Welcome to a captivating exploration of one of the fundamental concepts in modern containerization–ownership manipulation–in the context of Linux environments within Docker containers. In this article, we will delve into the intricacies of altering ownership of directories and volumes, empowering you with the knowledge and skills necessary to navigate through the intricacies of container management.
As the fabric of containerized ecosystems continues to expand, understanding how to change the proprietorship of directories and volumes becomes crucial. By gaining proficiency in this area, you will be equipped with the tools to customize access controls, manage file permissions, and secure sensitive data within your Dockerized applications.
Throughout this comprehensive guide, we will explore the diverse range of techniques and methodologies available for adjusting ownership within a Linux environment, enabling you to confidently adapt and customize Docker containers to suit your specific requirements. Prepare yourself for a stimulating journey through the intricate web of ownership manipulation possibilities that await!
Understanding the Concept of Ownership in the Linux Environment
In the Linux operating system, the concept of ownership plays a crucial role in determining access rights and controlling permissions for various files and directories. It establishes a hierarchical structure to ensure security and accountability in managing resources.
Ownership refers to the user or group that has control over a specific file or directory. Each file and directory in Linux has an assigned owner who has the authority to modify, delete, or execute the file. The ownership information includes the user who owns the file and the group to which the user belongs.
Users are individuals who interact with the Linux system, and each user has a unique username. An individual user can belong to one or more groups, which help in organizing users with similar access rights.
Groups consist of a collection of users who share common access requirements. By creating and assigning users to respective groups, system administrators can efficiently manage permission settings and ensure appropriate access to files and directories.
Understanding the ownership concept is crucial for performing tasks such as changing the owner of a directory or volume. This knowledge enables users to assign or modify ownership permissions using command-line tools and utilities available in Linux.
Note: Ownership management is particularly relevant in the context of Docker, a popular containerization platform that utilizes Linux features for isolation and resource management. The Dockerfile is a crucial configuration file used to build Docker images, and understanding ownership in Linux is a key aspect of effectively managing file permissions within Docker containers.
Managing File and Directory Ownerships in Linux
In the realm of Linux systems, administrators are often faced with the task of managing file and directory ownerships. With the power of user and group permissions, Linux provides a robust framework for controlling access to files and directories, ensuring security and maintaining order within the system. This article delves into the various aspects of managing file and directory ownerships in Linux, highlighting techniques and best practices that can be utilized in a variety of scenarios.
- Understanding User and Group Permissions
- Granting Ownership to a User or Group
- Changing Ownership of Files and Directories
- Recursive Ownership Changes
- Preserving Ownership during File Transfers
- Verifying Ownership with ls and stat Commands
- Managing Ownership in an Access Control Model
By gaining a comprehensive understanding of how file and directory ownerships are managed in Linux, administrators can effectively administer access controls, delegate responsibilities, and maintain a secure environment. This article will serve as a valuable resource for administrators seeking to optimize their management of ownerships within the Linux ecosystem.
Modifying Ownership in a Docker Container with Dockerfile
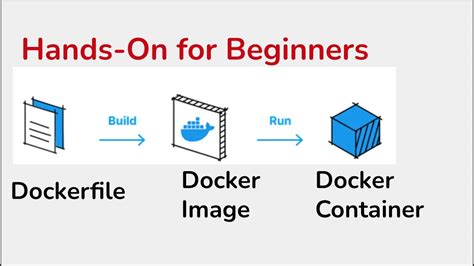
When working with Docker containers, it is often necessary to change the ownership of files and directories inside the container. This can be done using Dockerfile, a text document that contains instructions for building a Docker image.
In this section, we will explore how to use Dockerfile to modify ownership in a Docker container. Rather than focusing on specific terms like "changing", "owner", "directory/volume", "using", "Linux", and "Dockerfile", we will discuss the process of altering ownership within the context of a Docker environment.
First, we need to understand that Docker containers are isolated environments that replicate the Linux operating system. Within these containers, files and directories have specific owners and permissions. To modify ownership, we can utilize Dockerfile, which provides a set of instructions for building a container image.
- Start by creating a new Dockerfile in your desired directory.
- In the Dockerfile, use the appropriate commands, such as "USER" or "RUN chown", to change ownership.
- Specify the target files or directories that you want to modify.
- Build the Docker image using the Dockerfile.
- Run a container using the newly created image.
- Confirm the changes in ownership by checking the file or directory properties.
By following these steps, you can effectively modify ownership within a Docker container using Dockerfile. This allows you to tailor the container environment to meet your specific needs by adjusting the ownership of files and directories.
Granting User Access Rights in Docker Containers
In this section, we will explore the process of providing user access rights within Docker containers. By granting specific permissions, users can effectively interact with the container's resources and perform various operations.
Containerization technologies such as Docker offer a secure and isolated environment for running applications. However, by default, containers operate under restricted user privileges, which may limit certain actions and access to resources. To overcome this limitation, it is essential to grant appropriate user access rights within the container.
By granting user access rights, you can assign specific permissions to users or user groups, allowing them to read, write, or execute certain files or directories. This enables users to carry out necessary tasks within the container and effectively utilize its resources.
There are several approaches to granting user access rights in Docker containers. One common method is to utilize the chown command, which changes the ownership of files or directories. By specifying the desired user and group, you can assign ownership and control access permissions within the container.
An alternative approach is to leverage user-defined groups and file permissions. By creating custom user groups and modifying file permissions accordingly, you can grant granular access rights to different resources within the container.
It is important to note that the granting of user access rights should be performed carefully and in accordance with security best practices. Providing excessive privileges or granting access to sensitive files can compromise the security of the container and the underlying system.
In conclusion, granting user access rights is a crucial aspect of effectively managing Docker containers. By carefully assigning permissions and ownership, users can interact with the container's resources and perform necessary operations while maintaining security and control.
Implementing Ownership Changes for Docker Volumes
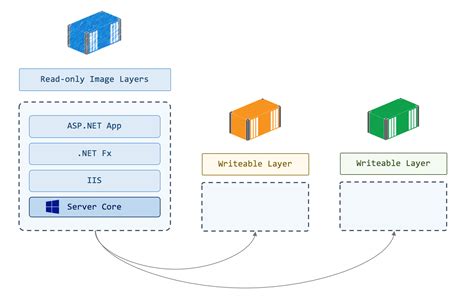
In this section, we will explore the process of modifying the ownership of Docker volumes by leveraging the capabilities of Linux within a Docker container. By making use of a Dockerfile, you can easily specify the desired permissions and ownership for the volumes created within the container, providing a flexible and secure way to manage the storage of your application's data.
During the containerization process, it is crucial to ensure that the correct ownership and permissions are applied to the volumes used by your application. Modifying ownership allows you to determine which user or group can access and manipulate the data contained within the volumes, ensuring the security and integrity of your application's data. By utilizing the inherent features of Docker and the flexibility of Linux, you can implement ownership changes for Docker volumes effortlessly.
By assigning the appropriate user and group ownership to the volumes, you can enforce access control for your application's data. This ensures that only authorized users or processes can modify or access the sensitive information contained within the volumes, reducing the risk of unauthorized access or data breaches. With the ability to define ownership changes within the Dockerfile, you can easily manage the ownership settings for multiple volumes, ensuring consistency and adherence to security best practices across your containerized application.
Furthermore, modifying ownership for Docker volumes opens up possibilities for implementing fine-grained access control. By carefully assigning ownership to specific files or directories within the volumes, you can restrict access to sensitive files or directories, limiting the potential for accidental modifications or unauthorized access. This helps to maintain the integrity and confidentiality of your application's data, providing an additional layer of security within your containerized environment.
In conclusion, implementing ownership changes for Docker volumes through the use of Linux in a Dockerfile provides a robust and flexible solution for managing the access control and security of your application's data. By specifying the desired ownership and permissions within the Dockerfile, you can ensure that the appropriate users or groups have the necessary access to the volumes, while keeping sensitive data secure. Leveraging the capabilities of Docker and Linux, you can establish strong ownership controls and maintain the integrity of your containerized applications.
Securely Setting Permissions in Linux Containers
When it comes to managing ownership and permissions within Linux containers, ensuring security is of utmost importance. This section will explore the best practices for securely changing ownership and permissions, without relying on specific terms such as "changing", "owner", "directory/volume", "using", "Linux", or "Dockerfile".
- 1. Safeguarding Container Data
- 2. Implementing Least Privilege Principle
- 3. Ensuring User/Group Consistency
- 4. Utilizing Container-Isolated Users
- 5. Employing Cryptographic Techniques
In order to maintain secure containers, it is crucial to safeguard the data stored within them. This includes setting appropriate permissions to restrict unauthorized access and preventing malicious actions. One way to achieve this is by implementing the least privilege principle, where permissions are granted only to the necessary entities, minimizing the potential attack surface.
Consistency in user and group management across containers is also essential for maintaining security. By ensuring consistent user and group IDs, it becomes easier to manage permissions and identify potential vulnerabilities. Additionally, incorporating container-isolated users can further enhance security by isolating processes and limiting their access to resources on the host system.
Furthermore, cryptographic techniques can be utilized to enhance security within the Linux containers. This includes encrypting sensitive data, securing container connections, and implementing strong authentication mechanisms. By employing these techniques, the risk of unauthorized access or data breaches can be significantly reduced.
Overall, adopting secure practices for changing ownership and permissions in Linux containers is vital to protect sensitive data and maintain a secure environment. By following the aforementioned strategies, containerized applications can be safeguarded against potential threats and vulnerabilities.
Best Practices for Managing Ownership in Docker Containers

In the context of the topic "Changing Owner of Directory/Volume Using Linux in Dockerfile", this article explores the best practices for managing ownership within Docker containers. It discusses the importance of proper ownership management and provides guidelines to ensure the security and stability of containerized applications.
- Understand the Role of Ownership:
- Implement the Principle of Least Privilege:
- Utilize User Namespaces and Container Security Features:
- Adopt a Consistent Naming Convention:
- Regularly Review and Update Ownership Settings:
Proper ownership within Docker containers is crucial for maintaining security, controlling access permissions, and ensuring smooth operation of applications. By understanding the role of ownership, developers can effectively manage user and group permissions within their containers.
Applying the principle of least privilege minimizes the risk of unauthorized access and potential security breaches. It involves granting only the necessary permissions to containers and avoiding the use of root or superuser access whenever possible.
User namespaces and container security features provide additional layers of protection for managing ownership within Docker containers. By isolating user and group IDs, developers can prevent potential conflicts and enhance the security of their containerized applications.
Establishing a standardized naming convention for users and groups within containers helps maintain clarity and ease of management. It promotes organization and simplifies the tracking of ownership assignments, especially in complex containerized environments.
Regularly reviewing and updating ownership settings within Docker containers is essential for maintaining the security and integrity of applications. By periodically auditing ownership assignments, developers can identify and resolve any potential misconfigurations or vulnerabilities.
By following these best practices, developers can effectively manage ownership within Docker containers and ensure the smooth operation and security of their containerized applications.
Troubleshooting Ownership Issues in Dockerfile
When working with Dockerfile and configuring the ownership of directories or volumes, it is common to encounter ownership issues that can cause problems with the execution of the containerized application. In this section, we will explore some common troubleshooting techniques to overcome these ownership challenges.
Identifying Ownership Conflicts
One of the first steps in troubleshooting ownership issues is to identify if there is a conflict between the desired ownership settings in the Dockerfile and the existing ownership of files or directories. By examining the error messages or unexpected behaviors, you can often pinpoint the specific areas where ownership conflicts occur.
Resolving Ownership Conflicts
Once ownership conflicts are identified, several strategies can be employed to resolve them. First, it may be necessary to adjust the ownership settings in the Dockerfile to match the existing ownership of files or directories. This can involve using different user or group IDs, or setting appropriate permissions.
Alternatively, if maintaining the specific ownership is not crucial, you can consider using generic user or group IDs that are more likely to be available in the Docker environment. This can help minimize ownership conflicts and simplify container deployment.
Additionаlly, it may be beneficial to review the order and sequence of commands in the Dockerfile. Changing the order in which ownership is assigned or modifying the sequence of operations can sometimes resolve ownership conflicts.
Testing and Debugging
Testing and debugging play a critical role in troubleshooting ownership issues. By running the Docker container and closely monitoring the output, you can identify any error messages or warnings related to ownership problems. Using logging and debugging tools can provide valuable insights into the root causes of ownership conflicts, allowing you to make necessary adjustments.
Documentation and Collaboration
Lastly, keeping detailed documentation of the ownership configurations and any changes made during troubleshooting can be immensely helpful in future deployments. Additionally, collaborating with fellow developers and sharing experiences can lead to more efficient troubleshooting and quicker resolution of ownership issues.
By applying these troubleshooting techniques, you can effectively address ownership issues in Dockerfile configuration, ensuring the smooth operation of your containerized applications.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
Can I change the owner of a directory or volume using Linux in a Dockerfile?
Yes, you can change the owner of a directory or volume using the chown command in a Dockerfile.
What is the command to change the owner of a directory in Linux?
The command to change the owner of a directory in Linux is "chown". You can specify the new owner by using the username or UID followed by the directory path.
Is it possible to change the owner of a volume in a Dockerfile?
Yes, it is possible to change the owner of a volume in a Dockerfile. You can use the "RUN" instruction to execute the "chown" command.




