In the vast realm of digital security, the Linux kernel harbors a hidden treasure trove of cryptographic capabilities, waiting to be utilized by Docker containers. Imagine a world where secure encryption algorithms dance at your command, safeguarding sensitive data within your application. This comprehensive guide aims to shed light on the intricacies of accessing the cryptographic API of the Linux kernel from Docker, offering developers and security enthusiasts a roadmap towards harnessing the power of secure encryption.
Beneath the surface, the Linux kernel houses a labyrinth of interwoven algorithms and protocols, working tirelessly to ensure the privacy and integrity of data. However, the potential of this cryptographic API often remains untapped, confined by the limited knowledge and unfamiliarity of developers. This guide seeks to demystify the intricate inner workings of the Linux kernel, granting you the tools to navigate this terrain and harness the cryptographic prowess hidden within.
With Docker revolutionizing the world of containerization, the synergy achieved by incorporating Linux kernel's cryptographic capabilities adds another layer of security to your applications. By seamlessly integrating Docker with the Linux kernel's cryptographic API, developers gain access to a plethora of encryption algorithms, key management systems, and secure communication protocols. This guide aims to bridge the gap between Docker and the Linux kernel, empowering you to securely protect your data and communications within containerized environments.
Embark on this journey with us as we unravel the secrets of the Linux kernel's cryptographic API. From understanding the fundamentals of encryption algorithms to exploring the intricacies of key management, this guide equips you with comprehensive knowledge and practical insights. Harness the power of secure encryption within Docker containers, ensuring that your application's sensitive data remains impervious to prying eyes and malicious hands.
Introduction to Docker: Understanding the Concept
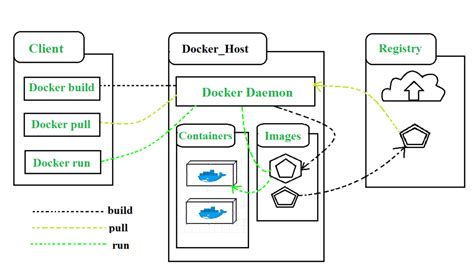
In this section, we will discuss the fundamental concept of Docker, providing a clear understanding of its purpose and functionality. Docker is a popular and widely-used platform that allows for the creation, deployment, and management of containerized applications. Containers provide a lightweight and isolated environment, enabling applications to run consistently across different operating systems and infrastructure.
When it comes to software development and deployment, Docker offers a range of benefits. These include improved scalability, increased flexibility, and simplified management of applications. By utilizing Docker, developers can package their applications along with all the necessary dependencies and configurations, making them easily portable across different environments.
Docker provides a streamlined process for building and distributing applications, allowing for efficient collaboration among development teams. With Docker, developers can create reproducible environments, ensuring that applications work seamlessly across different development and production stages.
- Efficiency: Docker containers run with minimal overhead, as they utilize shared operating systems and resources.
- Portability: Docker containers can be easily moved and deployed across different machines and environments, ensuring consistency and ease of deployment.
- Scalability: Docker allows for the seamless scaling of applications, both vertically and horizontally, in response to changing demands.
- Isolation: Docker containers provide a higher level of security and isolation, ensuring that applications do not interfere with each other or the underlying infrastructure.
- Speed: Docker enables developers to rapidly build, test, and deploy applications, reducing the time-to-market significantly.
By leveraging the power of Docker, developers can focus on writing code without worrying about the intricate details of the underlying infrastructure. This section serves as a solid introduction to the core concepts of Docker, providing a foundation for the subsequent discussions on accessing the cryptographic API of the Linux Kernel from Docker containers.
Overview of Linux Kernel's Cryptographic API
In this section, we will provide a comprehensive overview of the underlying cryptographic capabilities offered by the Linux kernel. By exploring the foundational elements of the Linux kernel's cryptographic API, we can gain a deep understanding of its functionality and how it can be leveraged for various security-related tasks.
Firstly, we will discuss the fundamental concepts and principles behind the Linux kernel's cryptographic API. We will explore the key components and building blocks that enable developers to perform cryptographic operations effortlessly and securely within the kernel environment.
We will delve into the various algorithms and protocols supported by the Linux kernel's cryptographic API. From symmetric encryption algorithms like AES and DES to asymmetric encryption algorithms such as RSA and ECC, the Linux kernel's cryptographic API offers a wide range of options to developers.
Furthermore, we will explore the different hashing algorithms available within the Linux kernel's cryptographic API. We will discuss the advantages and use cases of popular hashing algorithms like SHA-256 and MD5, highlighting their role in ensuring data integrity and verifying the authenticity of digital signatures.
Additionally, we will examine the concept of digital signatures and how they can be leveraged within the Linux kernel's cryptographic API. We will explore the various signature algorithms supported, such as DSA and ECDSA, and discuss their significance in guaranteeing the authenticity and integrity of data.
Lastly, we will touch upon the topic of random number generation within the Linux kernel's cryptographic API. We will discuss the importance of robust and unpredictable random number generation for cryptographic operations and highlight the methods and mechanisms available within the kernel for achieving this.
By the end of this section, readers will have a solid understanding of the Linux kernel's cryptographic API and its capabilities. This knowledge will serve as a foundation for the subsequent sections, where we will explore the process of accessing and utilizing this powerful API from within a Docker environment.
Accessing the Powerful Encryption Capabilities of Linux Kernel within Docker Environment
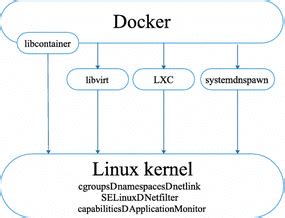
In this section, we will explore the proficient techniques to leverage the robust encryption functionalities offered by the Linux Kernel while operating within a Docker environment.
By harnessing the unwavering strength of the Linux Kernel's cryptographic capabilities, we can enhance the security and confidentiality of data within Docker containers. This section will provide comprehensive insights into the methodologies and best practices required to efficiently access these encryption features.
- Introduction to Linux Kernel Encryption: Gain an understanding of the diverse range of encryption algorithms, hashing functions, and cryptographic protocols supported by the Linux Kernel. Discover how these features can be harnessed to safeguard sensitive information within Docker containers.
- Configuring Docker for Enhanced Cryptographic Access: Dive into the intricacies of configuring Docker to enable seamless integration with the Linux Kernel's powerful encryption capabilities. Find out how to optimize Docker settings to harness the full potential of cryptographic functionalities.
- Usage Examples and Code Walkthroughs: Explore practical examples and code walkthroughs that demonstrate how to access and utilize the advanced cryptographic API of the Linux Kernel from within Docker containers. Learn how to incorporate encryption functionalities seamlessly into Dockerized applications.
- Best Practices for Securing Dockerized Environments: Delve into the best practices for maintaining robust security and mitigating potential vulnerabilities when accessing the cryptographic API within a Docker environment. Discover effective strategies for protecting cryptographic keys and ensuring the integrity of encrypted data.
- Performance Considerations and Benchmarking: Examine the performance impact of accessing the cryptographic API within Docker containers. Learn how to benchmark and fine-tune encryption operations to optimize performance without compromising security.
By following the guidelines and recommendations presented in this section, you will be equipped with the knowledge and skills necessary to effectively utilize the cryptographic capabilities of the Linux Kernel within Docker environments, bolstering the security of your applications and protecting sensitive data.
Exploring Use Cases and Applications
In this section, we will delve into various scenarios where the utilization of the cryptographic features provided by the Linux Kernel and Docker can be of immense value. By harnessing the power of cryptography, developers and organizations can enhance the security, privacy, and integrity of their applications and systems.
- Secure Communication: Cryptographic APIs can facilitate secure communication between different containers, services, or nodes within a Docker environment. By encrypting data at the source and decrypting it at the destination, sensitive information can be safeguarded from unauthorized access or interception.
- Data Protection: With the help of cryptographic techniques, Docker containers can ensure the confidentiality and integrity of data stored within them. By employing encryption algorithms, sensitive information can be protected both at rest and in transit, reducing the risk of data breaches and unauthorized modifications.
- Key Management: The cryptographic API of the Linux Kernel enables Docker containers to generate, store, and manage encryption keys securely. This capability allows for the seamless integration of cryptographic operations within containerized applications and ensures robust key management practices.
- Secure Authentication and Authorization: Through cryptographic APIs, Docker containers can enforce strong authentication and authorization mechanisms. By utilizing digital signatures, certificates, and authentication protocols, access to containerized services and resources can be tightly controlled, minimizing the risk of unauthorized access.
- Compliance and Regulatory Requirements: Cryptographic APIs in Linux Kernel and Docker can help organizations meet compliance and regulatory requirements, such as GDPR or HIPAA. By employing encryption at the data layer, organizations can enhance data protection, privacy, and meet the stringent security standards imposed by regulatory bodies.
- Blockchain and Distributed Systems: Cryptographic APIs play a crucial role in securing blockchain networks and distributed systems powered by Docker. By leveraging cryptographic algorithms and techniques, blockchain transactions can be validated, tamper-proof ledgers can be maintained, and the decentralized nature of these systems can be preserved.
These are just a few examples of the vast range of use cases and applications that can benefit from accessing the cryptographic API of the Linux Kernel within a Docker environment. By harnessing the power of cryptography, developers and organizations can ensure the security and resilience of their systems in an increasingly interconnected and digitally-driven world.
Limitations and Considerations

When working with the cryptographic functionalities of the Linux Kernel through Docker, there are certain limitations and considerations that need to be taken into account. Understanding these limitations can help ensure the proper utilization and integration of cryptographic APIs within a Docker environment.
Compatibility One important consideration is the compatibility between the cryptographic APIs and the underlying Linux Kernel version. Different versions of the Linux Kernel may have varying levels of support for cryptographic algorithms and protocols. It is important to ensure that the chosen cryptographic API is compatible with the specific Linux Kernel version being used. |
Resource Consumption Another limitation to consider is the potential impact on resource consumption when utilizing cryptographic functionalities within Docker. Cryptographic operations can be computationally intensive and may require significant system resources such as CPU, memory, and disk space. It is essential to monitor and allocate sufficient resources to ensure optimal performance and avoid potential bottlenecks. |
Security Considerations Security is of paramount importance when working with cryptographic APIs. It is crucial to ensure that the cryptographic libraries and algorithms used within Docker are secure and have been thoroughly audited for vulnerabilities. Additionally, proper key management practices must be implemented to protect sensitive cryptographic keys and ensure their confidentiality, integrity, and availability. |
Performance Trade-offs There may be trade-offs between performance and security when utilizing cryptographic APIs within Docker. Some cryptographic algorithms may offer stronger security but at the cost of increased computation time. Careful consideration must be given to strike a balance between performance and desired levels of security, depending on the specific requirements and constraints of the application. |
Documentation and Support Lastly, it is important to consider the availability of comprehensive documentation and support for the chosen cryptographic API. Access to clear and up-to-date documentation, as well as a vibrant community or support channels, can greatly aid in the successful integration and troubleshooting of cryptographic functionalities within a Docker environment. |
Nvidia CUDA in 100 Seconds
Nvidia CUDA in 100 Seconds 来自Fireship 1,031,356次观看 2个月前 3分钟13秒钟
100+ Docker Concepts you Need to Know
100+ Docker Concepts you Need to Know 来自Fireship 722,752次观看 1个月前 8分钟28秒钟
FAQ
How can I access the Cryptographic API of Linux Kernel from Docker?
To access the Cryptographic API of Linux Kernel from Docker, you need to install the necessary cryptographic libraries and tools, such as OpenSSL, within your Docker container. You can then use these libraries to interact with the Kernel's Cryptographic API and perform various cryptographic operations.
What are the benefits of accessing the Cryptographic API of Linux Kernel from Docker?
Accessing the Cryptographic API of Linux Kernel from Docker offers several benefits. Firstly, it provides a secure environment for running cryptographic operations within isolated containers. This helps protect sensitive information and prevents unauthorized access. Additionally, using Docker allows for easier management and deployment of cryptographic applications, as containers can be easily scaled, updated, and distributed.
Are there any limitations or considerations when accessing the Cryptographic API of Linux Kernel from Docker?
Yes, there are a few limitations and considerations to keep in mind when accessing the Cryptographic API of Linux Kernel from Docker. Firstly, ensure that the necessary cryptographic libraries and tools are installed within your Docker container. Additionally, be aware that running cryptographic operations within containers introduces some performance overhead due to containerization. It's also important to properly secure the containerized environment and regularly update the underlying Docker images to mitigate any potential security vulnerabilities.




