAM authentication modules, system administrators can implement robust and tailored authentication policies that suit their organization's security needs. Through this exploration, you will gain the knowledge and confidence to configure PAM authentication effectively.
Exploring the Realm of Custom PAM Authentication Rules
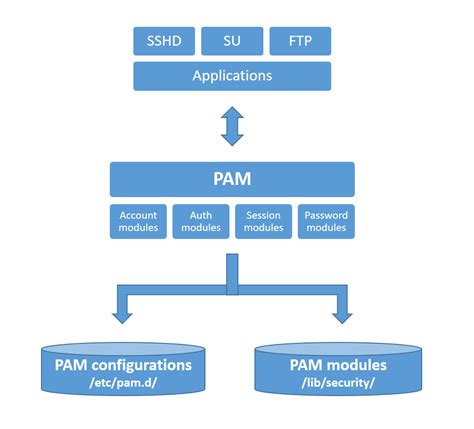
In the realm of securing Linux systems, the creation of custom PAM authentication rules holds immense potential. By venturing into the realms of customization, administrators can tailor authentication processes to align with the unique needs and requirements of their environment while bolstering the overall security posture.
The creation of custom PAM authentication rules involves a meticulous process that requires a deep understanding of the underlying authentication mechanisms and the flexibility that PAM provides. This article aims to shed light on the intricacies of crafting bespoke rules, offering insights into the key concepts, considerations, and steps involved.
| Table of Contents |
|---|
| 1. Unveiling the Foundation: Introduction to PAM |
| 2. The Power of Customization: Benefits of Custom PAM Authentication Rules |
| 3. Navigating the Landscape: Understanding PAM Authentication Modules |
| 4. Crafting Custom Rules: Key Concepts and Considerations |
| 5. Implementation in Action: Step-by-Step Guide to Creating Custom PAM Authentication Rules |
| 6. Ensuring Reliability and Security: Testing and Validating Custom PAM Rules |
| 7. Final Verdict: Weighing the Pros and Cons of Custom PAM Authentication Rules |
By delving into the exploration of custom PAM authentication rules, system administrators can unlock a world of possibilities in terms of fine-tuning authentication workflows, enhancing security, and meeting unique organizational requirements. Through careful consideration of the concepts and steps outlined in this article, one can navigate this journey with confidence and secure their Linux systems effectively.
Enhancing Account Management with PAM Configuration
PAM (Pluggable Authentication Modules) plays a crucial role in providing secure authentication and access control on a Linux-based system. By configuring PAM's account management, administrators can optimize user account handling, enforce password policies, and strengthen system security.
Streamlining User Account Handling: PAM's account management allows administrators to define rules and policies for user accounts. With the help of PAM modules, it is possible to specify criteria like password expiration, account locking, and limited login times. By configuring PAM account management effectively, administrators can ensure that user accounts are handled in a consistent and secure manner.
Enforcing Password Policies: PAM configuration enables the enforcement of strong password policies that protect sensitive user information from unauthorized access. By defining password complexity rules, setting password expiration intervals, and implementing account lockouts after failed login attempts, administrators can minimize the risk of password-based security breaches.
Strengthening System Security: PAM's account management configuration is an essential factor in strengthening the overall security of a Linux system. By combining PAM's account management capabilities with other security measures such as file permissions, network access restrictions, and proper user privilege management, administrators can create a multi-layered defense system that mitigates various security risks.
Configuring PAM account management effectively requires a thorough understanding of the available PAM modules, their configuration options, and the specific security requirements of the Linux system. By implementing a comprehensive and well-designed PAM account management configuration, administrators can significantly enhance the security posture of their Linux-based infrastructures.
Managing user access with PAM account modules
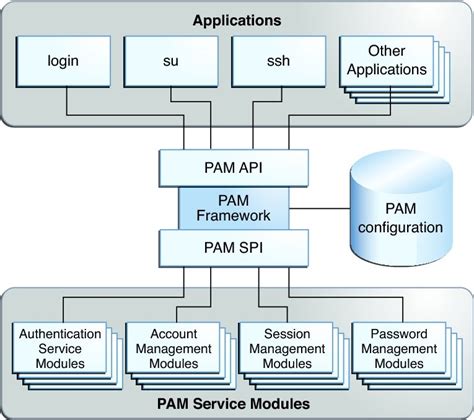
In the realm of configuring access control for users on a Linux-based operating system, the use of PAM account modules plays a crucial role. These modules are responsible for managing user access and permissions, ensuring secure and controlled authentication processes. By understanding and effectively configuring PAM account modules, system administrators can enhance security, control user access, and implement comprehensive access control policies.
With PAM account modules, system administrators gain flexible control over various aspects of user access, including password policies, account expiration, and account locking mechanisms. Through proper configuration, administrators can enforce strong password requirements, implement account expiration policies to ensure periodic security reviews, and prevent unauthorized access by locking user accounts after a specified number of failed login attempts.
Furthermore, PAM account modules allow for integration with external systems and services, enabling administrators to synchronize user access management across multiple platforms. This integration eliminates the need for independent user management on each system, promoting consistency, and streamlining the administrative tasks associated with user access control.
Properly configuring PAM account modules involves understanding and utilizing various directives provided by the PAM framework. These directives enable administrators to define account policies, set up authentication checks, and enforce access control measures. Administrators can configure PAM to perform specific actions based on the account state, such as denying access when an account has expired or prompting users to change their passwords upon login.
Overall, by effectively managing user access with PAM account modules, system administrators can fortify the security of their Linux systems, implement customized access policies, and ensure controlled user authentication across multiple platforms.
Setting Account Restrictions and Policies with PAM
Exploring the configuration options available for managing account restrictions and policies can greatly enhance the security of your Linux-based system. By leveraging the power of Pluggable Authentication Modules (PAM), you can implement various measures to control access, enforce password complexity rules, and set account lockout policies.
Account restrictions and policies play a crucial role in safeguarding your system against unauthorized access and protecting sensitive data. This section will delve into the diverse capabilities of PAM, providing valuable insights into how you can enhance your Linux system's security framework.
From setting password length and complexity requirements to configuring account lockouts after multiple failed login attempts, the range of options offered by PAM is extensive. By understanding the different modules and configuring them effectively, you can establish robust account restrictions and policies tailored to your specific security needs.
Moreover, this section will explore advanced techniques for implementing two-factor authentication using PAM, adding an extra layer of security to your Linux system. By combining something the user knows (like a password) with something the user possesses (like a physical device), you can significantly strengthen the authentication process.
By following the best practices outlined in this section, you can ensure that your Linux system is fortified with the appropriate account restrictions and policies, providing a solid defense against potential security threats and unauthorized access.
FAQ
What is PAM and why is it important to configure it on a Linux system?
PAM stands for Pluggable Authentication Modules. It is a system that provides a flexible and modular approach to authentication on Linux systems. By configuring PAM, you can customize and strengthen the authentication process, ensuring the security and access control of your Linux system.
How can I configure PAM on a Linux system?
To configure PAM on a Linux system, you need to modify the PAM configuration files located in the directory /etc/pam.d/. These files define the behavior and rules for authentication. By editing these files, you can specify which authentication modules to use, set authentication policies, and define the actions to be taken in case of successful or failed authentication attempts.
What are some common authentication modules used in PAM?
There are several common authentication modules used in PAM, including pam_unix (for traditional Unix authentication), pam_ldap (for LDAP authentication), pam_ssh (for SSH authentication), pam_winbind (for Windows domain authentication), and pam_wheel (for granting administrative privileges to specific users). These modules provide different methods and mechanisms for authentication, allowing you to choose the most suitable option for your system.
Can I configure PAM to require additional authentication factors, such as two-factor authentication?
Yes, you can configure PAM to require additional authentication factors, such as two-factor authentication (2FA). PAM supports various authentication methods, including biometric authentication, smart card authentication, and OTP (one-time password) authentication. By configuring the appropriate PAM modules and settings, you can add an extra layer of security to your Linux system.
What are some best practices for configuring PAM on a Linux system?
When configuring PAM on a Linux system, it is recommended to follow some best practices. These include enforcing strong password policies, using multi-factor authentication whenever possible, regularly reviewing and updating the PAM configuration files, monitoring PAM logs for any suspicious activities, and testing the configured PAM settings thoroughly before deploying them in a production environment. Additionally, it is crucial to keep the PAM software and modules up to date to benefit from the latest security enhancements.
What is PAM and why is it important for a Linux system?
PAM stands for Pluggable Authentication Modules and it is an authentication framework used by Linux systems. It allows the system to authenticate users and manage their access. PAM provides a flexible and modular approach to authentication, giving system administrators the ability to configure multiple authentication methods and policies.
How can I configure PAM on my Linux system?
To configure PAM on a Linux system, you need to modify the configuration files located in the /etc/pam.d directory. These files specify the authentication policies for various system services. You can use a text editor to modify the desired file and add, remove, or modify the authentication modules and options. It is important to carefully configure PAM to ensure the desired level of security and usability.




