In this article, we explore the method to effortlessly establish a secure and reliable access to private network resources from within a Windows Docker container. By leveraging advanced virtual private network (VPN) technology, Windows users can conveniently connect to remote hosts and take advantage of the vast range of functionalities offered by Docker containers.
Understanding the complexities associated with network accessibility, this guide uncovers the intricacies involved in establishing a seamless network connection, ensuring a seamless experience for Docker container users. Through the use of innovative techniques, we delve into the process of connecting to VPN hosts right from the comfort of your Windows Docker environment.
Explore the optimal approach towards enabling a secure communication channel between the Docker container and remote network hosts. Discover efficient methods to anonymize your network connectivity by leveraging the power of VPN technology. With detailed step-by-step instructions, this article equips you with the necessary knowledge to overcome any potential challenges and seamlessly access remote resources, all within the confines of your Windows-based Docker container.
Understanding VPN (Virtual Private Network) Networks
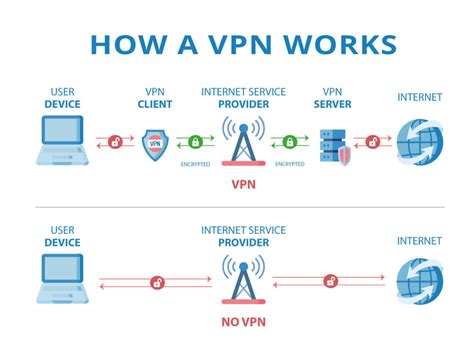
In the realm of secure networking, VPNs play a crucial role in establishing private and encrypted connections between different devices or networks. By leveraging various protocols and cryptographic techniques, VPNs enable users to access remote resources and communicate securely over insecure networks, such as the internet. This section aims to provide a comprehensive understanding of VPN networks and their fundamental principles.
1. Introduction to VPN Networks: Delve into the concept of VPN networks, exploring their functionalities, advantages, and applications across various industries. Highlight the importance of maintaining privacy, confidentiality, and data integrity in today's interconnected world.
2. Types of VPN Networks: Explore the different types of VPN networks available, including remote access VPNs, site-to-site VPNs, and hybrid VPNs. Discuss their key characteristics, use cases, and the underlying technologies that enable secure communication.
- Remote Access VPN: Investigate how remote access VPNs allow users to connect securely to a private network over the internet. Highlight the benefits of using remote access VPNs, such as enabling secure remote work and facilitating access to internal resources.
- Site-to-Site VPN: Examine the functionality of site-to-site VPNs, which establish secure connections between different networks. Discuss how site-to-site VPNs are commonly used to connect multiple branch offices or connect remote networks to a data center.
- Hybrid VPN: Explore the concept of hybrid VPNs, which combine the advantages of remote access and site-to-site VPNs. Explain how hybrid VPNs can provide a flexible and scalable network infrastructure, suitable for diverse organizational needs.
3. VPN Encryption and Protocols: Dive into the encryption methods and protocols employed by VPN networks to ensure confidentiality and secure data transmission. Discuss commonly used encryption algorithms, such as AES and RSA, and explore protocols like OpenVPN, IPSec, and WireGuard.
4. VPN Configurations and Setup: Provide insights into how VPN networks are configured and set up in both client and server environments. Discuss key considerations, such as authentication methods, VPN client configurations, and VPN server deployments.
By understanding the fundamental concepts and components of VPN networks, users can make informed decisions when accessing VPN hosts from Windows Docker container or any other platform.
Exploring the Concept of Virtual Private Network (VPN) and Its Advantages
In today's interconnected world, securing networks and protecting sensitive information has become of utmost importance. One technology that plays a crucial role in this area is the Virtual Private Network (VPN).
At its core, a VPN allows for secure and private communication between different devices over the internet. It creates a virtual tunnel that encrypts and encapsulates data, protecting it from unauthorized access and ensuring its integrity. By utilizing advanced encryption protocols, VPNs enable individuals and organizations to establish secure connections and browse the internet without the fear of being observed or having their data compromised.
One of the primary benefits of using a VPN is the ability to access geographically restricted content. By connecting to VPN servers located in different regions, users can bypass regional restrictions and access websites, streaming services, and online content that may be otherwise unavailable. This allows for a more open and unrestricted online experience, regardless of the user's physical location.
In addition to circumventing censorship and accessing restricted content, VPNs also enhance online privacy. Since all internet traffic is encrypted and routed through the VPN server, the user's IP address is masked, making it difficult for adversaries to track their online activities. This anonymization aspect of VPNs provides individuals with a layer of privacy and security, ensuring that their online identity and information remain protected.
Furthermore, VPNs are commonly used to establish secure connections when accessing public Wi-Fi networks. Public Wi-Fi hotspots are notorious for their lack of security, making them prime targets for hackers and cybercriminals. By connecting to a VPN, users can create a secure tunnel between their devices and the VPN server, encrypting their data and shielding it from potential threats. This significantly reduces the risk of falling victim to identity theft, data breaches, and other malicious activities.
Overall, VPNs offer a range of benefits, from unrestricted access to content and enhanced privacy to improved security when connecting to public networks. Understanding the concept of VPN and its advantages is essential for individuals and organizations looking to safeguard their online activities and protect sensitive information.
Understanding the Importance of VPN Hosts in Enabling Secure Remote Connectivity
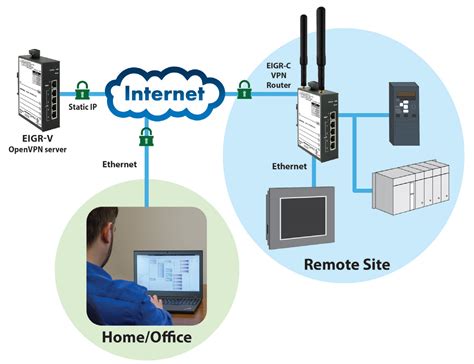
In the realm of remote access, securing network connections has become paramount for organizations. VPN hosts play a crucial role in ensuring the privacy, confidentiality, and integrity of data transmitted between remote locations and corporate networks. By establishing a virtual tunnel through various networks, VPN hosts enable individuals to securely access network resources and services.
Enhancing Privacy and Security: VPN hosts employ encryption protocols to safeguard the confidentiality of sensitive information. They serve as a protective shield against unauthorized access and interception. By encrypting data during transmission, VPN hosts ensure that only authorized users can access the network resources, preventing eavesdropping and data breaches.
Facilitating Remote Connectivity: VPN hosts enable individuals to establish secure connections to remote networks. This remote access capability empowers employees and partners to work from any location, ensuring seamless collaboration and productivity. Moreover, VPN hosts allow remote users to bypass geographical restrictions, leading to unrestricted access to network resources and services.
Enabling Secure Transmission: VPN hosts utilize authentication mechanisms, such as certificates and passwords, to ensure the integrity of transmitted data. By verifying the identities of both the client and the server, VPN hosts prevent the manipulation or tampering of information during transmission. Additionally, VPN hosts deliver data through encrypted tunnels, protecting it from potential threats and ensuring secure transmission.
Protecting against Malicious Activities: VPN hosts come equipped with features that safeguard against malicious activities and intrusions. They offer firewall capabilities, intrusion detection systems, and other security mechanisms that detect and mitigate potential threats. By filtering network traffic and implementing access controls, VPN hosts minimize the risk of unauthorized access and protect the network from potential attacks.
Summary: In summary, VPN hosts play a vital role in ensuring secure remote access by enhancing privacy, facilitating remote connectivity, enabling secure transmission, and protecting against malicious activities. By leveraging encryption, authentication, and security mechanisms, VPN hosts establish a secure tunnel through which individuals can access network resources and services without compromising data integrity and confidentiality.
Introduction to Windows Docker Containers
In this section, we will provide an overview of the concept of Windows Docker containers. Docker containers, which are lightweight, isolated environments, enable developers to package and deploy applications with their dependencies in a consistent and reproducible manner. Windows Docker containers, specifically tailored for Windows-based applications, utilize the Docker engine to run and manage these containers on Windows operating systems.
Windows Docker containers offer a range of benefits for developers and system administrators. Firstly, they provide a flexible, efficient, and portable way to package and distribute applications, allowing for easy deployment across various environments. Secondly, the isolation provided by containers ensures that applications run independently and do not interfere with each other, leading to enhanced stability and security. Additionally, Windows Docker containers offer seamless integration with existing Windows infrastructure and tools, making them an ideal choice for Windows-based development and deployment scenarios.
- Lightweight and Portable: Windows Docker containers allow developers to package applications and their dependencies into self-contained units, which can be easily shared, moved, and deployed across different environments.
- Isolated and Secure: Each Windows Docker container runs in its own isolated environment, ensuring that applications do not affect each other and providing an additional layer of security.
- Consistent and Reproducible: By encapsulating all dependencies within the container, Windows Docker containers provide a consistent and reproducible environment, reducing the chances of unexpected issues during application deployment.
- Integration with Windows Infrastructure: Windows Docker containers seamlessly integrate with existing Windows infrastructure and tools, enabling developers to leverage familiar tools and processes for application development and deployment.
Overall, Windows Docker containers offer a powerful solution for packaging, deploying, and running Windows-based applications. Understanding the fundamentals of Windows Docker containers is crucial for developers and system administrators to take full advantage of this technology and streamline their application development and deployment workflows.
Configuring a Secure Network Connection in Windows Docker Containers
In this section, we will explore the process of setting up a secure network connection within the Windows Docker containers. By implementing a Virtual Private Network (VPN) configuration, users can establish a protected communication channel between their Docker containers and external networks. Through this setup, data transmission can be encrypted and authenticated, enhancing the overall security of their containerized applications.
Establishing Secure Network Connectivity in Windows Docker Containers
The first step in configuring a VPN within a Windows Docker container involves setting up the necessary network security protocols and authentication mechanisms. By implementing standardized encryption algorithms, such as OpenVPN or IPsec, users can ensure that their network connections are secured against unauthorized access and data breaches.
Authentication and Authorization Processes
Once the encryption protocols are in place, users need to configure the authentication and authorization processes within their Docker containers. This ensures that only authorized users or devices can establish a connection to the VPN. By implementing authentication mechanisms such as username/password authentication, digital certificates, or multi-factor authentication, users can add an additional layer of security to their containerized applications.
Routing and Access Control
After securing the network connection and implementing authentication, users need to define the routing and access control policies within their Windows Docker containers. This helps regulate the flow of network traffic and restricts access to specific resources or networks. By configuring proper routing tables and access control lists (ACLs), users can ensure that their containerized applications communicate securely with external hosts via the VPN.
Monitoring and Auditing
Lastly, it is crucial to establish monitoring and auditing mechanisms within the Windows Docker containers to track any potential security breaches or suspicious activities. By implementing logging and monitoring tools, users can gain insights into the network traffic and detect any anomalies or unauthorized access attempts. This enables proactive identification and mitigation of security threats, ensuring a robust and secure networking environment for containerized applications.
Easy Installation and Configuration of VPN for Windows Containers
In this step-by-step guide, we will walk you through the process of installing and setting up a VPN on your Windows containers. By following these instructions, you'll learn how to securely connect your containers to a VPN network, enabling secure communication and data transfer.
Step 1: Preparing the Environment
Before we begin the installation process, it is essential to ensure that your Windows containers are properly set up and meet the necessary requirements for VPN connectivity. This includes ensuring that your containers have the required network interfaces and configurations.
Step 2: Installing the VPN Client
Next, we will guide you through the process of installing the VPN client software on your Windows containers. This software will enable your containers to establish a secure connection with the VPN server.
Step 3: Configuring VPN Settings
Once the VPN client is installed, we will show you how to configure the VPN settings for your containers. This includes specifying the VPN server address, authentication methods, and other relevant parameters.
Step 4: Establishing the VPN Connection
With the client software and settings in place, we will demonstrate how to establish a VPN connection from your Windows containers. This step will enable your containers to securely communicate with other devices and access resources within the VPN network.
Step 5: Verifying VPN Connectivity
Finally, we will provide you with instructions on how to verify that your Windows containers have successfully established a VPN connection. We will guide you through various methods to confirm connectivity and troubleshoot any potential issues.
By following this comprehensive guide, you'll gain the knowledge and skills necessary to install and set up a VPN on your Windows containers. This will enable secure access to resources within your VPN network, ensuring the privacy and integrity of your containerized applications and data.
Common Challenges and Troubleshooting Tips
In this section, we will explore the commonly encountered difficulties and provide useful solutions to overcome them when attempting to establish connectivity between a Windows Docker container and VPN hosts. By understanding these challenges and implementing the troubleshooting tips, users can enhance their experience and ensure a smooth connection.
- Networking Configuration:
- Firewall and Security:
- DNS Resolution:
- VPN Client Compatibility:
- Log Analysis and Debugging:
- Updating Software and Dependencies:
One of the primary challenges is configuring the networking settings correctly to enable communication between the Docker container and the VPN hosts. This involves configuring the virtual network interface and ensuring proper routing to establish a seamless connection.
Firewall settings and security policies can often interfere with VPN connectivity. It is crucial to identify and resolve any firewall or security-related issues such as blocked ports, restricted access, or security policies that may hinder the connection between the Docker container and the VPN hosts.
Incorrect DNS resolution can lead to connection failures when accessing VPN hosts. Troubleshooting DNS resolution issues, such as configuring the correct DNS server settings or resolving DNS conflicts, can help resolve this challenge and enable successful communication.
Compatibility issues between the VPN client and the Docker container can hinder connectivity. Verifying the compatibility of the VPN client software with the specific Docker container environment can help avoid any potential compatibility-related challenges.
When facing difficulties in accessing VPN hosts from a Windows Docker container, analyzing logs and using debugging tools can provide valuable insights. Understanding log entries, error messages, and tracing network traffic can help pinpoint the root causes and facilitate troubleshooting.
Outdated software versions or missing dependencies can impact VPN connectivity in Docker containers. Regularly updating the software and dependencies, including the VPN client, Docker, operating system, and any relevant network components, can help mitigate compatibility and performance issues.
By addressing these common challenges and implementing the troubleshooting tips, users can effectively overcome hurdles in establishing connectivity between a Windows Docker container and VPN hosts. Resolving these issues ensures a stable and secure connection that enables efficient communication and data transfer.
Connecting Containers with the Network Infrastructure: Techniques and Resources
In this section, we will explore the various techniques and resources that can be employed to establish connectivity between containers and the network infrastructure they rely on. By establishing a seamless connection, containers can access VPN hosts and leverage their capabilities, ensuring secure and reliable communication.
| Technique | Description | Advantages |
|---|---|---|
| Container Networking Interface (CNI) | CNI provides a standardized approach for connecting containers to the network, enabling seamless integration with VPN hosts. By utilizing CNI plugins, containers can leverage the VPN infrastructure and securely communicate with external resources. | 1. Easy integration with existing VPN setups 2. Simplified deployment and management 3. Flexible configuration options |
| Host-Based VPN Forwarding | This approach involves configuring the host machine to forward VPN traffic to the containers. By utilizing network address translation (NAT) techniques, containers can receive VPN traffic and respond accordingly, enabling effective communication with VPN hosts. | 1. Provides direct VPN access to containers 2. Minimal configuration required 3. Efficient utilization of host resources |
| Service Mesh Integration | By integrating service mesh technologies like Istio, containers can establish secure and reliable connections with VPN hosts. Service mesh solutions provide features such as traffic encryption, load balancing, and observability, enhancing the overall connectivity experience. | 1. Enhanced security through mutual TLS authentication 2. Advanced traffic management capabilities 3. Simplified operation and monitoring |
By leveraging these techniques and resources, containers can seamlessly connect with VPN hosts and unlock the full potential of their network infrastructure. Each approach offers unique advantages, allowing organizations to choose the most suitable method based on their specific requirements and existing infrastructure.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
Can I access VPN hosts from a Windows Docker container?
Yes, it is possible to access VPN hosts from a Windows Docker container.
How can I access VPN hosts from a Windows Docker container?
To access VPN hosts from a Windows Docker container, you need to configure the container to use the host's network stack and DNS resolver. This can be done by using the "--network=host" flag when running the container and specifying the host's DNS resolver.
Is it necessary to have a VPN client installed inside the Docker container to access VPN hosts?
No, it is not necessary to have a VPN client installed inside the Docker container. By configuring the container to use the host's network stack, the container can directly access the VPN hosts.
Will accessing VPN hosts from a Windows Docker container impact the host's VPN connection?
No, accessing VPN hosts from a Windows Docker container will not impact the host's VPN connection. The container will create a separate network stack and will not interfere with the host's VPN connection.
Are there any limitations or considerations when accessing VPN hosts from a Windows Docker container?
Yes, there are a few limitations and considerations. The host's firewall configuration may need to be adjusted to allow the container to access the VPN hosts. Additionally, the container's network configuration needs to be carefully set up to ensure proper connectivity to the VPN hosts.
Can I access VPN hosts from a Windows Docker container?
Yes, it is possible to access VPN hosts from a Windows Docker container by following the necessary steps.




