In the ever-evolving landscape of software development, the need for streamlined and efficient deployment processes has become paramount. As organizations strive to stay ahead in the competitive market, traditional methods of application deployment in a Linux environment have displayed limitations. However, a remarkable solution emerged, revolutionizing the way software is deployed: the ingenious concept of encapsulation.
With the advent of this breakthrough technology, software encapsulation is achieved through the utilization of specialized entities that seamlessly integrate within the Linux ecosystem. These entities, known for their agility and adaptability, revolutionize the way applications are deployed, empowering organizations with unmatched flexibility and efficiency.
In this article, we delve into the unparalleled potential of leveraging cutting-edge encapsulation techniques to deploy software in a Linux environment, uncovering how this paradigm shift is reshaping the software development landscape. Through a comprehensive exploration of the benefits and advantages, we aim to shed light on the transformative power that encapsulation brings to the table.
Understanding the Fundamentals and Advantages of Docker in an Operating System Environment

In this section, we will explore the core concepts and benefits of utilizing Docker within the context of an operating system setup. By delving into the fundamental principles and advantages of this innovative technology, we can gain a deeper understanding of how Docker optimizes the management and deployment of applications.
| Concept | Description |
| Isolation | The ability of Docker to isolate applications and their dependencies ensures that they operate independently, preventing conflicts and compatibility issues. |
| Portability | Docker's portability allows applications and their dependencies to be packaged into standardized containers, enabling seamless deployment across various operating systems and environments. |
| Scalability | With Docker, applications can be easily scaled up or down, allowing for efficient resource utilization and the ability to adapt to changing workloads. |
| Efficiency | The lightweight nature of Docker containers ensures minimal resource usage, resulting in improved efficiency and reduced overhead. |
| Flexibility | Docker's flexibility enables developers to use a wide range of programming languages and frameworks, providing greater choice and compatibility. |
| Reproducibility | The ability to reproduce and share Docker images allows for consistent deployments and collaboration among team members, fostering a streamlined development process. |
By comprehending the core concepts outlined above and recognizing the advantages they bring, we can fully grasp the significance of Docker within the realm of operating system environments. Embracing Docker's power allows for enhanced application management and deployment, ultimately leading to increased efficiency and productivity.
Simplifying Application Deployment in Linux with Docker Containers
In the realm of Linux-based application deployment, Docker containers have emerged as a powerful and efficient solution. By encapsulating applications and their dependencies into self-contained units, Docker provides a simplified and lightweight alternative to traditional deployment methods.
With Docker, the process of deploying and managing applications becomes more streamlined and efficient. Rather than dealing with complex and time-consuming setups, Docker containers offer a standardized approach to application deployment in the Linux environment.
By leveraging the versatility of Docker, developers can package their applications along with the necessary dependencies and configurations, making it easier to deploy and run them on any Linux system. This simplification of the deployment process enables faster and more consistent application delivery, reducing the risk of compatibility issues and improving overall system stability.
Furthermore, the use of Docker containers in Linux environments allows for greater scalability and resource optimization. Containers can be easily replicated and scaled horizontally, enabling applications to handle increased workloads without the need for significant infrastructure changes.
In summary, Docker containers provide a means to simplify the deployment of applications in Linux environments. By encapsulating applications, dependencies, and configurations into self-contained units, Docker simplifies the deployment process, enhances scalability, and improves system stability. Embracing Docker in Linux-based application deployment architectures can help streamline the development and deployment cycle, ultimately leading to more efficient and reliable application delivery.
A Step-by-Step Guide to Running and Managing Docker Containers on Linux Servers
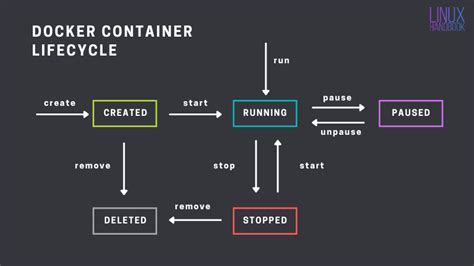
Enhance your productivity by mastering the efficient deployment and management of containerized applications on Linux servers. This comprehensive guide will walk you through the step-by-step process, providing you with the knowledge and skills needed to effortlessly run and manage Docker containers in a Linux server environment.
Enhancing Security and Isolation in a Linux Setting with Dockerized Containers
In order to ensure the highest level of security and isolation within a Linux environment, leveraging the power and flexibility of Docker containers can prove to be a valuable approach. By implementing robust security measures and establishing isolation boundaries, organizations can enhance protection against potential threats and minimize the risk of compromising sensitive data or system resources. This section explores various strategies and techniques for reinforcing security and isolation when utilizing Docker containers in a Linux setting.
Ensuring the Security of Docker Deployments in a Linux Environment: Essential Features and Recommendations

As organizations increasingly adopt containers as a means of running and managing their applications, it becomes crucial to understand the key aspects related to securing these deployments in a Linux environment. Achieving robust security is essential to protect sensitive data, prevent unauthorized access, and ensure the integrity and availability of Docker containers.
In this section, we will delve into the core features and best practices that can help organizations mitigate security risks while leveraging the power and flexibility of Docker deployments. By implementing these measures, businesses can enhance the overall security posture of their containerized environments and establish a solid foundation for safe and reliable operations.
1. Isolating Containerized Applications
One of the fundamental principles in securing Docker deployments involves strong isolation of containerized applications. By employing various isolation techniques, organizations can ensure that each container operates independently, creating a barrier against potential threats and vulnerabilities. This section will explore different methods, such as namespaces and cgroups, that enforce strict boundaries for containers, preventing unauthorized access and unauthorized communication.
2. Implementing Container Image Security
The security of the container image plays a critical role in the overall security of Docker deployments. This aspect encompasses various considerations, including ensuring the authenticity and integrity of container images, scanning for vulnerabilities, and regularly patching and updating them. We will discuss image signing, vulnerability scanning tools, and best practices for securing container images to safeguard against potential security breaches.
3. Controlling Access and Privileges
Proper access control measures are essential in limiting unauthorized access and minimizing potential security risks. This section will explore different techniques for granting and managing user privileges within Docker deployments, including user namespaces, role-based access control (RBAC), and least privilege principles. By carefully controlling access and privileges, organizations can minimize the attack surface and mitigate the impact of potential security breaches.
4. Monitoring and Logging
Effective monitoring and logging are crucial for identifying and responding to security incidents promptly. This section will discuss the importance of adopting monitoring solutions and logging mechanisms within Docker deployments. We will explore monitoring tools, log management strategies, and the utilization of centralized logging platforms to gain real-time insights into container activities, detect anomalies, and proactively address potential security threats.
5. Network Security and Segmentation
Securing the network environment in which Docker containers operate is vital to protect sensitive data and ensure secure communication. In this section, we will examine various networking features and best practices, including network segmentation, firewall rules, and the utilization of secure overlay networks. By implementing network security measures, organizations can establish secure communication channels between containers and limit potential exposure to external threats.
6. Continuous Security Testing and Auditing
Ensuring the ongoing security of Docker deployments requires regular testing, vulnerability assessments, and audits. This section will explore the importance of continuous security testing and auditing practices, including penetration testing, vulnerability scanning, and compliance audits. By incorporating these processes into the development and deployment lifecycle, organizations can identify and address security vulnerabilities proactively and maintain a robust security posture.
By adopting the key features and best practices discussed in this section, organizations can strengthen the security of their Docker deployments in a Linux environment, mitigating risks, protecting sensitive data, and ensuring the smooth and secure operation of containerized applications.
Never install locally
Never install locally by Coderized 1,600,972 views 1 year ago 5 minutes, 45 seconds
Docker Tutorial for Beginners
Docker Tutorial for Beginners by Programming with Mosh 2,438,039 views 3 years ago 56 minutes
FAQ
What is a Docker container?
A Docker container is a lightweight, standalone, executable package that includes everything needed to run a piece of software, including the code, a runtime, libraries, environment variables, and dependencies.
How does Docker work in a Linux environment?
Docker leverages Linux kernel features, such as namespaces and control groups, to provide a lightweight virtualization solution where containers share the same kernel as the host system. This allows for efficient resource utilization and isolation of applications.
What are the advantages of deploying Docker containers in a Linux environment?
Deploying Docker containers in a Linux environment offers several advantages, such as enhanced performance due to shared kernel resources, better resource utilization, simplified deployment process, and compatibility with a vast range of Linux distributions.
Can Docker containers be deployed in a non-Linux environment?
Yes, Docker containers can be deployed in non-Linux environments as well. Docker provides support for different operating systems, including Windows and macOS, by utilizing virtualization technologies specific to each platform.
Are there any security concerns when deploying Docker containers in a Linux environment?
While Docker containers provide isolation, security concerns may arise if proper precautions are not taken. It is important to secure the host system, regularly update Docker images and container runtimes, use container security features, and apply best practices for securing Linux environments.




